The Bleeping Computer forum published master keys for decrypting data affected by Maze, Egregor and Sekhmet ransomware attacks. Apparently, the keys were “leaked” by one of the developers of the malware.
Journalists remind that the Maze ransomware has been active since May 2019 and quickly gained wide popularity, as its operators first came up with the idea of using the “double extortion” tactic. Then the hackers began not only to encrypt the data of their victims, but also began to publish files stolen from the attacked companies, if they refused to pay. Maze operators set up a dedicated website for these leaks, and other groups soon followed their example, including Sodinokibi, DopplePaymer, Clop, Sekhmet, Nephilim, Mespinoza, and Netwalker.
When Maze announced its closure in October 2020, the Egregor ransomware entered the scene, which was basically just a rebrand of Maze. However, it did not last long, as soon the Ukrainian authorities arrested some of the criminals associated with it.
The Sekhmet ransomware stands a little apart on this list, as it appeared in March 2020, when Maze was still active.
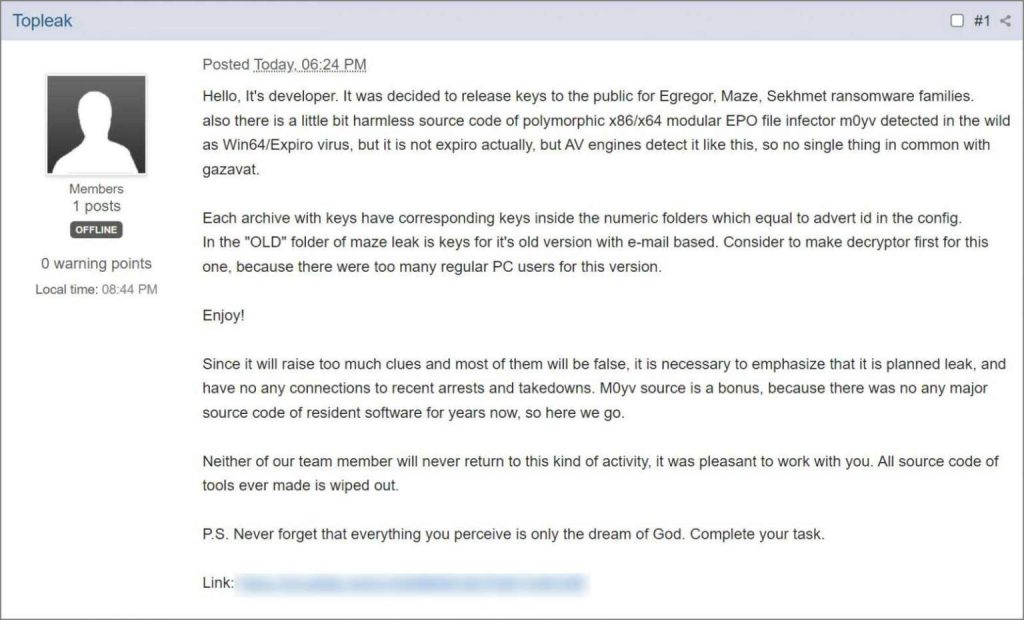
Bleeping Computer writes that the master keys were posted on the forum by a user named Topleak, who claims to have had a hand in the development of all three malware. At the same time, the hacker writes that this is a “planned leak” that has nothing to do with the recent law enforcement operations that led to the seizure of servers and the arrests of “partners” of various extortion groups.
Topleak also emphasized that in the future, none of the members of his hack group will return to the development of ransomware, and they generally destroyed all their source codes.
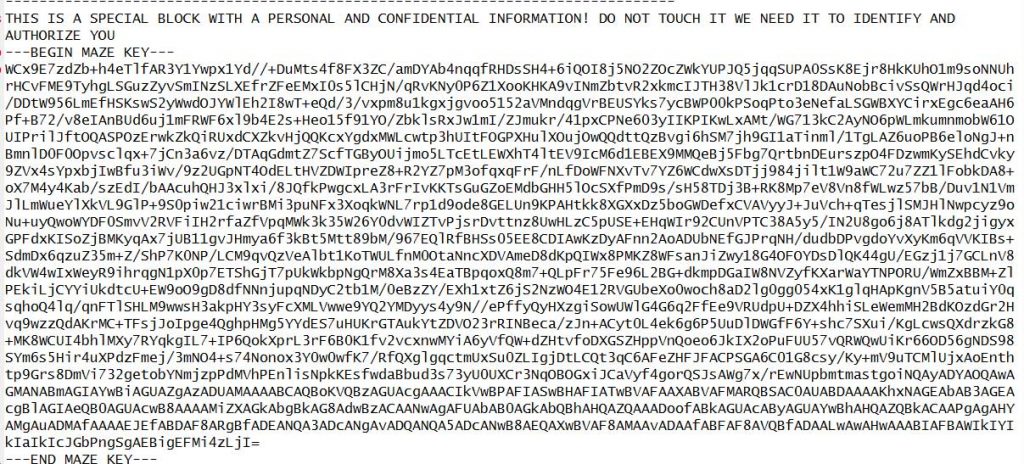
The message is accompanied by a 7zip file with four archives, which contain the decryption keys for Maze, Egregor and Sekhmet, as well as the source code of the M0yv malware, which the hacker called a bonus.
The keys provided by Topleak have already been checked by information security experts Michael Gillespie and Fabian Vosar from Emsisoft, confirming that they can indeed be used to decrypt files.
Emsisoft has already released its own free decryption tool that allows victims of Maze, Egregor and Sekhmet (who have been storing the affected files all this time) to recover their data. In order to use this utility, victims will need a ransom note created during the attack, as it contains the encrypted key needed to “rescue” the files.
Let me remind you that we wrote that Free decryptor for BlackByte ransomware was published, and that Experts linked BlackCat (ALPHV) ransomware to BlackMatter and DarkSide groups.