Google Project Zero specialists presented a report according to which software vendors began to fix 0-day vulnerabilities faster. For example, last year organizations needed less time than in previous years to fix 0-day vulnerabilities discovered by experts.
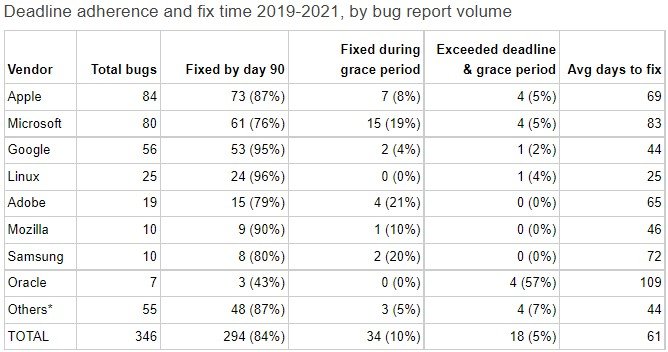
On average, companies took 52 days to fix bugs, while three years ago they needed an average of 80 days. Thus, almost all vendors fixed the vulnerabilities within the industry standard of 90 days.
According to statistics collected for 2019-2021 and based on 376 zero-day vulnerabilities discovered by Google Project Zero experts, 26% of the problems related to Microsoft products, 23% to Apple and 16% to Google. That is, the three software giants accounted for 65% of all detected problems, and, according to experts, this well reflects the complexity and volume of their software products, which inevitably have “white spots” that even numerous security engineers miss.
Overall, the report named Linux, Mozilla, and Google as the best in terms of timely release of patches, while Oracle, Microsoft, and Samsung were named as the worst.
Recall, by the way, that we wrote that 0-day vulnerability remained unpatched for 2 years due to Microsoft bug bounty issues.
In the highly competitive field of mobile OS, iOS and Android go hand in hand: the former has an average bug fix time of 70 days, while the latter has 72 days.
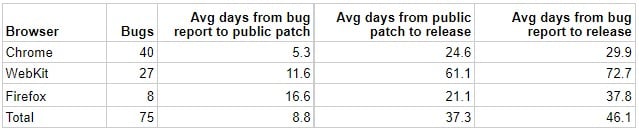
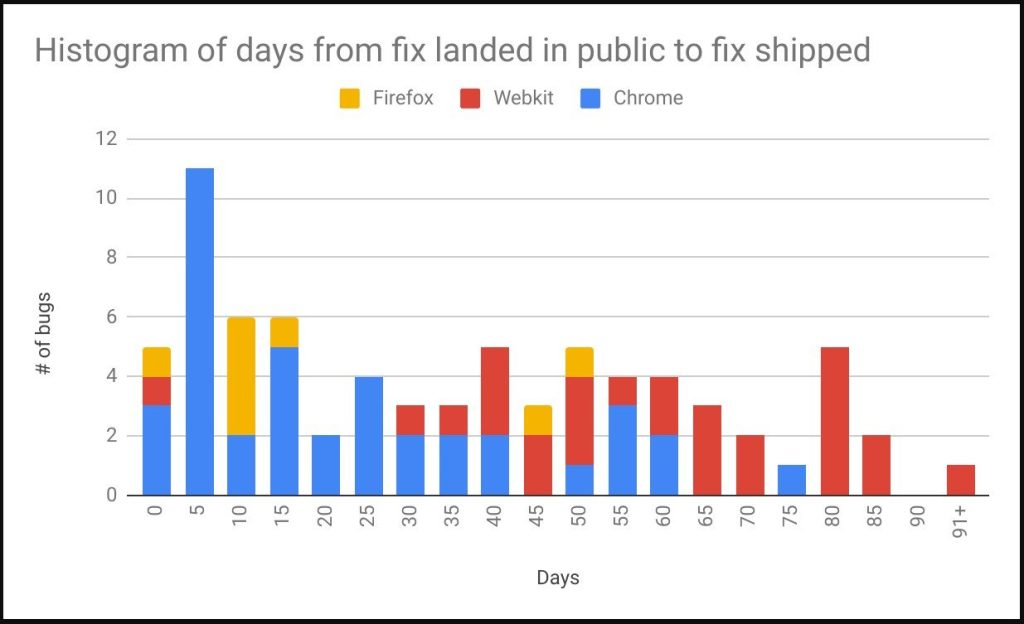
In the browser category, Chrome outperforms all competitors with an average bug fix period of 29.9 days, while Firefox comes in second with 37.8 days. Apple, in third place, took twice as long to fix bugs in WebKit, taking an average of 72.7 days.
Google Project Zero experts explain:
You might also be interested in reading what Google says that a quarter of all 0-day vulnerabilities are new variations of old problems.
READ ALSO: Zero Day Attacks – How To Prevent Them? What does a zero day attack mean? Or is there a way to avoid this danger?