Zero-day vulnerability are the real mess of a modern cybersecurity world. You may have a perfect protection system established in your network, and your employees may be warned and ready to react properly if something goes wrong, but that still is not enough to say that a zero-day threat is avoided. So is there a reason to create any kind of cybersecurity shield? What is the zero-day attack meaning? Or is there a way to avoid this danger? Let’s figure it out together.
What is a Zero-Day Vulnerability?
And so, how can you describe the zero-day attack definition? It is a vulnerability that has never been detected yet. Zero-day attack exists, but no one expects them, either as it’s used for malware deployment. Any application may be the potential attack surface, hence, there is no reason to build a trusted lineup of any sort. Such a situation looks like a nightmare for any cybersecurity analyst, however, for most people who work in this industry that just adds to the excitement.
Let’s have a short reference to the definition of vulnerability (and zero-day vulnerability). It is the undeclared function in the program or the operating system that allows the attacker to execute his code in more beneficial ways. Primarily, the exploits that are used by crooks the most are ones that provide remote code execution and escalation of privileges. Such actions usually make it possible for cybercriminals to do whatever they want in the infected environment. Since it assumes the use of advanced software, the majority of attacks committed with the use of exploits is done against corporations – just because they have much more valuable stuff.
Zero-day attack vulnerabilities never appear out of the blue. Developers do their best to make their programs work well. Nonetheless, a well-working program solution does not always mean one that has no vulnerabilities. Besides the ones that are known by the vendor, there are some that are still present but have not been uncovered. They may be uncovered by cybercriminals, as well as by analysts who review the application. Special outsource users, called bug hunters, also work on uncovering the vulnerabilities present in a certain product. Such initiatives are paid generously, so it is a good way to earn money. But there are still a lot of advanced users who decide to apply those tricks for revenue.
How are zero-day vulnerabilities used?
Since no one (besides the crook who discovered it) knows about that breach, it is pretty easy to apply it if we are talking about the avoidance of any alarms and attention. Even some of the EDR solutions make a mistake by passing the actions from well-known programs like legit, without the thought that this exact activity may be malicious. That’s why it is better to use an endpoint zero-day attack protection application.
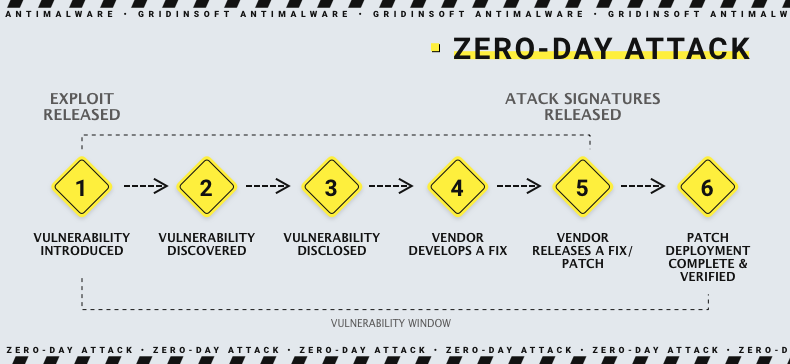
Any vulnerability needs a way to be used, and zero-day vulnerabilities are not single. Same as with any other exploit, crooks create an exploit malware that opens that breach and executes the payload with advanced privileges. For the breaches that allow escalation of privileges, there is the other method. Crooks just make another account in your system, which has administrator privileges, and hide it from your sight. Therefore, they get the ability to run anything with admin privileges at any time. Such a step is quite popular when the APT is deployed.
Why Zero-day Vulnerability is Dangerous?
Of course, like any other exploits, zero-day ones carry tremendous danger, wherever it is used. Using any of the deployment consequences, they provide themselves full control over one of the computers in the network and then expand it to the whole network. The final target of threat actors is your domain controller – they likely know that you have something you don’t want to be published. Crooks may even break into your network without interacting with your files – but they can ask you for payment to keep the fact of the breach in secret. Such cunning guys often call themselves postpaid pen-testers.
Nonetheless, not all crooks may be so noble. Usually, they will deploy ransomware, spyware, or both things simultaneously – to make it impossible for you to reach your data without paying them. Ransomware developers work a lot at making a compound malware that has both data stealing and ciphering modules – such a cadaver is just a nuke for sensitive data. They will also ask you to pay two separate ransoms – one for data decryption and the other for keeping the leaked data in secret. Still, nobody stops them from taking both ransoms, publishing the stolen data, and disappearing without the decryption key. Fortunately, such situations are pretty rare.
Zero-day Attack Prevention
Most of the discovered vulnerabilities are fixed pretty fast. When these breaches are not expected, specialists who found them report them to the vendor, and the latter fixes them as fast as possible. In the current environment, it is important to keep silent until the exploit fix is released. OSINT gives a lot of basic information for cyberattacks, so even several words you told in your Instagram story can act a lot. But, what is a zero-day attack in cyber security?
The exact danger for you is in the fact that someone applies this exploit against you. Its existence is unpleasant, but it is still nothing until you are not attacked. However, it is quite hard to make sure that no one will ever attack you. Fortunately, there are some tips that may decrease this danger, as well as the overall damage done by the attack by orders of magnitude.
- Use a well-done security tool. Both regular and zero-day vulnerability may easily circumvent the non-professional protection mechanisms. Using the solutions like EDR, together with all possible security setups in the systems will decrease the chances of a successful attack. Harsh delimitation of rights will likely block the span of possible actions, while the EDR with a zero-trust policy will detect and block all possible tricks they may apply to reach the target. For sure, that is not a panacea – all these actions are recommended to apply along with regular cybersecurity measures.
- Update your software regularly. Even though zero-day vulnerabilities may be discovered even in the latest version of programs, the chance of such a case decreases with the growth of version number. Sure, sometimes this rule does not work, but it is better to rely on a trend than to deny it because of the miserable exclusions. Besides zero-day attacks, you will also receive patches for all breaches that were already discovered. Older versions may have a worse codebase, or contain solutions that are much easier to hack.
- Limit the attack surfaces. Even when you cannot predict where the attack will happen, you still can make it much harder to apply any attack vector. The biggest breach which is present in each company – the human – must be the element of the biggest concern. Zero-click attacks happen pretty rarely, so the vast majority of threats your company will face will likely be related to the actions of your employees. Opening the attached file from the phishing email, and plugging in the flash drive without scanning it for possible malware – that may look like a low probability case, but that isn’t.




