Secureworks researchers have discovered a phishing campaign by Chinese Mustang Panda cyberspies targeting Russian officials and the military.
According to experts, Chinese “government” hackers from the Mustang Panda group (aka HoneyMyte, Bronze President, RedDelta and TA416) are behind the attacks.
Let me remind you that we wrote that Hacker groups split up: some of them support Russia, others Ukraine, and also that, for example, RuRansom Malware Destroys Data in Russian Systems, so perhaps the Chinese hackers simply chose a side.
This hacker group has been active since at least July 2018, and most often its attacks target various regions of Southeast Asia, although sometimes hackers are also interested in targets from Europe and the United States.
Secureworks reports that this time the Mustang Panda is exhibiting unusual behavior as the attackers now appear to have focused on Russian military personnel and officials working near the border with China. In their phishing baits, hackers exploit the theme of Russia’s invasion of Ukraine: malicious documents are written in English and disguised as data published by the EU on sanctions against Belarus.

Such lures are .exe executable files, but disguised as PDF documents and are named in Russian – “Blagoveshchensk – Blagoveshchensk border detachment.” The question arises why the document named in Russian contains the text in English, but the logic of the hackers in this matter has remained a mystery to researchers. Secureworks specialists came to only one clear conclusion: the target of this campaign is Russian officials or the military in the border region.
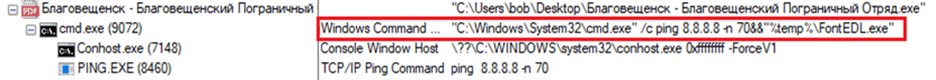
Running the executable extracts many additional files, including the decoy document itself, which can be seen in the screenshot above, a malicious DLL loader, an encrypted version of the PlugX (aka Korplug) malware, and another .exe file.
PlugX is the main tool of hackers; it is a remote access Trojan for Windows that allows to execute various commands on infected systems, steal files, install backdoors and additional malicious payloads. Several Chinese hack groups have been relying on this malware for many years.
It should be noted that the results of the Secureworks study complement the reports of Proofpoint and ESET, released last month. They detailed the use of a new PlugX variant codenamed Hodur, so named because of its resemblance to another variant called THOR.




