Kinsta, a prominent WordPress hosting provider, has issued a warning to its customers regarding a concerning new trend in cyberattacks. Cybercriminals are now leveraging Google Search Ads to promote phishing websites aimed at stealing user credentials, particularly those for Kinsta’s vital service, MyKinsta, which is used to manage WordPress and other cloud-based applications.
Kinsta Phishing: Hackers Exploit Google Ads
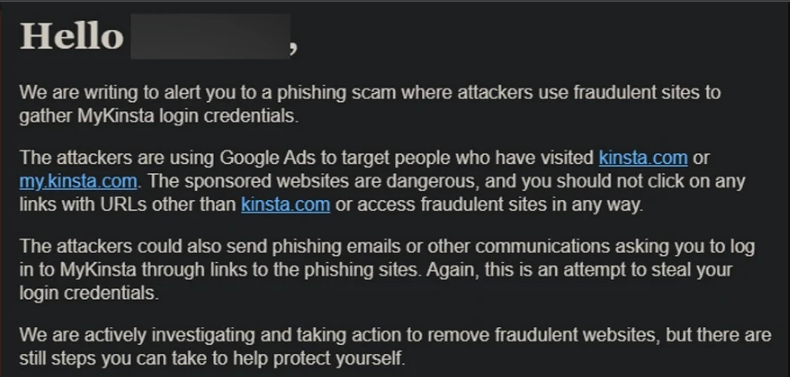
In an email notification, Kinsta shares that cybercriminals use Google Ads as the primary vector for their phishing attacks. These attackers specifically target individuals who have previously visited Kinsta’s official websites. They craft fraudulent websites that closely mimic Kinsta’s own, cunningly enticing users to click on them.
The email from Kinsta states:
The Impact
This incident highlights a broader trend of cybercriminals exploiting Google Ads to deceive users and compromise their security. I’ve reviewed the first massive case of 2023 back in January, though similar phishing ads kept appearing for the whole year. Recent examples include deceptive ads masquerading as legitimate pages for Amazon. Clicking on these ads redirected users to tech support scams.
The primary objective was to lure users into entering their Kinsta login credentials on the fake website. Once stolen, attackers could exploit these credentials to gain access to users’ WordPress websites, potentially causing serious damage. This could include:
- Sensitive information stored on compromised websites, such as customer data, financial details, and intellectual property, could be exposed.
- Attackers could inject malicious code into compromised websites, redirecting visitors to phishing sites or spreading malware further.
- The website’s content could be defaced or replaced with malicious messages.
- Access to payment gateways or sensitive financial information could lead to financial losses for users or their clients.
- A successful phishing attack could damage Kinsta’s reputation by casting doubt on its security measures and leading to user distrust.
Phishing increases with Google Ads
Google Ads, a widely used advertising platform, has unfortunately become an increasingly popular tool for hackers and cybercriminals. These individuals and groups are exploiting the platform’s reach and visibility to carry out various malicious activities.
Several websites advertised fake downloads for popular software including Grammarly, MSI Afterburner, Slack, Dashlane, Malwarebytes, Audacity, μTorrent, OBS, Ring, AnyDesk, Libre Office, Teamviewer, Thunderbird, and Brave through Google Ads.
Protecting Against Phishing Threats
Kinsta emphasizes the malicious nature of these sponsored websites. Also, strongly advises users to exercise extreme caution when dealing with any links. These links should lead directly to the official kinsta.com or my.kinsta.com domains. The company also urges users to enable two-factor authentication (2FA) on their accounts to enhance security measures further.
To protect against these threats, it is crucial to exercise caution when interacting with online ads. Always verify the URLs of the websites you visit and refrain from clicking on suspicious links or sharing login credentials in response to unsolicited messages. To be completely sure that you follow a proper link, avoid clicking any ads in Google Search, using regular results instead.
Use reliable anti-malware software with network protection features. We highly recommend GridinSoft Anti-Malware because it is a fast, lightweight and highly effective solution that can effectively counter a wide range of threats. You can explore its features during the 6-day free trial period.





