Israeli cybersecurity specialist Zohar Shachar talked about his discovery of XSS vulnerability in Google Maps in 2019, and then found out that Google was unable to fix it from the first time.
The issue was related to the Google Maps feature that allows users to create their own maps. Such maps can be exported in a variety of formats, including Keyhole Markup Language (KML), which is XML-based and commonly used to display geographic data in Google Earth, and so on.
While examining the server response when exporting a map using KML, the researcher discovered an XML that contained, among other things, an open CDATA tag. Shahar tried to close the tag with special characters and found that adding “]]>” at the beginning of the payload (at the beginning of the map name) helps to go beyond CDATA and add arbitrary XML content.
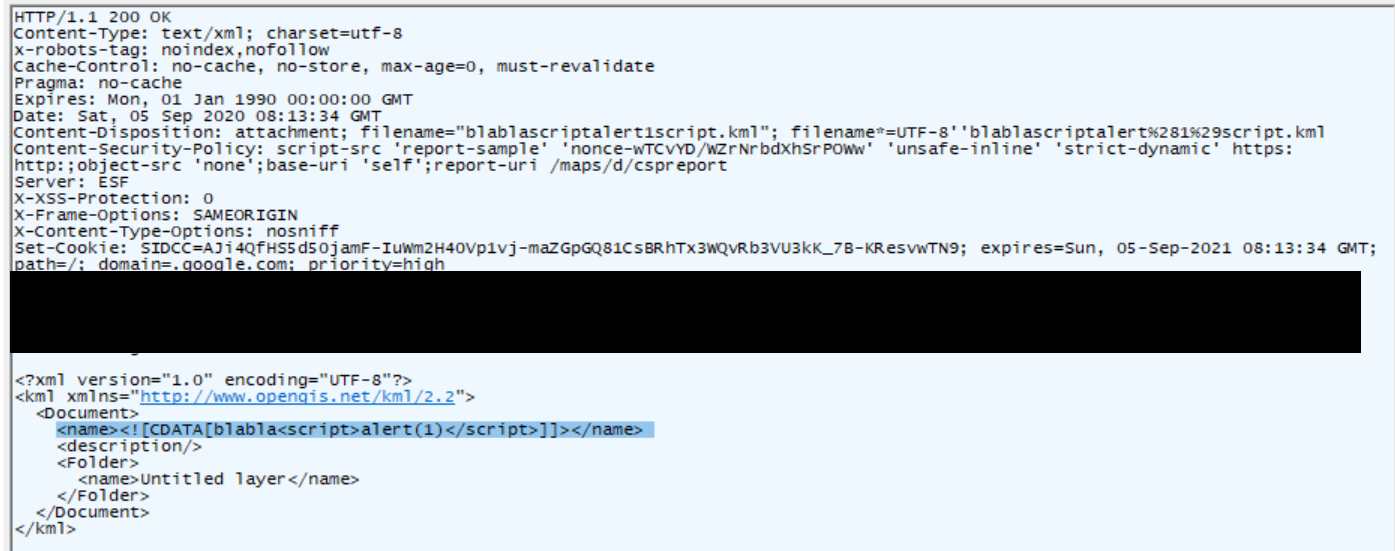
All this ultimately leads to an XSS vulnerability. For example, an attacker could create a new map in Google Maps, equip it with an XSS payload, make it public and export it as a KML file, and then copy the download link.
“After that, the hacker could only send the link to the victim and wait for the victim to click on it, launch the exploit and execute the malicious code in his browser”, — says Zohar Shachar.
The researcher immediately reported about the problem to Google, but the story was not finished. When Shahar received notification that the vulnerability was fixed and earned $5,000 for discovering the error, he decided to check if this was so and was surprised to see that the “patch” consisted of adding another CDATA tag.
Therefore, to bypass the two CDATA tags and this fix, attacker only had to close the tags twice, and the exploit worked again.
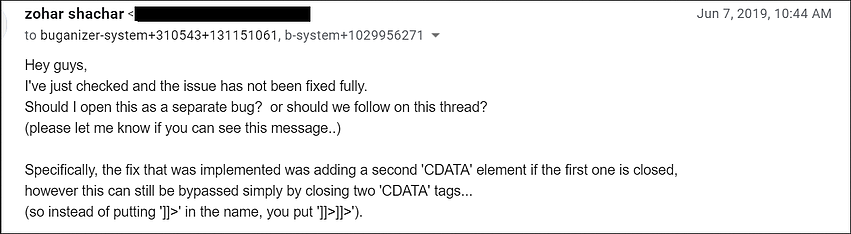
Doubting that he understood what was happening correctly (such a simple workaround of the patch seemed unlikely to Shahar), the researcher nevertheless contacted Google again and explained that the fix did not seem to work. As it turned out, Shahar was completely right. Just two days later, the error was completely corrected, and the researcher was paid another $5,000, as he technically discovered another similar problem.
“After the Google Maps bypass incident, I always re-check patches, even for the simplest things, and it pays off. I sincerely urge all of you to do the same”, — writes he researcher.




