IntSights experts found that recently in the darknet there increased interest YouTube Channel Credentials, and also, as a “side effect”, this stimulates data verification activities.
On hacker forums and sites that sale credentials, you can find more and more offers of this kind.
It should be noted that cybercriminals for a long time were interested in YouTube, because the site provides them with a new audience that can be used in a variety of ways, from fraud to advertising. In addition, attackers often “steal” popular channels from their rightful owners, and then demand a ransom for the return of access.
“The data on YouTube channels is mainly collected from computers infected with malware, as a result of phishing campaigns and so on. After the stolen information is sorted into specific logins and passwords from certain services, and then sold on the black market”, — said IntSights researchers.
The cost of listings for sale with recorded data from YouTube channels is proportional to the number of subscribers. Researchers give some examples. So, in one case, the price for a channel with 200,000 subscribers began at $1,000 and increased in increments of $200.
In another case, the researchers found an auction advertisement, in which they sold data from 990,000 active channels, and the price started at $1,500 (the one who paid $2,500 received a list without bidding). Obviously, the seller was hoping to make money quickly by selling the data, as he was afraid that his victims would notice compromise, turn to support and regain access to their accounts.
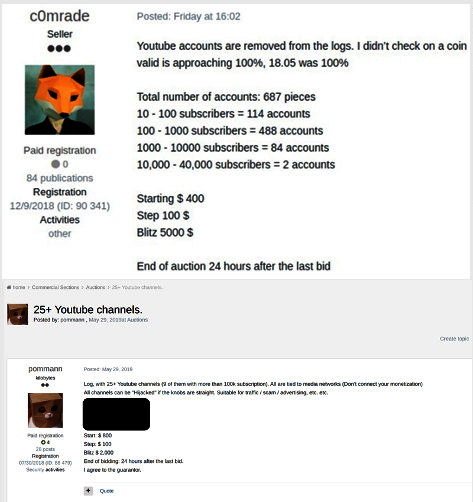
Another set of 687 YouTube accounts, sorted by the number of subscribers, was put up for sale at an initial price of $400 (the price increased in increments of $100, and for $5,000 a lot could be withdrawn immediately).
IntSights experts believe that hackers are likely to collect material for such lists with credentials from YouTube channels, checking databases with stolen logins and passwords (in search of data from Google accounts) and data received from infected computers.
IntSights experts write that earlier cybercriminals used sophisticated phishing campaigns and reverse proxy toolkits to spoof Google’s two-factor authentication. Now sellers rarely mention 2FA, and most likely this suggests that the hijacked accounts were not protected by two-factor authentication.
Bleeping Computer magazine notes that users who suffered from hacking and hijacking an account on YouTube often complain that they tricked them into downloading the malware. For example, in the network you can find such complaints:
“They pretended to be YouTube sponsors, and when I tried to access their site, a keylogger / spyware was uploaded to my browser. For a maximum of a couple of minutes, they changed my password, deleted my devices, deleted my phone number and email used for recovery. Then they tried to extort money from me, they wanted me to send them BTC, or they will sell my channel.”
Another scam victim tells a similar story when scammers pretended to be looking for people to collaborate on.
For example, I told you that MyKingz botnet uses Taylor Swift photo to infect target machines. Just a good photo)




