Information security specialists from PRODAFT have published the results of an investigation into the Wizard Spider group, which is allegedly associated with the Grim Spider and Lunar Spider hacker groups.
The Wizard Spider group, possibly of Russian origin, manages an infrastructure of “a complex set of sub-commands and groups, controls a huge number of hacked devices, and uses a highly developed workflow to ensure security and a high pace of work.”
Let me remind you that we also reported that Leaked Conti ransomware source codes were used to attack Russian authorities, and also that State Department Offers $1 million for Info on Russian Hackers.
Now various cybercriminal campaigns often use a business model that includes hiring the best specialists and creating a financial basis for depositing, transferring and laundering proceeds to make a profit or work in the interests of the state. Wizard Spider, according to this model, invests part of the profits in development by investing in tools, software and hiring new specialists. According to the report, the group owns “hundreds of millions of dollars in assets.”
Wizard Spider focuses on compromising corporate networks and “has a significant presence in nearly every developed country in the world, as well as many emerging economies.” The group’s victims include defense firms, corporate firms, equipment suppliers, hospitals and infrastructure companies.
Wizard Spider attacks start with spam and phishing using QBot and SystemBC proxy. The group can also infiltrate the business through compromised email between employees in BEC (Business Email Compromise, BEC) schemes.
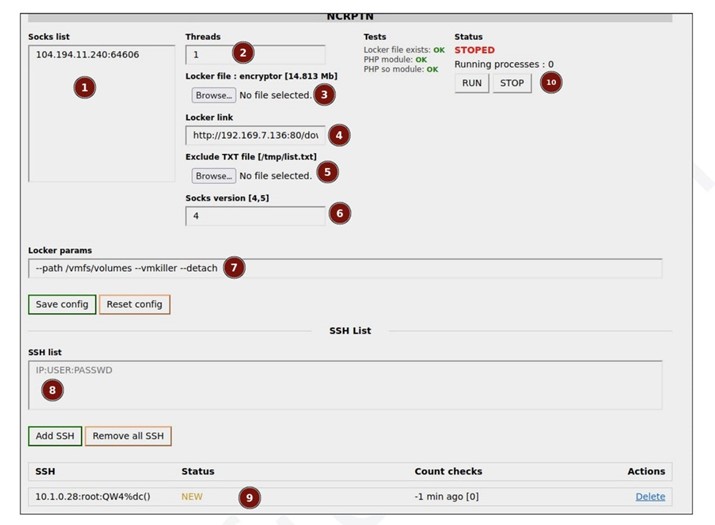
After gaining access to the system, the group can deploy Cobalt Strike and attempt to gain domain administrator rights. Once the Conti malware is deployed and the computers and hypervisor servers are encrypted, the hacker can demand a ransom from the victim. Compromised devices are managed through the control panel.
Wizard Spider uses VPNs and proxy servers to hide its tracks. The group has invested in VoIP systems and employees who call victims and intimidate them into paying a ransom.
The Sekhmet, Maze, and Ryuk groups have used such scare tactics in the past. Coveware suspects that such “call center” work could be outsourced to cybercriminals, as the templates and scripts used are often the same.
Another notable tool is the Wizard Spider hack station. A special set stores cracked hashes and launches attackers to pick up domain credentials and other forms of hashes.
The station also informs the team on the status of the hack. There are currently 32 active station users. Also, several servers were found containing a cache with tactics, methods, exploits, information about crypto wallets and encrypted ZIP files with notes of attacking groups.