The researchers warned that the RapperBot Mirai botnet has resumed activity, and now the updated malware is used for DDoS attacks on game servers, although the exact goals of the botnet are unknown.
Let me remind you that we also wrote that Google revealed the most powerful DDoS attack in history, and also that MooBot Botnet Attacks D-Link Routers.
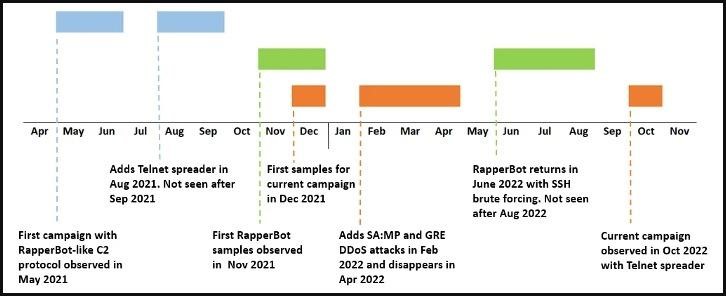
For the first time, RapperBot malware was discovered by Fortinet analysts in August last year. Then it was reported that RapperBot has been active since May 2021, uses SSH brute force and is distributed on Linux servers.
RapperBot Campaigns
The new version of the malware that researchers have now discovered uses a self-propagation mechanism via Telnet, which is more similar to the original Mirai that underlies this malware. In addition, the goals of the RapperBot operators have become more obvious in the current campaign: in the new version, the malware is clearly adapted for attacks on game servers.
Experts were able to study the new version of RapperBot using C&C communications artifacts collected during previous campaigns (that is, this aspect of the botnet’s operation has not changed). It turned out that the new version has several differences, including support for Telnet brute force using the following commands:
- registration (used by the client);
- keep-alive (do nothing);
- stop DDoS and shut down the client;
- carry out a DDoS attack;
- leave all DDoS attacks;
- restart Telnet brute force;
- stop Telnet brute force.
Now the malware tries to brute force new devices using weak credentials from a hard-coded list, whereas previously such a list was loaded from the control server.
If the accounted data is successfully guessed, the malware reports this to the cybercriminals’ control server via port 5123, and then tries to obtain and install a payload binary suitable for the architecture of the attacked device. The currently supported architectures are ARM, MIPS, PowerPC, SH4, and SPARC.
In addition, the functionality of RapperBot has been replenished with an extensive set of commands for DDoS attacks, including:
- UDP flood;
- TCP SYN flood;
- TCP ACK flood;
- TCP STOMP flood;
- UDP SA:MP (targets Grand Theft Auto: San Andreas game servers)
- GRE Ethernet flood;
- GRE IP flood;
- TCP flood.
Since the malware uses the Generic Routing Encapsulation (GRE) tunneling protocol and UDP, the researchers say that Grand Theft Auto: San Andreas Multi Player (SA:MP) servers are clearly one of the targets of the attackers.
Fortinet experts believe that all RapperBot campaigns were most likely organized by the same operators, since the new malware variants are clearly created by people who have access to the malware source code. Moreover, the C&C communications protocol and the credential lists used remain unchanged.




