VMware specialists spoke about the activity of the RuRansom wiper, which attacks Russian systems and deliberately destroys its data, including backups. Unlike ordinary cryptographers who extort ransoms from the victims, the author of RuRansom does not ask for money, but simply intends to cause damage to the Russian Federation.
By the way, let me remind you that we reported that hacker groups split up: some of them support Russia, others Ukraine.
Back in early March, Trend Micro analysts wrote about RuRansom, who told users and companies about the new anti-Russian viper. According to the company, the malware appeared on February 26 and was created as a destructive software, specifically to destroy the backups and data of the victims.
As VMware experts, who have prepared their own analysis, now say, the viper is written in .NET and spreads like a worm and copies itself as a file with a double doc.exe extension to all removable drives and connected network resources.
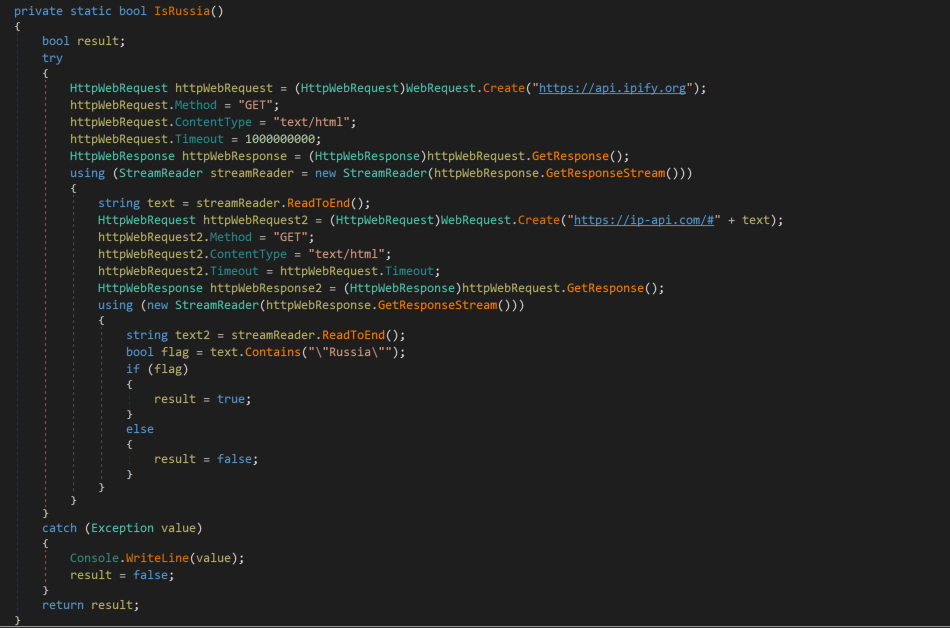
After being launched on the victim machine, the malware immediately calls the IsRussia() function, checking the public IP address of the system using a well-known service located at https://api[.]ipify[.]org. RuRansom then uses the IP address to determine the geographic location of the machine using a known geolocation service using the URL format https://ip-api[.]com/#[public ip].
Note: And also, for example, we reported that leaked Conti ransomware source codes were used to attack Russian authorities.
If the target is not in Russia, the malware displays a message on the screen: “Only Russian users can run the program” and stops execution.
If the process is not interrupted, the malware gains administrator privileges using cmd.exe /c powershell start-process -verb runas and proceeds to encrypt data. Encryption applies to all extensions except for .bak files, which are removed. The files are encrypted using the AES-CBC algorithm with a hard-coded salt and a randomly generated base64-length key (“FullScaleCyberInvasion + ” + MachineName).
At the same time, the note left by the malware author in the code and file “Full-scale_cyber-invasion.txt” says that he does not need a ransom, and he wants to harm Russia by avenging the “special military operation” in Ukraine.