SASE and Zero Trust look as two paradigms that aim to secure access to resources in a networked environment and overall improve its secureness. Although SASE and zero trust are often seen as competing ideas, they approach the problem from different angles. Let’s have a closer look at each one and answer the question, at last – what is better, SASE or Zero Trust?
Secure Access Service Edge (SASE) Overview
Secure Access Service Edge (SASE) is a network architecture that combines wide-area networking (WAN) capabilities with comprehensive security functions. It is delivered predominantly as a cloud service (SaaS). Developed by Gartner in 2019, SASE seeks to provide secure and efficient access to resources regardless of the user’s location. In other words, it replaces hardware data centers with cloud-based infrastructure. This infrastructure offers flexibility, easy scalability, and multi-layered security measures. It allows you to consolidate your networking and security tools in one place.
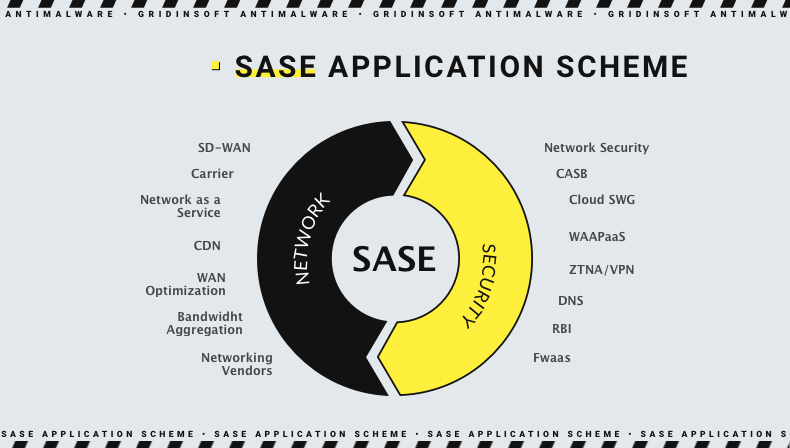
SASE includes Software-Defined Wide Area Network (SD-WAN), enabling reliable and efficient connectivity across multiple locations. This technology allows for intelligent routing and network traffic optimization to ensure consistent performance. The cloud-based security services integral to SASE bring together various security functions such as secure web gateways, cloud access security brokers, firewall as a service, and zero trust network access (ZTNA). These components work together to protect users and data by applying security policies in the cloud, providing a unified security approach across different access points.
SASE is also identity-driven, meaning security policies are based on the identity of users and devices rather than relying on traditional network boundaries. This approach ensures access controls are more dynamic and adaptable to different scenarios, especially in environments where users and devices are constantly moving. Additionally, SASE leverages a global edge network, which consists of a distributed network of points of presence (PoPs). These PoPs help deliver low-latency access and high performance by ensuring users are connected to the nearest and most optimal network location.
What is Zero Trust?
Zero trust is a security framework that operates on the principle of “never trust, always verify.” Unlike traditional security models that rely on defined perimeters, zero trust assumes that threats can exist both inside and outside the network by default. Therefore, continuous verification of user identity and device health is required.

Zero trust emphasizes micro-segmentation. This strategy divides networks into smaller, isolated segments to limit attackers’ lateral movement. This segmentation helps contain potential breaches and minimizes the risk of widespread damage. Continuous authentication and authorization are fundamental to zero trust. This approach requires regular verification of identity and context, including user behavior and device status, to ensure that access remains secure at all times. Such steps, although looking redundant, are essential against attacks with the use of a stolen identity.
Another cornerstone of zero trust is the concept of least-privilege access. This principle ensures that users and devices have the minimum level of access necessary to perform their tasks. As a result, this reduces the potential attack surface. Furthermore, endpoint security is crucial within Zero Trust. It involves robust protection and monitoring of all endpoints accessing the network to prevent unauthorized access and detect anomalies.
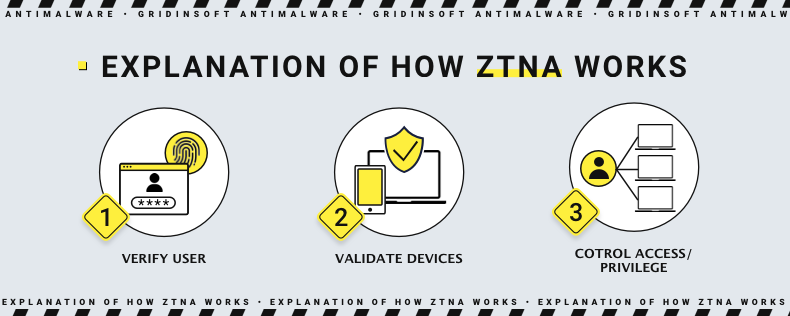
In network security, zero trust appears as a part of Zero Trust Network Access solutions. They, in turn, may sometimes be integrated into the aforementioned SASE solutions that offer a much more comprehensive protection. It in particular can focus on providing secure remote access without intrinsic networking capabilities. Although the integration may sometimes be time-consuming and complex, quite a few of them come already ingrained into the SASE system.
Comparing SASE and Zero Trust
While both frameworks aim to enhance security, their approaches and focuses differ. SASE integrates networking and security in a cloud-native architecture, emphasizing ease of access and management for distributed environments. On the other hand, zero trust focuses on strict access controls and continuous verification. This makes it highly effective for protecting against insider threats and advanced persistent threats (APTs).
SASE might be easier to implement for organizations that are already extensively using cloud services. It relies on cloud-based security services and a global edge network. Zero Trust can be more complex because it requires granular controls and continuous monitoring of all network activities and entities. SASE’s cloud-native approach also offers greater flexibility and scalability. This mainly benefits organizations with a significant remote workforce or multiple branch offices. In contrast, zero trust’s focus on micro-segmentation and endpoint security might necessitate more substantial changes to existing infrastructure.
Performance is another area where these frameworks differ. SASE can improve performance by optimizing traffic through its global PoPs, ensuring users have fast and reliable access to resources. On the other hand, zero trust’s continuous verification processes might introduce some latency. This though can be mitigated with advanced technologies and efficient implementation strategies.
As a part of the SASE solution, zero trust elements can bring quite substantial improvements. An organization can minimize the potential impact of a compromised account by granting access based on the principle of “need to know” and aligning with business requirements. Implementing access control at the network level eliminates the need to accommodate the diverse requirements of different platforms, endpoints, and deployment environments. Additionally, using an integrated SASE solution allows for the centralized monitoring and management of policies and alerts, as opposed to dealing with multiple standalone solutions across the organization.
What is Best?
Choosing between SASE and Zero Trust depends on an organization’s specific needs, existing infrastructure, and security priorities. For companies looking to enhance their cloud and remote work capabilities, SASE may provide a more integrated and scalable solution. ZTNA as a stand-alone implemetation of a zero trust approach may be of a great effectiveness, though may require additional software for better visibility and control.
Still, oganizations with high-security requirements and complex internal networks might benefit more from zero trust’s stringent controls and verification processes. Ultimately, both frameworks are excellent; they each serve different purposes. A hybrid approach incorporating both frameworks’ elements could offer the most robust security posture.