
What Is Firewall?
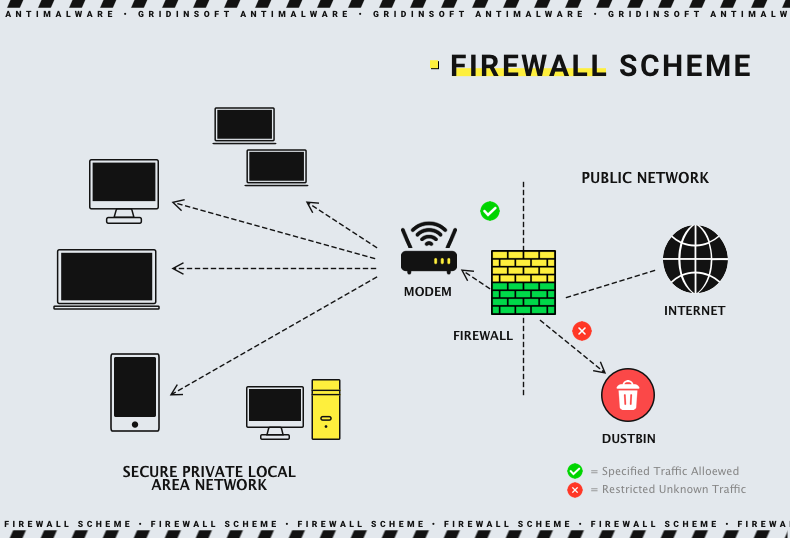
A firewall is a complex tool designed to protect internal networks from external sources (internet, for example) threats like malware or threat actors. It may consist of a hardware device (network router or switch) or software (firmware or a specific app in the OS). Exactly, devices cannot function properly without the specific programs or firmware.
Firewall monitors incoming and outgoing network traffic deciding on whether to permit or block going data packets according to a previously established set of security rules. It serves as a barrier between the user's internal network and incoming traffic from outside.
How Does Firewall Work?
Firewall is a borderline between external networks and guarded internal ones. It usually has inline insertion across network connection monitoring all coming in and out data packets. To separate malicious data packets from original packets, the firewall has a specifically created set of rules to distinguish between the packets monitored. A firewall is needed not only to protect against malware. They are also used when you need to cover certain parts of the network infrastructure from prying eyes or restrict internal users from connecting to certain sites.
Set rules can be based on several important security points that indicate the desirability or safety of any specific data packet that is subject to monitoring:
- Content of data packet;
- Destination of data packet;
- Source of data packet.
The term "packet" here means pieces of data specifically formatted to the internet transfer. Each packet will contain the data it is transferring and the information about it, for example, where this data packet is coming from.
Based on the information every data packet has, the firewall decides on whether to allow it or block. The rules can be different on every other layer of the network. Also, every data packet that moves through the network must be reformatted several times for protocols to know where to send it. Different types of firewalls exist for monitoring data packets at different layers of the network.
What Are The Different Types Of Firewall
Firewall can come in the form of software and hardware. Specialists recommend having both variants in place. You can install a firewall as an application on your computer and it will regulate the traffic via applications and ports. Alternatively, you can use a physical firewall that looks like a piece of equipment you need to install between the gateway of your network and the network itself. Below are the most common types of firewalls and what exactly they will do in terms of securing your networks:
- Stateful multilayer inspection (SMLI) firewall. The firewall monitors packets at transport, application, and network layers and compares them to already known and thus trusted data packets. The same as NGFW firewall SMLI only allows those data packets that were permitted on every layers individually;
- Network address translation (NAT) firewall. This type hides every IP address on a network and allows one to connect to a network using a single IP address for all multiple devices. This security method ensures that threat actors won't be able to get the specific details about each of the devices on the network, which includes IP addresses. This type of firewall works similar to proxy firewalls because they pose as an intermediary between a group of connected devices and the outside networks;
- Proxy firewall. The firewall works at an application level and unlike the basic type of firewall it serves as an intermediary between two end systems. A client first sends a request to the firewall, which is compared against previously set security rules and either permits or blocks the request. Along with evaluating requests, the firewall conducts both deep and stateful packet examination;
- Next-generation firewalls (NGFW). One of the most effective types of firewalls includes traditional firewall functionality and additional ones like anti-virus, intrusion prevention systems, encrypted traffic inspection, and more. But most importantly, it has a packet inspection (DPI). Unlike basic firewalls, which only look at the headers of every monitored packet DPI allows for analysis of the data inside the packet itself;
- Packet-filtering firewall. This is the most common type of firewall. It monitors data packets and either block or allows them according to the set security rules. A firewall examines every sent in and out of the packet and its IP destination. If any specific packets are in the set security rules, they are allowed to pass.
There are two categories of packet filtering firewalls: stateless and stateful. Stateful firewalls can "remember" previously allowed data packets therefore, specialists consider them more reliable. Stateless firewalls do not hold information about previously allowed data packets. In some cases, data packet filtering firewalls can be quite effective, but the service of securing networks they provide is fundamental and limited.
Do I Need Firewall Protection?
When you connect your computer to the Internet it automatically becomes susceptible to various cyber attacks. Firewalls are the tools that will help you to protect yourself against all the malicious activity going on the Internet and at the same time ensure your positive experience on it, allowing data you need safely come to you.
Firewalls put a barrier between your computer and malicious traffic, but they also prevent unauthorized access to your computer or network. You can configure your firewall so that it will block data coming from specific locations, ports, applications, etc, and at the same time ensure the safe and secure passage of relevant data.
Can Firewall Fully Protect Your Computer?
Even if your firewall is properly configured, it may leave some security gaps in your network. Most users won't be a great concern if they also use antivirus or antimalware software and maintain good cyber security hygiene. In case of everything is in place , there won't be many problems for ordinary users.
The same goes for large companies and enterprises but on a large scale where there could be up to thousands of various entry points like servers, endpoints, clients, and more. Firewall accompanied with effective anti-malware or antivirus software, staff education on main cyber threats and how to recognize them should ensure the most robust cyber security system.
