
What is an IP address?
Basically, IP addresses explain the principle by which the internet works. Because the internet needs some way to differentiate between millions of computers, websites, and routers, that's where the IP address comes in help. They provide information on location and also make devices accessible for communication.
What is IP Address?
An IP address looks like a string of numbers separated by dots. More precisely, it is a set of four numbers — an example address will be 192.158.1.38. Each number in an IP address set can go from 0 to 255. The full IP address range varies from 0.0.0.0 to 255.255.255.255.
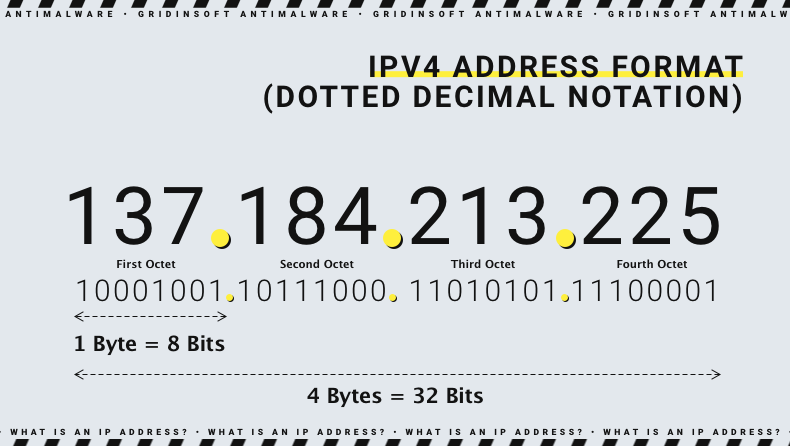
At first sight, it might seem random, but numbers in IP addresses don't come from a pure guess. They are created mathematically and are assigned by the Internet Assigned Numbers Authority (IANA), a division of the Internet Corporation for Assigned Names and Numbers (ICANN).
Established in the United States in 1998, ICANN is a non-profit organization that helps maintain the security of the internet and its usability for all. Each time you need to register a domain on the internet, you will do this with a domain name registrar that pays a fee to the ICANN to register the domain.
Technically, an IP address can be represented in several formats and, therefore, can be used in a URL in various ways. For example, any IP address (en example 137.184.213.225) can be written in other formats, including:
- Octal IP address: http://0211.0270.0325.0341
- Hexadecimal IP address: http://0x138861525
- Integer or DWORD IP address: http://2310591969
Private Address Ranges
The Internet Assigned Numbers Authority (IANA) has assigned several address ranges used by private networks. Address ranges to be used by private networks are:
- Class A 10.0.0.0 to 10.255.255.255
- Class B 172.16.0.0 to 172.31.255.255
- Class C 192.168.0.0 to 192.168.255.255
THEREFORE, an IP address within these private ranges is considered non-routable, as it is not unique. Any private network that needs to use IP addresses internally can use any address within these ranges without coordination with IANA or an Internet registry. Addresses within this private address space are unique within a given private network.
How do IP Addresses Work?
It's a sure thing that every time you have troubles with internet connectivity, you always have the question of how everything in it works popping up in your head. But, understanding how everything works won't take too much effort.
Internet Protocol is a universal language with a set of guidelines that regulate the way computers all around the world communicate with one another. All devices send, find and exchange information with the help of this universal language that all computers understand.
An average user usually doesn't get to see how the thing works as communication happens behind the scenes. The simplified version of the process will be like this:
- When your device connects to the internet, it gets connected to some network, granting you access to the internet. For home users it would be an ISP (Internet Service Provider) and at work — your company's network;
- Your ISP assigns you your IP address. ISP reroutes internet connectivity back to you using your assigned IP address. Because they give you access to the internet, it's they who assign you an IP address;
- Your IP address can change. Either way, you can ask your ISP to change it, or it can be changed by turning on and off a router/modem. Also, when you leave your home, you don't take the IP address with you. Because you will be using another network and receive another (temporary) IP address assigned to you by the airport, hotel, coffee shop provider.
Types of IP Addresses
There are several different types of IP addresses. Whether your IP address is inside the network or outside, it would be either a local IP address or public. And public IP addresses can be dynamic or static. For website owners who don't host their server but instead rely on a web hosting package (which is the case for most website owners) there are shared and dedicated types of IP addresses. Read the following paragraphs to learn more about each type:
- Local IP address. If you have multiple internet-connected devices at home, your router needs a way to recognize them all, and they also need to somehow identify and communicate with each other. Within your primary IP address, each device receives its IP address assigned to them by your router;
- Public IP address. A public IP address, in its turn, is the IP address assigned to your router by your ISP provider. This IP address is considered the main IP address of your home network. Typically, ISPs have many IP addresses that they assign to their customers. And your public IP address is the main address that all other users and devices outside your home network will recognize you by;
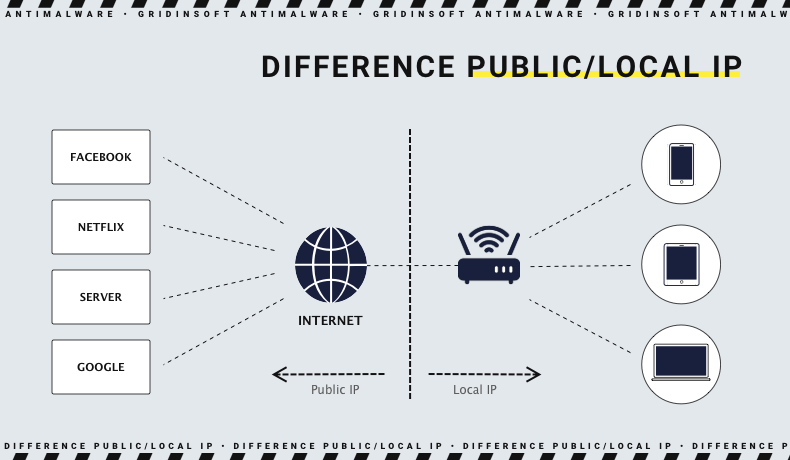 Schematic difference between public and local IP address
Schematic difference between public and local IP address - Dynamic IP address. This type of IP address changes regularly and automatically. ISPs, as it was said, buy a large of the IP addresses to re-assign them to their customers and put the old IP addresses back into the pool for further use. Automating the process means ISPs don't need additional actions to reestablish the IP address. The benefits come from the savings costs of buying new IP addresses and securing their customers because changing IP address makes it harder for cybercriminals to hack into your network;
- Static IP address. On the contrary, static IP addresses do not change once assigned. Most individuals and businesses do not need this option, but it is a crucial point for those who will host their server. A static IP address ensures that all email addresses and websites tied to a specific server will be easily found on the internet by other devices;
- Dedicated IP address. A dedicated IP address allows for easier sharing and transferring of files with numerous people within an organization. This type of IP address also allows to access the website only using the IP address rather than the domain name — a useful feature if you want to build and test it before you register your domain;
- Shared IP address. In shared hosting plans, many websites are hosted on the same server. Such websites usually include individual websites or SME websites, those sites limited in pages, etc., and where the traffic volumes can be managed;
What is My IP Address?
One of the simplest ways to check your IP addresses would be to type in the Google Search words like "What is my IP address". As a result, you will receive an extensive list of various sites where you can easily see your IP address.
For example, your current IP address and country:
216.73.216.181 - US
Some of these sites will show you your internet provider and the city. Of course, the information on the location is approximated; it will be shown only the location of your internet provider. To get the information on your real physical location, someone needs to provide a search warrant to your ISP to have this information.
If you want to see the IP address of your devices, you can easily do this by looking up the info from your router. The usual way to do this would be to type the router's gateway IP address into a web browser to access it. After doing this, you can now navigate to something like "attached devices" where you should see all the devices currently or recently attached to the network and their IP addresses.
Also, you can look up the device's IP address by going into specific settings of your device:
- In Windows. Use the command prompt. Search for “cmd” (without the quotes) in Windows search. In the showed up pop-up box, type “ipconfig” (without quote marks) to see the information;
- On a Mac. Go to System Preferences. Select network - and the needed information should be on display;
- On an iPhone. Go to Settings. Select Wi-Fi and click the “i" in a circle () next to the network you are on – you should see the IP address under the DHCP tab.
IP Address Security Threats
Out of all various techniques to obtain your IP, cybercriminals most commonly will use social engineering and stalking. If a cybercriminal knows your IP address, they can launch several attacks to breach your security, like downloading illegal content using your IP, hacking into your device, or directly attacking your network.
To know what kinds of those will prove no less success in counteracting them and mitigating their consequences.
We will explain each related notion mentioned in a previous paragraph down below:
- Social engineering. Cybercriminals with much enthusiasm use social engineering attacks to make potential victims reveal their IP address. For example, they can find you on Skype or other similar instant messaging apps. Any app that uses IPs for customer communication looks up your IP address without much effort. Be careful who you chat with, as they can easily see your IP address on the app;
- Online stalking. Cybercriminals can get to know your IP address by merely looking up your online activities, like comments on websites and forums. Once they get your IP address, they can understand your approximate location. In addition to confirming their guess, they can see the info you provided themselves on social media;
- Downloading illegal content using your IP address. Cybercriminals are known to use stolen IP addresses to download content that they do not want to be traced back to them. It can be some innocent instances like downloading pirated movies, videos, or music, thus breaching your ISP's terms of use. More serious cases include the downloads of content related to terrorism or child pornography;
- Hacking into your device. To connect to the internet, uses ports and your IP address. Every IP address has up to thousands of ports. If a threat actor knows your IP address, they can easily force the connection to take, for example, control over your phone and steal some sensitive information. Or they could install some malware for further planned malicious actions;
- Attacking your network directly. Though it is much less common for an individual user to fall victim to a DDoS attack, this doesn't mean they don't happen. Knowing your IP address allows threat actors to conduct this and other similar direct attacks to disrupt your cyber safety and security. Usually the victims of such attacks become businesses and video game services;
How to Protect My IP Address?
To protect your IP address you need to hide it and you can manage to do this in following ways:
- Use VPNs. It's one of the easiest ways to hide your IP address. VPN, which stands for Virtual Private Networks, replaces your real IP address with either a dynamic address that changes with each connection, a dedicated address, or a static address that’s shared with multiple users. If you use a VPN your ISP will only see these replaced addresses instead of your actual IP address;
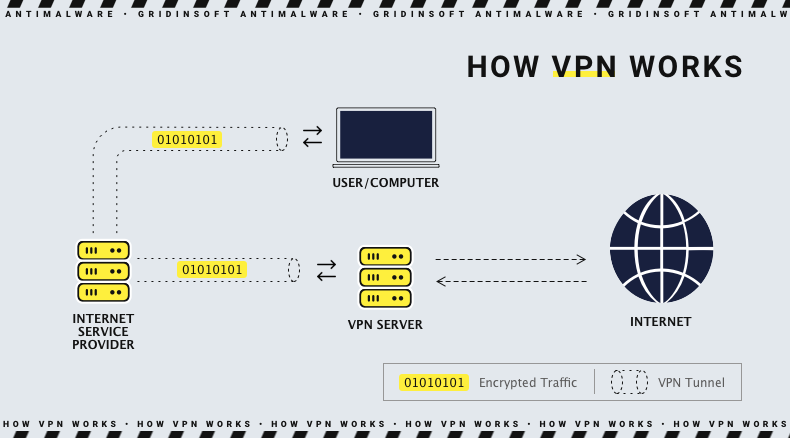 How VPN works
How VPN works - Use proxy servers. Many people confuse proxy servers with VPNs, but they have their differences. While you can use VPN for a long-term hide of IP, the proxy servers are only good for a one-time run. Of course, both options offer to hide and encrypt a user’s IP address, but VPN also makes the encryption of their web activity. Proxy servers are free, but you must pay for a good VPN service. But the proxy servers are only free because they sell the data of their customers, making in this sense, some paid VPN services a better choice;
- Use Tor. Cumbersome duty encryption tool that will ensure you the most security and privacy. The only problem is that the connection will be slow, making you wait. Initially released in 2008, the project became widely used by political descendants and cyber criminals. Tor browser will offer you multilayered encryption, resistance to fingerprinting, block of trackers, and surveillance without any payment because it's a volunteer-based project.
