Identity theft is a significant issue affecting millions yearly, whether through stolen credit card information or fraudulent accounts. It’s a lucrative business for criminals, who can steal billions of dollars annually through these methods. Unfortunately, data breaches are a common occurrence, and they contribute to the problem. While it’s impossible to prevent data breaches, there are steps you may take to reduce the chances of fraud or identity theft and minimize the damage it can cause.
What’s identity theft?
Identity theft is the use of someone’s personal information for fraudulent purposes. This can include name, social security number (SSN), credit card information, or other sensitive data. It also includes unauthorized access to bank accounts, credit card fraud, creating fake identities, or taking out loans in the victim’s name. In addition to the primary financial damage, identity theft often causes severe emotional distress to victims. It also creates serious problems in recovering and returning stolen identities.
Before the advent of the Internet, criminals had to monitor a victim’s physical mailbox in search of valuable information. Another standard practice was to rummage through the victim’s stinky trash to get the information they needed for identity theft. For example, those “you’re already approved,” pre-screened credit offers we all get in the mail. However, thanks to modern technology, today’s cybercriminals don’t need to go to such great lengths to invade someone’s privacy. Big businesses and large caches of data could be more profitable. They contained on their networks present a much more lucrative target than piecemeal attacks on individual consumers.
Types of identity theft
There are various types of identity theft, each with its own specific focus and methods. I will uncover the most common types of one according to available statistics.
Account takeover identity theft
Account takeover identity theft is a cybercrime where a fraudster gains unauthorized access to your existing accounts. Usually, such attacks aim at social media pages or bank accounts. The scammer can use this access to steal your money, take out loans or credit in your name, or deceive your friends, followers, or contacts with phishing attacks or other scams. As the “next tier” victims will see messages from a familiar person, the chances of a successful scam increase by orders of magnitude.
Credit identity theft
Credit identity theft is when a thief steals your credit card data and uses it for fraudulent purchases or obtains credit cards or loans under your name. According to the Federal Trade Commission, this is the most common form of identity theft. The reason is obvious – in this attack, fraudsters can go in cash much faster than in any other way.
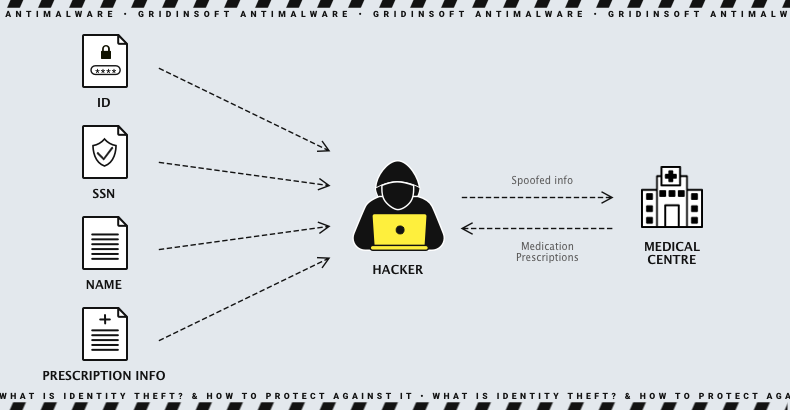
Medical identity theft
Medical identity theft occurs when criminals use victims’ personal information to receive medical treatment, obtain prescription drugs, or see a doctor. In the past, medical identity theft could have impacted victims’ health coverage or led to higher medical costs. However, recent changes in the law have addressed these issues. Still, scammers can incur past-due medical debts in your name, which can appear on a victim’s credit report and negatively affect their credit score. Seniors who receive Medicare are particularly vulnerable to medical identity theft, as frequent medical visits usually may not raise suspicion.
Medical identity theft is also dangerous due to the sensitivity of such information. If hackers manage to leak medical data of a person, they can further blackmail them in order to avoid disclosing their health condition. And when we are talking about celebrities, there are a lot of tabloids ready to spend a small fortune on information on such a topic.
Tax identity theft
Tax identity theft is when a scammer steals an individual’s SSN and uses it to receive a tax refund or secure a job. This commonly happens when victims’ SSNs are exposed online due to a data breach. Despite the lack of love received from taxpayers, the US Internal Revenue Service’s initiatives aimed at decreasing tax-related identity theft are effective.
Criminal identity theft
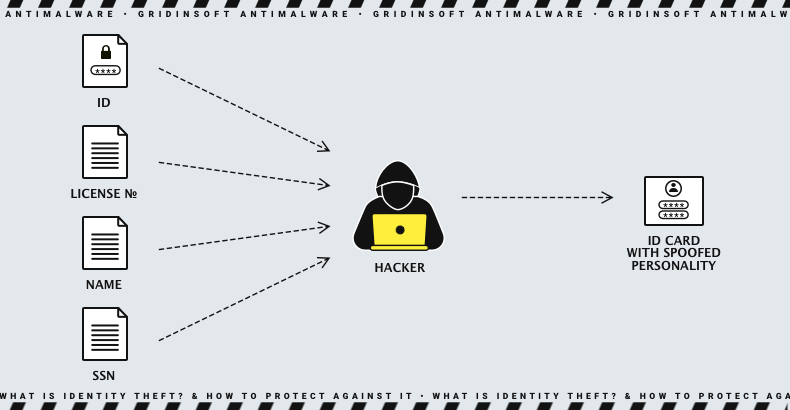
Criminal identity theft is a specific theft in which the perpetrator steals another person’s identity to commit a crime. Examples of crimes committed through criminal identity theft include driving under the influence, shoplifting, drug possession, trespassing, probation or parole violations, and failure to appear in court. The thief may use stolen name, date of birth, SSN, or other identifying information to impersonate the victim. As a result, the victim may face criminal charges, and have a criminal record. Criminal identity theft can have a devastating impact on the victim’s life.
Child identity theft
Child identity theft is fraudulently using a child’s personal information to obtain financial gain. The question arises: why would someone want to pretend to be a child? Well, there are many reasons for that. Scammers can use a child’s Social Security Number (SSN) to claim them as a dependent, obtain a tax refund, open a line of credit, get a job, or even obtain a government ID. Making someone’s child a tool in illegal credit obtaining or tax refunds is rather cynical, but fraudsters involved in such schemes never had strict moral rules.
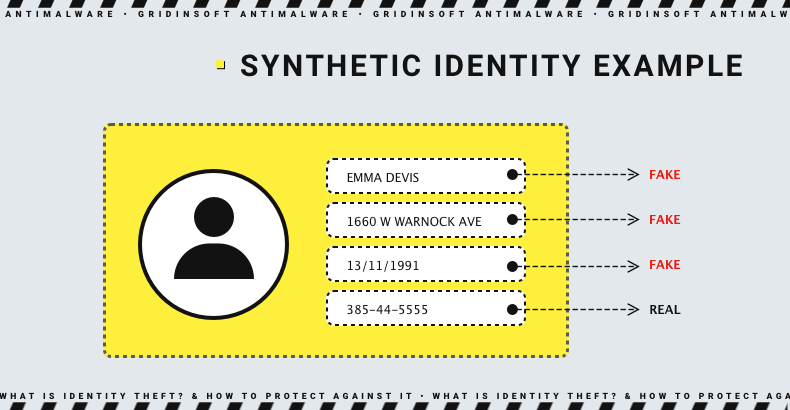
Synthetic identity theft
Synthetic identity theft means criminals create a new identity amalgamating real and fake information. They commonly steal real information, such as a Social Security number (SSN), and make up phony information. The latter is most commonly the name, address, or date of birth. Crooks obviously do it to mask a real identity in illegal activities. The thief can then use this synthetic identity to open credit accounts, get loans, or rent an apartment. Because the identity is new, credit bureaus or lenders may not flag it as fraudulent. This makes it easier for the thief to commit fraud without being caught.
How does it work?
While the number of identity theft methods is limited by the imagination of attackers. They can accomplish it either through physical contact with the victim or remotely. Somietimes, the attackers don’t need to do anything – the victim reveals all the necessary information themselves. The following are the most common examples:
Social engineering
By far, the unprecedented winner in successful identity theft is social engineering and phishing. Phishing involves tricking people into sharing sensitive information like usernames and passwords. Attackers often use social engineering tricks to manipulate emotions – most often greed and fear. They may send spoofed emails or text messages that appear to come from trusted sources. These messages urge recipients to take urgent action to verify payments or purchases. Clicking on the provided link will redirect users to a malicious login page designed to steal their login credentials.
Social media oversharing
The next point is very similar to the previous one, but the victim is the initiator here. There’s nothing wrong with wanting to share information on social media. However, users is essential to understand and choose what information to share and what should stay in private. Thus, oversharing on social media raises the risk of identity theft in case of a data breach. Facebook and Instagram have had bugs allowing access to the personal information of millions of users. To limit your exposure, check out our guide.
Malware and Exploits
Spyware and keyloggers steal personal information, such as usernames, passwords, and social security numbers. They can infect your computer through seemingly harmless software bundles or Trojans like Emotet, which can deliver spyware and other malware. Once infected, the spyware or keylogger sends your information to cybercriminals through C&C servers. Cybercriminals exploit software vulnerabilities to gain unauthorized access to a system and steal data. Researchers aim to report and patch these vulnerabilities in a race against criminals. Commonly exploited software includes operating systems, browsers, Adobe, and Microsoft Office applications.
Misplaced phones and wallets
Identity theft can occur when people lose their wallets, purses, or cell phones. Besides, crooks can steal them. Thieves can access important identification documents and sensitive information. And since smartphones commonly contain huge amounts of personal information, it is obvious that.
Data breaches
Data breaches refer to unauthorized access to a company’s database by hackers who target sensitive customer information. It includes names, addresses, social security numbers, and financial details. This can also be caused by SQL injection attacks or misconfigured access controls. SQL injection attacks exploit weaknesses in how websites interact with SQL databases, allowing hackers to access sensitive information. The alternative to this is misconfigured access controls that can accidentally make private information public.
Who is the primary target?
Identity theft can happen to anyone, but some groups are more vulnerable than others. For example, seniors are often targeted because they may be less familiar with technology and more trusting of unsolicited communications. People with good credit histories are also at risk since criminals can open new credit accounts in their name and make unauthorized purchases. Those with higher incomes may also be targeted as they have more financial resources to exploit. Children are also vulnerable targets as their personal information can be used for fraud over an extended period before being detected since they usually don’t have a financial history.
What can I do if I’m a victim of identity theft?
If you’re a victim, use this checklist to mitigate:
- Start by cleaning your computer. The first thing we recommend performing is a full scan of your device. Scan your system for threats using a good cybersecurity program such as Gridinsoft Anti-Malware. This will provide clarity and insight into whether the threat came from the infected device.
- Next, change your passwords. Whether or not you have malware on your device, intruders already have compromised your accounts. We recommend changing your passwords to prevent attackers from accessing your accounts. Please avoid reusing passwords across sites. Consider using a password manager for unique alphanumeric passwords and to detect spoofed websites.
- Enable MFA or 2FA. 2FA is an effective line of defense against unauthorized access. The attacker must enter a confirmation code if the account login and password are compromised. Since this code is usually sent to your other devices, it reduces the chance of an attacker gaining access to the account.
- Report stolen or lost cards. We strongly recommend contacting your bank ASAP if you lose your plastic bank card. Bank employees will block the card, thus preventing intruders from using it. You can also request to have your card reissued on your bank’s mobile app. It will take a few minutes; you can link the new card to Apple Pay or Google Pay and continue using it.
- File a report with the FTC. You’ll need it to obtain a seven-year fraud alert from the credit bureaus and remove fraudulent accounts from your credit file. You can file another report with your local law enforcement agency only if your creditors demand it or you know the identity thief personally. You can dispute wrong information on your credit report under the Fair Credit Reporting Act. If the reporting agency doesn’t fix it within 30 days, file a complaint with the Consumer Financial Protection Bureau.
- Be careful of phishing emails. It is crucial to keep a close eye on your email inbox. Opportunistic cybercriminals know that many individuals whose accounts have been breached expect to receive some form of communication regarding the incident. These scammers will take advantage of the situation by sending out fake emails that trick you into providing your personal information. It is, therefore, essential to be vigilant and cautious when receiving such emails.
In addition to the above, we have a article dedicated to Identity Theft traits. In it, we describe how to protect against Identity Theft in more detail.




