On February 1, 2024, a post on a Darknet hacker forum selling Hewlett Packard Enterprise data appeared. Threat actor known as IntelBroker claims hacking into the company’s network and grabbing a whole lot of data, including access tokens and passwords. The company themselves acknowledges the breach, but cannot confirm any cybersecurity incidents happened in the recent time.
Hewlett Packard Enterprise Hacked
A post on the infamous BreachForums published on February 1 offers to purchase an extensive database, leaked from Hewlett Packard Enterprise (HPE) internal network. The seller, known under the name IntelBroker, claims hacking into the network and obtaining the said data. That means the company has suffered a new security breach, or the hacker was present in the network for quite some time.
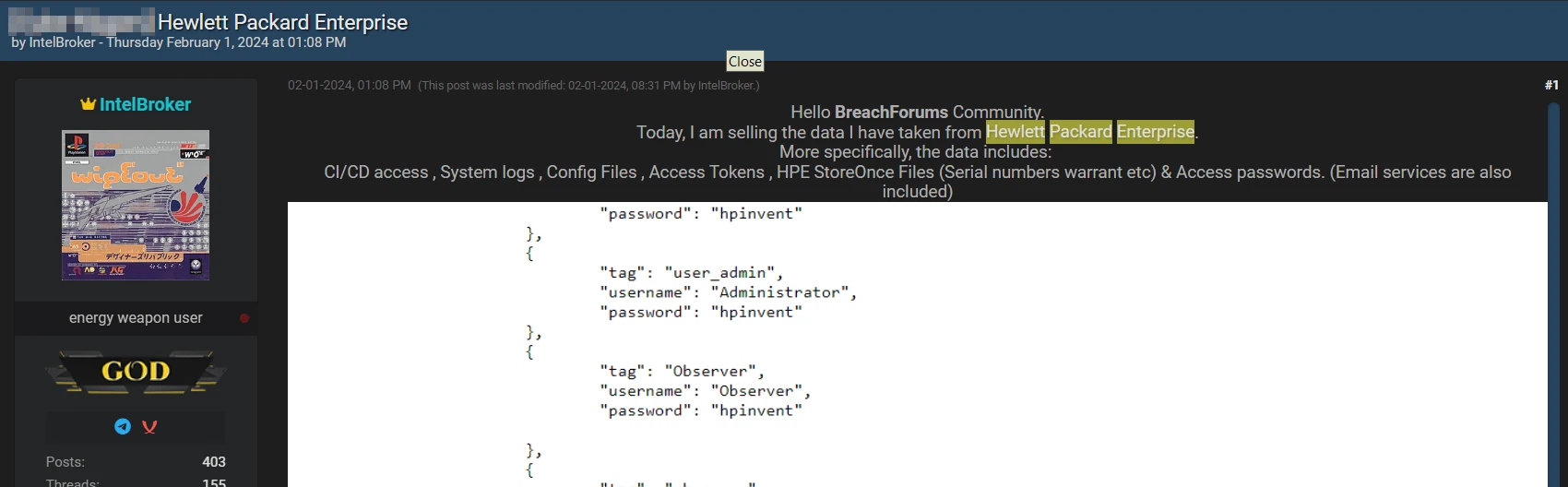
As it usually happens with Darknet forum posts offering to buy leaked information, there are several screenshots attached as evidence. Among the leaked data types, hacker claims CI/CD access, system logs, config files, access tokens, HPE StoreOnce files and access passwords. Albeit being representative to the types of data claimed in the leak, the screenshots do not include any data that allows identifying the time frame, e.g. there is no way to find how old this breach is.
As I’ve mentioned in the introduction, HPE knows about the data posted on the forum and investigates the case. At the same time, representatives of the company do not have any evidence of a cyberattack or a security breach over the last time.
Data Leak, But No Ransomware
The fact that the attack that leaked extensive amounts of data may sound absurd, considering that there is typically a ransomware deployment that finalizes the attack. Though, such an approach is not new: adversaries may practice leak-only attacks to speed up the overall process or avoid possible detection. In some cases, this works as the way to get at least something from the attack, when the security manages to block malware.
Still, there is a positive part of this story – no customer data appears to be involved. Both what is claimed and things that appear on the screenshots are purely internal data. And this is good not only to the HPE customers, as the company itself has much less headache notifying the ones whose data have been leaked.
Any Relation to HPE Corporate Email Accounts Breach?
Despite the company’s representative saying that no cyberattacks were detected, there apparently was one that can be a culprit. Back in mid-January 2024, HPE reported that their corporate email accounts were hacked by APT29, a threat actor related to Russian SVR. The breach itself took place in May 2023, with the fact of the adversary having access to the environment acknowledged on December 12, 2023.
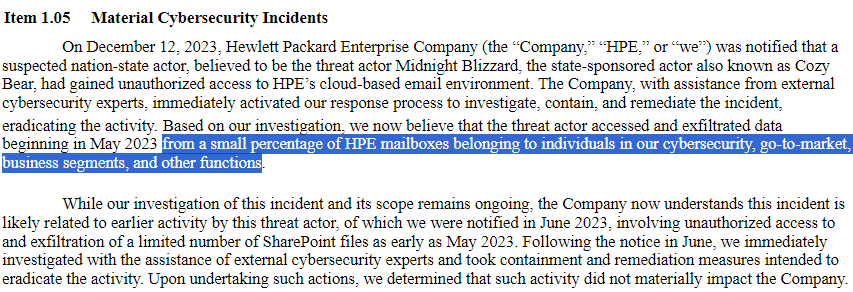
Why can this data be sourced from this old breach? The official company note regarding the case mentions a selection of data categories, which matches with what we see in the BreachForums post. More specifically, the company talked about hackers accessing several mailboxes of employees of their cybersecurity, go-to-market, business segment and several others. Logs, configs and access tokens is a normal occurrence in those emails, though there could have also been access to customer data. Nonetheless, that won’t be much of a surprise if the ongoing investigation will lead to the past APT29 hack.




