A security vulnerability loophole discovered by cybersecurity experts has revealed that decentralized social network Mastodon contains a critical vulnerability. Also, the flaw could potentially allow attackers to gain unauthorized access and take control of user accounts. Fortunately, the fix is already available.
Mastodon Account Takeover Vulnerability Published
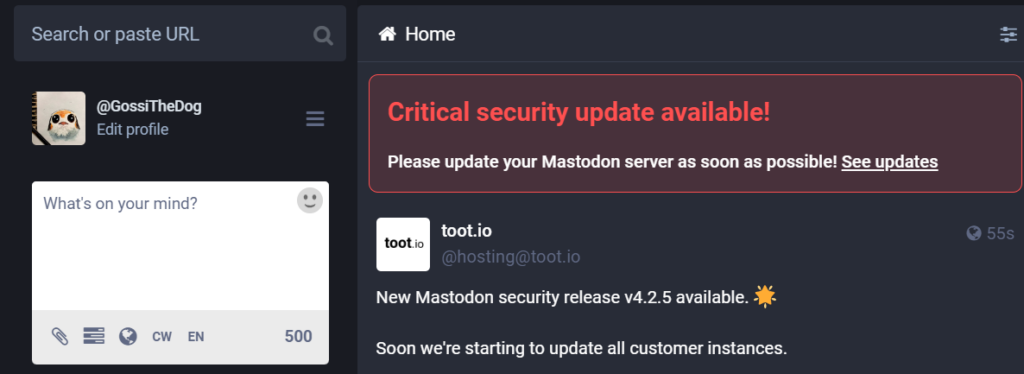
Given the potential impact and the ease with which it can be exploited, CVE-2024-23832 has been assigned a critical severity rating of 9.4 out of 10. At the heart of the vulnerability is a flaw in the way Mastodon processes user authentication. Specifically, the issue lies in the handling of session tokens, which can be manipulated by attackers to impersonate legitimate users. Mastodon versions 3.1.2 through 3.3.0 and 4.0.x versions before 4.0.13, 4.1.x versions before 4.1.13, and 4.2.x contain this vulnerability.
(Source: Kevin Beaumont)
Attackers can exploit this flaw by sending a malicious request to the affected application. If successful, the attack could lead to unauthorized code execution on the server, granting the attacker the ability to manipulate or access sensitive data. The potential impact of this vulnerability is far-reaching. Attackers could exploit this trick to carry out several unauthorized actions. Also, they could post content, access private messages, and even change account settings without the user’s knowledge or consent.
Patch Deployment
The patch was made available as part of a new Mastodon release, which administrators of Mastodon instances could download and install. Detailed installation instructions and support were provided to ensure a smooth update process. The vulnerability has been fixed in the versions past 3.3.1. Users of affected instances are urged to upgrade to this version or later.
Mastodon plans to wait until February 15, 2024, before disclosing more technical details about the vulnerability. This delay is intended to give admins enough time to update their server instances and prevent exploitation. The Mastodon team has also committed to continuous monitoring of the network for any unusual activity, ensuring that any potential exploitation of the vulnerability is swiftly addressed.
Security Tips
Upon discovery, the Mastodon development team was quick to respond, acknowledging the severity of the issue and initiating immediate steps to mitigate the risk. Therefore, following what they say is crucial: install the update, and you will be fine. The recent wave of account hijackings in X/Twitter is pretty representative on what kind of mess such a vulnerability can make.
Being aware of recent cybersecurity news is another part of staying safe. 10 minutes of news reading per day may save you a lot of time solving that one vulnerability you’ve missed. This, in combination with fast reaction times and proper security tools will get you covered for the majority of situations.





