A new campaign named “Commando Cat” uses a Docker API vulnerability. It uses Docker to gain initial access to a system and then deploys a series of malicious payloads. This leads to cryptocurrency mining on compromised hosts.
Docker API Vulnerability Exploited
Investigators have discovered a new malware campaign aimed at Docker API endpoints. The malware is called Commando Cat, and its purpose is to take advantage of misconfigured Docker APIs, allowing it to run harmful commands on the affected containers. According to a report, Commando Cat has nine distinct attack modules that can carry out several tasks. These include downloading and executing additional payloads, scanning for open ports and vulnerable services, stealing credentials and sensitive data, mining cryptocurrencies, launching distributed denial-of-service (DDoS) attacks, and spreading to other containers and hosts.
The malware campaign was first detected in January 2024. This marks the second Docker-related campaign identified in 2024, following the previous discovery of the malicious deployment of the 9hits traffic exchange application. Then, specialists observed a spike in malicious activity from a single IP address from China. The researchers traced the source of the attack to a Docker container running on a cloud server infected by Commando Cat. The malware had accessed the Docker API through an exposed port and executed a series of commands to download and run its modules.
Commando Cat Attacks Docker
Commando Cat delivers its payloads to exposed Docker API instances via the Internet. The attacker instructs Docker to fetch a Docker image known as “cmd.cat” from the project “Commando”, which generates Docker images with the necessary commands for execution. This choice of image is likely an attempt to appear benign and avoid suspicion. After creating a container, the attacker uses the “chroot” command to escape from the container onto the host’s operating system. The initial command looks for services “sys-kernel-debugger,” “gsc,” “c3pool_miner,” and “dockercache,” which are all created by the attacker after the infection.
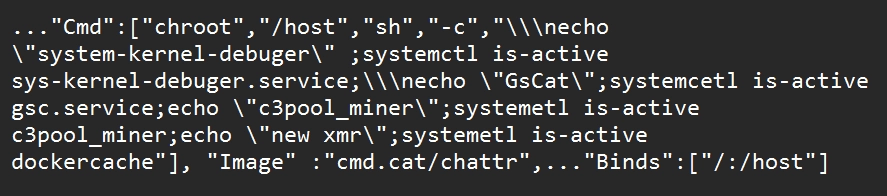
Experts also believe the attacker avoids competing with another campaign by checking for the “sys-kernel-debugger” service. After these checks are passed, the attacker reruns the container with a different command, infecting it by copying specific binaries onto the host. This process involves renaming binaries to evade detection, a common tactic in cryptojacking campaigns. The attacker also deploys various payloads with parameters like “tshd,” “gsc,” and “aws.”
The final payload is delivered as a base64 encoded script. It deploys an XMRig crypto-miner and “secures” the Docker install on the infected host. Next, it removes all containers with a special command, and then it removes all containers without a command containing chroot. It kills other mining services before setting up its miner. Further, malware uses a systemd service to achieve persistence for the XMRig stager. It hides the docker-cache and docker-proxy services using the hid script. Finally, Commando Cat blackholes the Docker registry to eliminate the risk of competition.
Safety Tips
Protecting against a sophisticated threat, like Commando Cat is, appears to be a challenging affair. Its advanced detection evasion methods make it hard to detect for classic security solutions. But there are still enough tricks to make this malware less of a threat.
- Use Firewall. You can configure your firewall for strict packet filtering. Only allow necessary network connections and block all others. You can also limit outbound connections from containers to prevent unauthorized access.
- Employ XDR. Extended Detection and Response systems can analyze network traffic and identify anomalies. Suspicious activity should trigger warnings or alerts about potential intrusions. So, you can utilize network activity monitoring tools to detect unusual traffic related to the Docker API.
- Training and Awareness. Training users on secure Docker usage and basic cybersecurity practices is essential to prevent most problems. Educated users can help prevent social engineering and mishandling of data.




