The NCC Group warns of a spike of Clop ransomware attacks (hack group also known as TA505 and FIN11), which exploits a vulnerability in SolarWinds Serv-U.
Most of them start off by exploiting the CVE-2021-35211 bug in Serv-U Managed File Transfer and Serv-U Secure FTP. This issue allows a remote attacker to execute commands with elevated privileges on the affected server.
SolarWinds fixed this bug back in July 2021, after discovering the “only attacker” who used this vulnerability in attacks. Then the company warned that the vulnerability affects only clients who have enabled the SSH function, and disabling SSH prevents the exploitation of the bug.
As the NCC Group now reports, Clop operators have also begun to exploit the vulnerability in their attacks, although they typically relied on explanting 0-day issues in Accellion and phishing emails with malicious attachments. Now attackers use Serv-U to launch a subprocess under their control, which allows them to run commands on the target system. This paves the way for malware deployment, network reconnaissance, and lateral movement, creating a solid platform for ransomware attacks.
Certain errors in the Serv-U logs are a characteristic sign of exploitation of this vulnerability. So, the error should look like the following line:
‘EXCEPTION: C0000005; CSUSSHSocket::ProcessReceive();’
Another sign of exploitation of the bug are traces of the PowerShell command used to deploy Cobalt Strike beacons on the affected system.
The NCC Group has published a system administrator checklist that can check systems for signs of compromise:
- check if your Serv-U version is vulnerable;
- find the DebugSocketlog.txt file for Serv-U;
- Look for entries such as ‘EXCEPTION: C0000005; CSUSSHSocket::ProcessReceive();’;
- check event ID 4104 in the Windows event logs for the date and time of the exception error, and look for suspicious PowerShell commands.
- check for the captured scheduled RegIdleBackup task;
- CLSID in COM should not be set to {CA767AA8-9157-4604-B64B-40747123D5F2};
- If the task contains a different CLSID: check the contents of the CLSID objects in the registry, the returned Base64 strings could be an indicator of compromise.
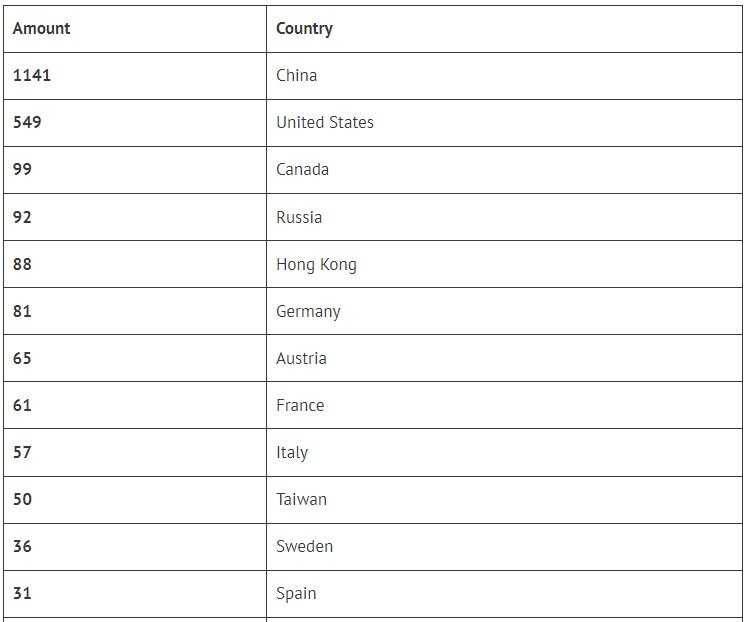
The researchers note that most of the vulnerable Serv-U FTP systems are in China and the United States.
Let me remind you that I wrote that the Cyber police of Ukraine arrested persons linked with the Clop ransomware, but also that Clop ransomware continues to work even after a series of arrests.