Virus:Win32/Grenam.VA!MSR is a type of malware that can stealthily get into the system and establish remote connections. It allows attackers to access the system and remotely perform keylogging and information-gathering functions. This malware usually spreads through fake software downloads and on compromised websites.
Viruses like Grenam can be disguised as legitimate software. The specific capabilities and behaviors of the malware may differ depending on the variant. However, it is commonly associated with the delivery of other malicious software, making it a severe threat to the security and privacy of computer systems.
Virus:Win32/Grenam.VA!MSR Overview
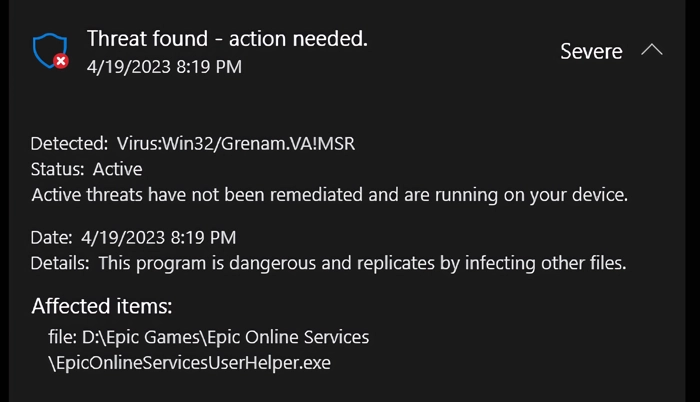
Virus:Win32/Grenam.VA!MSR is a generic detection name used by Microsoft Defender Antivirus to identify a type of malware that belongs to the Grenam family. This family consists of backdoors and Remote Access Trojans (RATs). These types of malware are designed to provide unauthorized remote access to a target system. It is used to steal sensitive data, install malicious software, or cause other damage.
Grenam malware can infiltrate a system through various methods, but the most common ones include malicious advertising and pirated software. Once the malware is installed, it uses anti-analysis and defense software evasion features to avoid detection by antivirus programs. As a result, it can remain undetected on a system for long periods, giving access to more dangerous malware.
Technical Analysis
Let’s look at one of the Virus:Win32/Grenam.VA!MSR samples to understand how it works. Once the malware enters the system, it executes initial dropper files such as C:\DllLoader.exe and C:\Documents and Settings\
Moreover, some users report that their desktop wallpaper was changed after detecting this malware.

Establishing Persistence
To ensure continuity and maintain a persistent presence on the infected machine, it requesting the following permissions by calling for a WinAPI function:
SE_LOAD_DRIVER_PRIVILEGE
The malware may exploit system vulnerabilities or use stolen credentials to gain higher privileges necessary for deeper system access and modification. The malware often manipulates other system settings or uses exploits to elevate privileges.
After finishing with persistence, Grenam starts rummaging through registry keys to collect info about the system. It mainly concentrates on data like CPU, display resolution, installed programs, etc, without getting into user data.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services
Defense Evasion
To evade detection from antivirus software and system monitoring tools, the malware employs techniques such as obfuscating its files and operations, hiding windows, and masquerading its processes. It also uses XOR and RC4 to encode data, modify file attributes, and renames its files with misleading extensions.
These keys store advanced Windows Explorer settings like hidden files, file extensions, and title bar paths, system-wide policies affecting user accounts, rights, security options, and system behaviors, information on system services, and Shell Execute Hooks that modify Windows Shell behavior.
Command and Control
Finally, once it has the required access and control, the malware can execute actions as directed by its operators, including data exfiltration, further infections, or using the host for additional attacks. The malware opens backdoors and communicates with external servers via TCP and UDP to known bad IPs to establish control.
TCP 23.216.147.62:443
TCP 23.216.147.64:443
UDP a83f:8110:4170:706c:6963:6174:696f:6e50:53
This is a clear indicator of C2 activity. The malware infects other executable files or uses network connections to spread to additional systems within the network environment. It infects files and possibly uses network drives to spread itself.
How To Remove Virus:Win32/Grenam.VA!MSR?
If you are struggling with Virus:Win32/Grenam.VA!MSR, I suggest using GridinSoft Anti-Malware. This software has advanced features that can effectively find and neutralize malware from your system. In addition to removing existing threats, this solution provides long-term protection to prevent unwanted effects from other malware.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.