PUA:Win32/Presenoker is an adware designed to make money by showing intrusive advertisements and collecting data. This malware can take control of your web browser and send you to advertising pages. The majority of them will be questionable, without even a slight tint of relevance.
It is often disguised as legitimate cracked software, driver finder, or tweaker. This malware can also steal some information.
PUA:Win32/Presenoker Overview
PUA:Win32/Presenoker is adware designed to generate revenue through intrusive advertisements. In addition to malvertising, it can steal users’ data, including search history, cookies, and other sensitive information. Although it collects basic system information, it is only about fingerprinting the system; it does not touch passwords or session tokens. Almost all instances of this malware are connected to websites that redirect users to advertising pages. While some pages it advertises are legitimate, others are questionable, significantly degrading the user experience.
PUA:Win32/Presenoker often spreads under the guise of cracked legitimate software, tricking users and infiltrating their devices without their consent. The malware also masquerades as a laptop driver finder or tweaker. However, almost anything downloaded that is not from an official website can lead to Presenoker infection.
Presenoker Technical Analysis
Let’s break down its behavior based on the PUA:Win32/Presenoker sample analysis. As I said above, malware infiltrates the system under the guise of legitimate software. In our case, it is a free but Windows kernel research tool.
Once on the system, malware seeks persistence. To do so, it performs standard actions—it creates driver files, adds appropriate registry entries, and obtains the necessary permissions. Among the latter is the ability to modify the kernel to execute programs at system startup.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SafeBoot\Minimal\bajejyicthbeby.sys
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SafeBoot\Minimal\bhrzxcfdwsfytp.sys
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SafeBoot\Minimal\boalxrinybzftbduk.sys
The malware created multiple registry entries for each file to ensure its drivers and services were loaded in “Minimal Safe Mode”, a diagnostic mode of Windows with only essential functions.
C2 Communication
Presenoker takes multiple HTTP requests made to various URLs, including ww1.epoolsoft[.]com and www.epoolsoft[.]com, suggesting communication with a command-and-control (C2) server. TCP connections are established to several IP addresses on ports 80 and 443, indicating potential communication with external servers.
TCP 63.143.32.86:80
TCP 64.190.63.136:80
UDP a83f:8110:0:0:6076:c7a:e801:0:53
The malware probably receives adverts through some channels (opening some of these addresses redirects to the advertised websites).
Presenoker Advertising
As I said before, the primary purpose of this kind of application is advertising. Usually, these ads often promote online scams, unreliable or hazardous software, and malware. When clicked on, some ads can execute scripts to install or download software without the user’s consent.
In rare cases, users will see what looks like a legitimate internet search website like Yahoo or Bing, but with changed results. The URLs below are the intermediary sites that appear in the URL bar during this redirection. It looks like they gather the information about the search queries and God knows what else.
hxxp://www.epoolsoft[.]com/PCHunter_StandardV1.56=DE8D8650A2322F6FBD61DC24EA6CE9703EDC1C1ABBA4523E236D3DE26CFD2B49C08503DEEA5AEDF515739967BDA959FD
hxxp://ww1.epoolsoft[.]com/?sub1=39aa0efd-0311-11ef-af09-729c7805264a
hxxp://www.epoolsoft[.]com/pchunter/pchunter_free
This website contains links that, when clicked on, will redirect you using adsensecustomsearchads.com
Defense Evasion
Malware may use IsDebuggerPresent and SetWindowsHookExW to evade detection and employ hooking techniques. The PE file has a section (not .text) that is highly probable to contain compressed code using a zlib compression ratio of less than 0.011. It also checks for debuggers, including window names and unique Hardware/Firmware, and can detect virtual machines. Moreover, it may use evasive loops to hinder dynamic analysis and check whether the current process is under debugging.
HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\SystemBiosVersion
HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\VideoBiosVersion
As the name says, these keys contain BIOS information. That is enough data to understand whether the system is a virtual machine or some other modified environment.
How To Remove PUA:Win32/Presenoker?
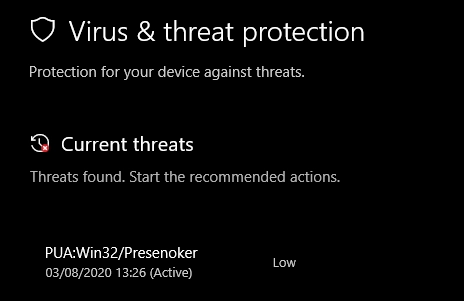
To remove PUA:Win32/Presenoker you need to use a powerful antimalware solution. GridinSoft Anti-Malware will be an excellent choice to clean your system from unwanted software. In addition to cleaning, this solution will prevent future infections on your device.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.