Cybersecurity experts from SafeBreach have found a new, previously undocumented and “undetectable” PowerShell backdoor, which hackers actively use and has been used to attack at least 69 targets.
Let me remind you that we also wrote that Germans Interested in the Situation in Ukraine Are Attacked by the PowerShell RAT Malware.
The backdoor spreads through spear phishing, as part of malicious Word documents that are usually disguised as job offers. When such a document is opened, a macro is triggered within it that delivers the updater.vbs PowerShell script to the victim’s computer, which creates a scheduled task claiming to be part of a Windows update.
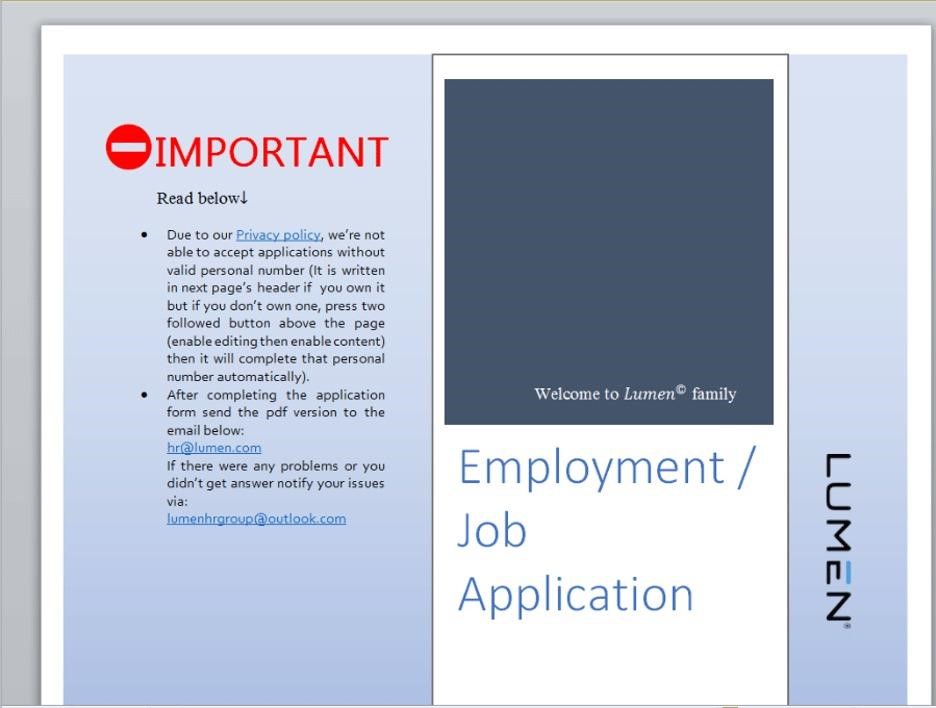
Bait from hacker’s letter
The VBS script executes two other PowerShell scripts (Script.ps1 and Temp.ps1), which are stored obfuscated inside the malicious document itself. When SafeBreach analysts first discovered these scripts, none of the products featured on VirusTotal identified them as malicious.
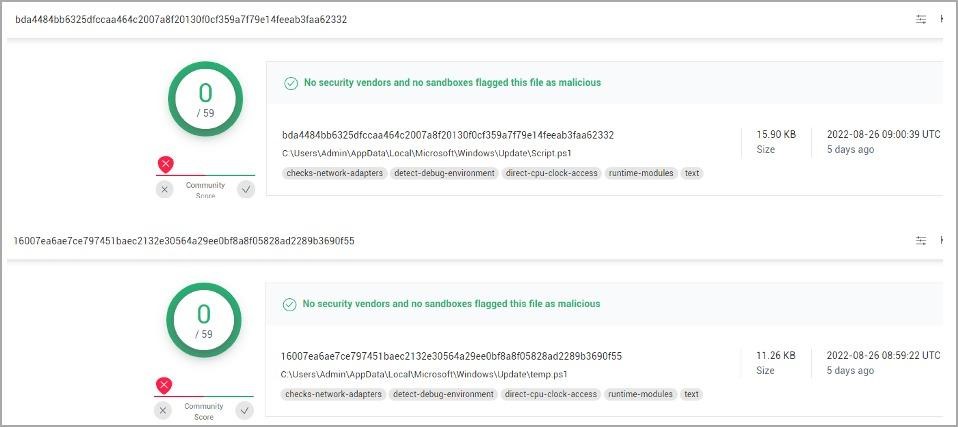
Script.ps1 connects to the C&C servers of the attackers, sends the victim ID to its operators, and then waits for further commands, which it receives in encrypted form (AES-256 CBC). Based on the count of such identifiers, the analysts could conclude that about 69 victims were registered on the attackers’ control servers, which probably corresponds to the approximate number of hacked computers.
The Temp.ps1 script, in turn, decodes the commands received from the server as a response, executes them, and then encrypts and uploads the result via a POST request to the control server.
The experts created a script that deciphered the commands of the malware operators, and found that two-thirds of them were intended to steal data, and the rest were used to compile lists of users, files, delete files and accounts, and also compile lists of RDP clients.
Researchers believe that this PowerShell backdoor seems to be created by some previously unknown attackers, and so far there is too little data to talk about the attribution of these attacks.