Cybersecurity experts have released a decryptor for the Akira ransomware. It will allow victims who encounter attacks to decrypt their files without paying a ransom.
Akira ransomware decryptor released to the public
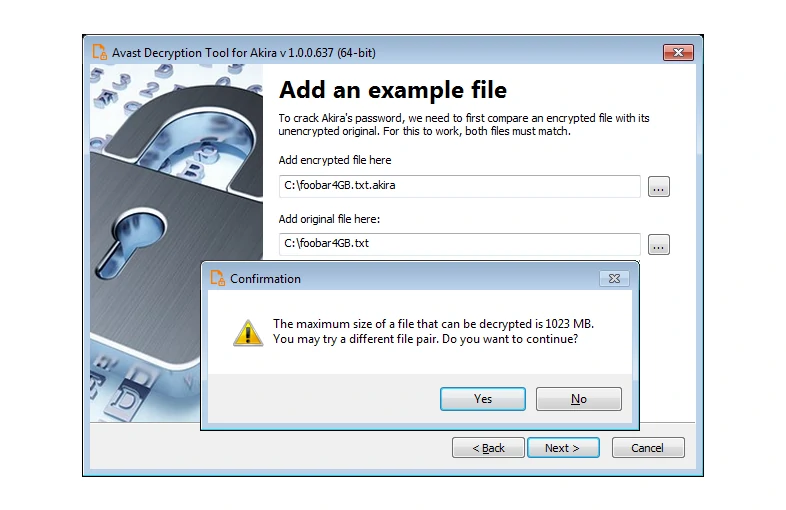
Cybersecurity firm Avast recently released a free decryptor for Akira ransomware. This tool can help victims recover their data without paying any money to fraudsters. The decryptor has two versions, 32-bit and 64-bit. Specialists recommend using the latter because the program consumes much system memory to crack passwords. For decryption, the tool must generate a decryption key based on two identical files, one of which is encrypted. In addition, choose as large-size files as possible because this will influence the maximum size of the decrypted files.
The fact that the decryptor was released shows that ransomware developers picked a vulnerable encryption algorithm. Even if it is AES-256 or RSA versions with an even bigger number of potential keys, the encryption process flaws may mess all the things up. Hackers have probably implemented the mechanism that allows malware to speed up the encryption – a pretty sensible characteristic. And this is what made it possible to find the fast decrypting option, instead of brute forcing all the trillions of possible keys.
What is Akira Ransomware?
Akira is a ransomware for Windows and Linux that has been available since March 2023. As a newcomer to the ransomware market, Akira made a name for itself by quickly picking up victims. It targeted organizations around the world in a variety of sectors. It is worth noting that there was another strain of ransomware, also known as Akira, in 2017. However, there is currently no evidence that the two are related. According to analysis, the malware uses a symmetric key generated by CryptGenRandom. It is then encrypted with the associated RSA-4096 public key and added to the end of the encrypted file. Since the ransomware operators are the only owners of the RSA private decryption key, this should have restricted the decryption of the files without paying a ransom.
The researchers also found similarities between Akira and the now-defunct ransomware Conti v2. It suggests that the authors used leaked Conti ransomware source code. Similarities include the file type exclusion list, directory exclusion list, and file tail structure. Although the Windows and Linux versions of the Akira ransomware are very similar in Щthe way they encrypt devices, the Linux version uses the Crypto++ library instead of the Windows CryptoAPI.
Should I Not Fear Akira Ransomware Anymore?
Undoubtedly, getting your files back for free is good news. Yet this does not mean that the threat is entirely over. The main problem after encrypting files is the leakage of confidential information. Akira operators claim that they will put any valuable information up for sale on the Darknet if the victim does not pay. This could be proprietary code, internal financial data, or corporate information. In addition, there is still an arms race between cybercriminals and security services. It means that operators are likely to overhaul the encryption mechanism sooner or later.
Use advanced anti-malware protection
We recommend using a set of measures that include EDR, XDR, SIEM, and SOAR. These are potent tools against ransomware. Thus, EDR monitors endpoint activities, and XDR extends detection and response capabilities. SIEM aggregates security event logs, and SOAR automates incident responses. Together these technologies provide advanced threat detection and centralized management capabilities to prevent ransomware incidents.
Control over all malware spreading methods
In addition to comprehensive protection, keeping an eye on potential entry points is crucial. No matter how strong an enterprise’s cyber defense is, one human error can jeopardize the entire company. Cyber hygiene is the first line of defense because human error causes most incidents. Organizations should update software regularly, use web filtering and utilize network and email security measures. Another essential component is training employees on safe email practices, subscribing to threat intelligence, and having an incident response plan. A multi-layered approach is crucial for minimizing the risk of malware infections and protecting sensitive data.


