Analysts of the Sekoia company reported that the Russian DDoSia hacker project grew by 2400% in less than a year. That project pays volunteers to participate in attacks on Western organizations. More than 10,000 people are currently involved in the attacks.
DDoS-for-hire services became particularly popular over the last years. We recently did the review of of the most popular ones. And if you are interested in criminal records, Cloudflare Recorded the Most Powerful DDoS Attack in the History of Observations.
What is DDoSIA project?
DDoSIA project appeared back in fall 2022. Then the Radware company announced that the project was launched in August 2022 by the group NoName057(16). The latter, however, appeared only in March 2023, as a pro-Russian hacker group. They created a DDoSia project in Telegram, where the operators posted a link to GitHub with instructions for potential “volunteers”.
These “volunteers” were offered to register via Telegram to receive a ZIP-archive with malware (dosia.exe). Archive contains a unique ID for each user. The most interesting feature of this project was the fact that participants could link their ID with a cryptocurrency wallet and receive money for participating in DDoS attacks. And the payment was proportional to the capacities provided by the concrete participant.
As Sekoia experts say now, the DDoSia platform has grown significantly over the past year and now has about 10,000 active participants who contribute to DDoS attacks. At the same time, more than 45,000 people have already subscribed to the main Telegram channels of hackers (all seven of them). In addition to just comments (what to do with DDoSia ataks), the platform has improved its toolkit and Tebera welcomes banaries for all OS programs, selling audience controls.
How that works?
Registration of new users is fully automated through the Telegram bot, which supports only the Russian language. New participants start by providing a TON (Telegram Open Network) wallet address to receive cryptocurrency, and in response the bot creates a unique client ID and provides a text file for help.
Next, new participants receive a ZIP-archive containing a tool for attacks. As of April 19, 2023, the archive included the following files:
- d_linux_amd64 – executable file ELF 64-bit LSB, x86-64;
- d_linux_arm — 32-bit executable file ELF LSB, ARM;
- d_mac_amd64 — Mach-O x86-64 64-bit executable file;
- d_mac_arm64 — Mach-O arm64 64-bit executable file;
- d_windows_amd64.exe — executable file PE32+ (console) x86-64 for Microsoft Windows;
- d_windows_arm64.exe — executable file PE32+ (console) Aarch64 for Microsoft Windows.
To perform these useful loads, the text file with the client ID must be placed in the same folder as the payloads themselves, which makes it difficult for unauthorized execution of files by IT experts and other «outsiders».
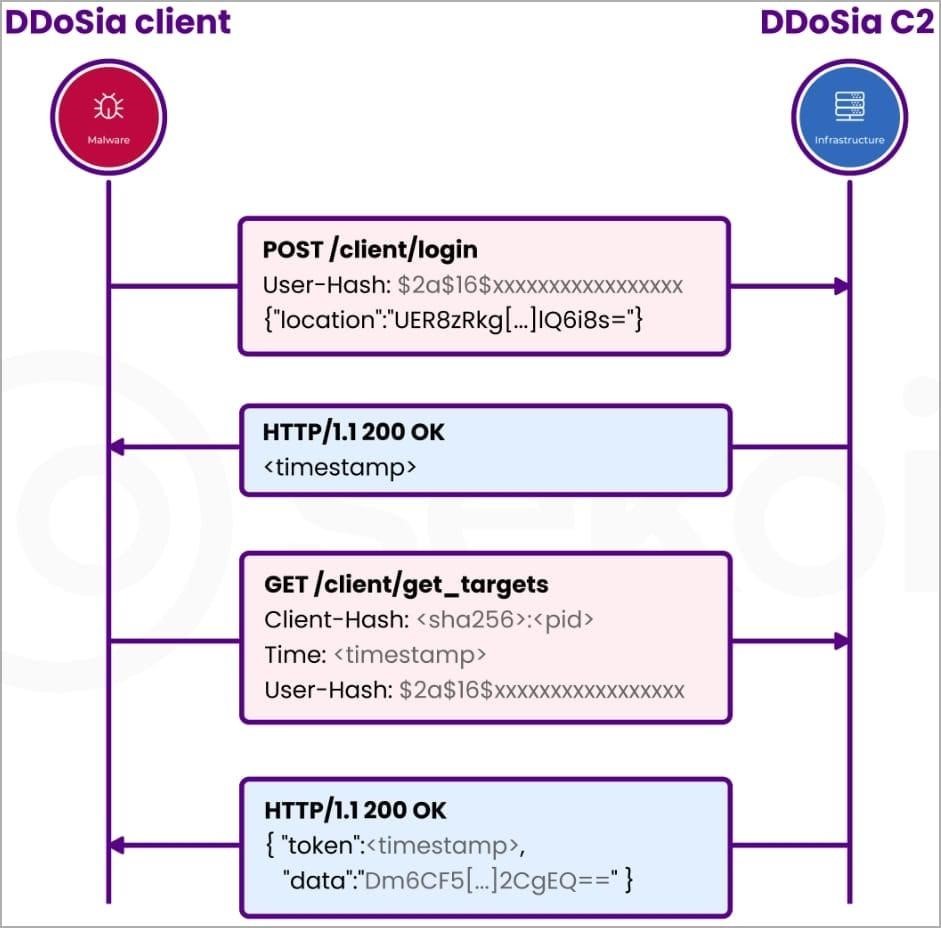
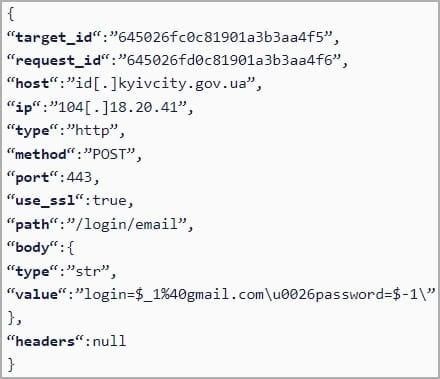
After that, the DDoSia client launches a command line invitation. There, participants receive a list of targets in an encrypted form. They can pick a specific target to attack. Experts studied the 64-bit Windows executable file and found that it is a binary written in Go, using AES-GCM encryption algorithms to communicate with the control server. The C&C server transmits the DDoSia target ID, host IP address, request type, port and other attack parameters to the client in an encrypted form, and all of this is then decrypted locally.
DDoSIA Massively Attacks Lithuania, Ukraine and Poland
Sekoia researchers collected data about some DDoSia targets for the period from May 8 to June 26, 2023, which were communicated by the server controlling the attacks. Basically, the groups and their «volunteers» were organizations from Lithuania, Ukraine and Poland, which accounted for 39% of the total activity of the project.
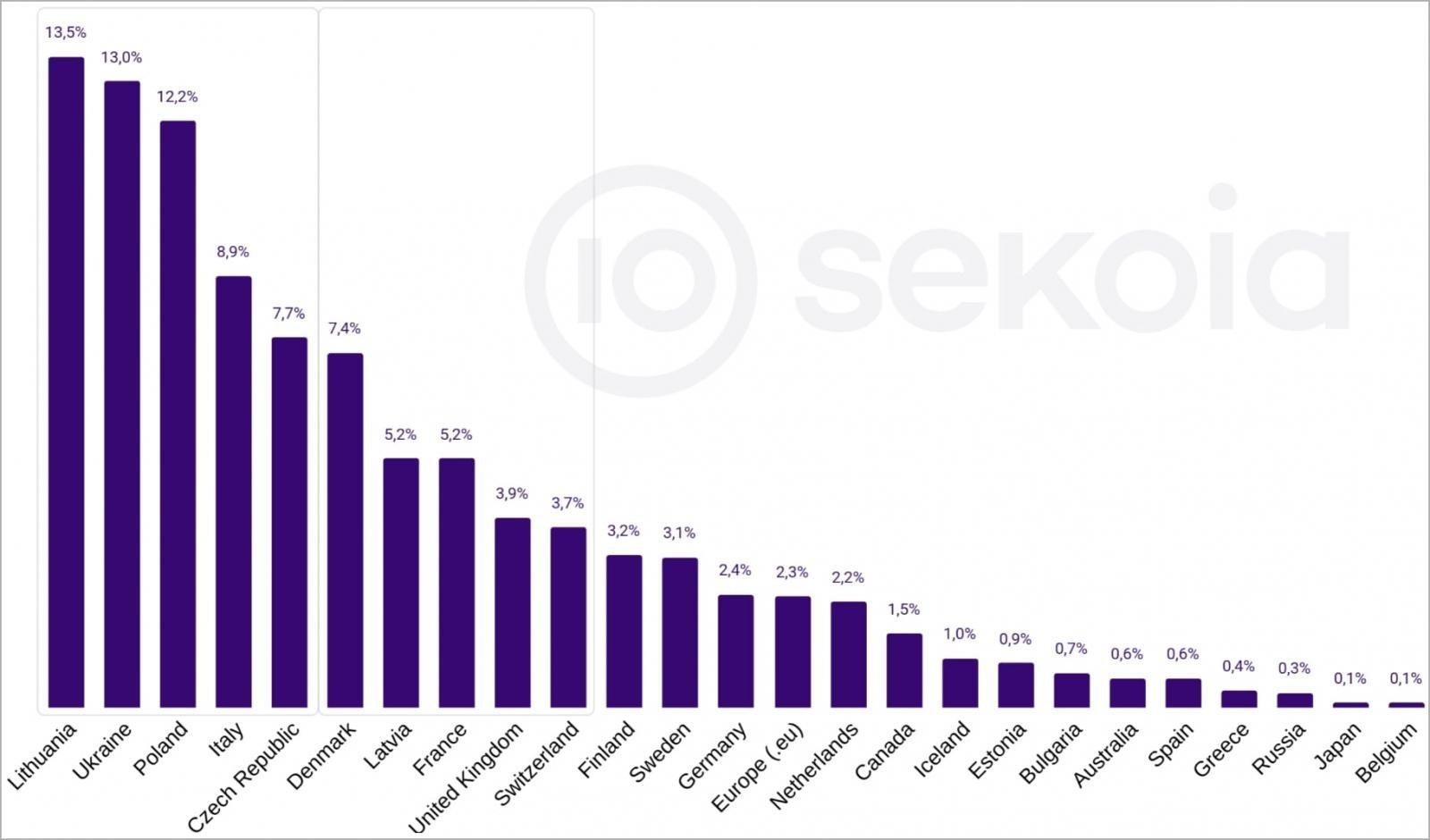
Analysts noted that DDoSia attacked a total of 486 different sites. In May and June, crooks focused on attacks on educational platforms, possibly to disrupt end-of-school exams. In summary, the DDoSia project has already reached a sufficiently large size to create serious problems for its targets. Who knows what will happen when they will grow even more?




