Researchers uncovered a vulnerability in Apple Silicon processors, dubbed GoFetch. It allows attackers to extract secret keys from Mac computers while performing widespread cryptographic operations. Notably, it is practically impossible to patch the flaw as it stems from the microarchitecture of the processor.
Apple Silicon Vulnerability Allows Hackers to Extract Encryption Keys
Researchers have discovered a vulnerability in Apple’s self-made M-series processors. Under certain conditions, this vulnerability allows cryptographic information to be stolen from the processor cache. Modern computing devices use a hardware optimization called the DMP (data memory-dependent prefetcher). It reduces latency between the main memory and the CPU by predicting memory addresses and loading their contents into the CPU cache before they’re needed. By exploiting the flawed mechanism of cryptography operations handling, attackers can recover private encryption keys piece-by-piece.
Unlike more common vulnerabilities, developers can’t directly fix this flaw with a software patch. This issue at hand is linked to the microarchitecture design of the silicon itself. The only way to mitigate this vulnerability is to build defenses into third-party cryptographic software. Yet this workaround may have serious performance impact, with older M1 and M2 chips suffering the worst losses.
Understanding GoFetch Attack
Let’s take a closer look at how this attack works. The attack is called GoFetch, and relies on classical and quantum-resistant encryption algorithms. As mentioned, it exploits a vulnerability in Apple processors related to DMP (data memory-dependent prefetcher). This next-generation prefetcher is only used in Apple and Intel Raptor Lake processors, loading memory contents into the cache before they are needed. So, GoFetch can be exploited if the target cryptographic operation is a malicious application with standard user privileges. By the way, these privileges are available to most applications running in the same CPU cluster.
The vulnerability stems from the prefetcher’s ability to load data into the CPU cache with a pointer to load other data. DMP sometimes confuses memory contents and loads the wrong data into the CPU cache. The problem is that the vulnerability completely neutralizes the effect of constant-time protection. This should by design protect against side-channel and cache-related CPU attacks. This protection ensures that all operations take the same time, regardless of their operands. However, due to the vulnerability, applications exploiting GoFetch can put sensitive data in the cache, and a malicious application can steal it.
How Dangerous It Really Is?
When executed on the same core cluster (efficient or performance) with cryptographic operations, GoFetch reaches its peak efficiency. As far as analysis shows, it can effectively hack both current and next-gen encryption techniques.
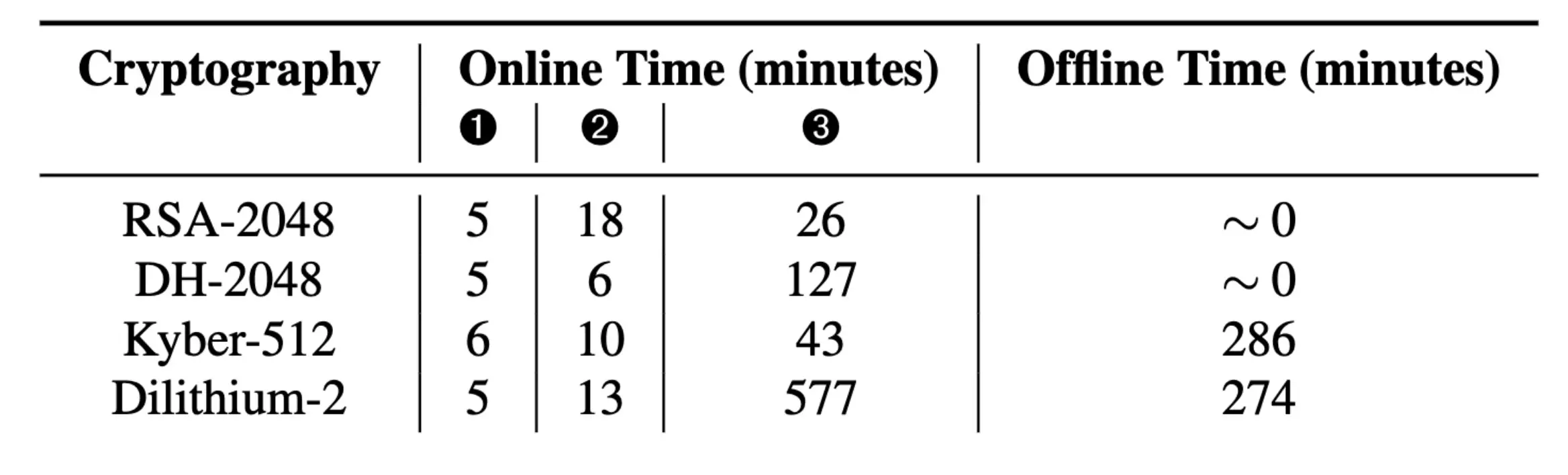
As for exact numbers, GoFetch takes less than an hour to extract a 2048-bit RSA key and just over two hours to extract a 2048-bit Diffie-Hellman key. An attack to extract the material needed to assemble a Kyber-512 key takes 54 minutes. The Dilithium-2 key would require about 10 hours, not counting the time needed to process the raw data offline.
Unpatchable Vulnerability
The main problem is that fixing this vulnerability by patching is impossible. This flaw sits in the Apple Silicon chip architecture. The only way out is through software protections and embedding patches in third-party cryptographic software, that avoids using the vulnerable mechanism. However, as I said, this will slow down cryptography operations on M1 and M2 and will throw a spanner in the developers’ work.
Aside from purely software workarounds, it is theoretically possible to run cryptographic processes on efficiency cores, which do not have DMP. Though this will impact performance as well, as E-cores were never meant to be fast, and the flawed mechanism itself brought quite a bit of speed-up. Experts emphasize that the performance drop will be felt if the affected software performs certain cryptographic operations only. At the same time, when working in browsers and many other types of applications, users will never notice changes.
It is worth noting that Intel Raptor Lake architecture (which includes 13th and 14th generation processors) does not have this vulnerability despite using the same prefetching mechanism as Apple’s M-series processors. The M3 processor is less susceptible, as it has a special “switch” that developers can use to disable DMP. However, it is still unclear how much performance degradation will occur when this functionality is disabled.



