A new phishing campaign has recently been discovered that uses GitHub to deliver Remote Access Trojans (RAT) STRRAT and Vcurms via a malicious Java downloader. ANY.RUN specialists have detected the active spread of these malicious programs and warn users against potential threats.
Short About STRRAT and Vcurms
STRRAT is a Java-based RAT, notorious for its ability to steal information. It’s primarily used to gather credentials from browsers and email clients, log keystrokes, and provide backdoor access to infected systems. Same as other remote access trojans, STRRAT also relies on stealthiness of its operations and detection evasion.
Vcurms, is another Java-based RAT, but with distinct operational tactics. It communicates with its command-and-control server via a Proton Mail email address and executes commands received through specific email subject lines. This malware carries the functionality of infostealer, capable of extracting data from various applications like Discord and Steam. Aside from this, it can grab credentials, cookies, and autofill data from multiple web browsers. It shares similarities with another malware known as Rude Stealer.
Attack Overview
ANY.RUN researchers say the attack begins with a phishing email convincing recipients to click a button to verify payment information. This action leads to the download of a malicious JAR file masquerading as a payment receipt. The downloaded file then launches two additional JAR files that activate both Vcurms and STRRAT trojans.
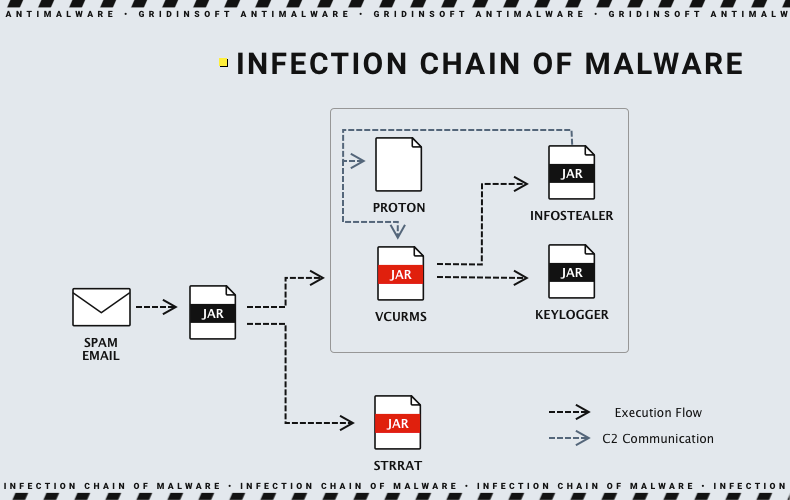
Both malware samples try to remain stealthy, using detection and analysis evasion techniques. Researchers found them using these specific tricks:
- Using legitimate services and tools – when attackers can use legitimate cloud platforms such as AWS and GitHub to store or distribute malware. Such a trick also complicates filtering network requests of malicious origin.
- Code Obfuscation – in which the source code of a program is converted into a form that makes it difficult to read. This is used to hide malicious functions from antivirus scanners and analysts. (By the way, the first JAR file received via email is obfuscated and downloads malware using a PowerShell command).
- Packing – where malicious code is compressed or “packed” together with some type of unpacking mechanism. This makes it difficult to analyze the code without executing the malware.
This is not the first time malware actors abuse GitHub or other developer platforms. Unfortunately, there are not a lot of options to mitigate this proactively: it is easy to masquerade the code and make it look innocent. GitLab administrators reacted to user complaints and removed the malicious repository, but this does not guarantee that there won’t be a comeback.
Sandbox attack analysis
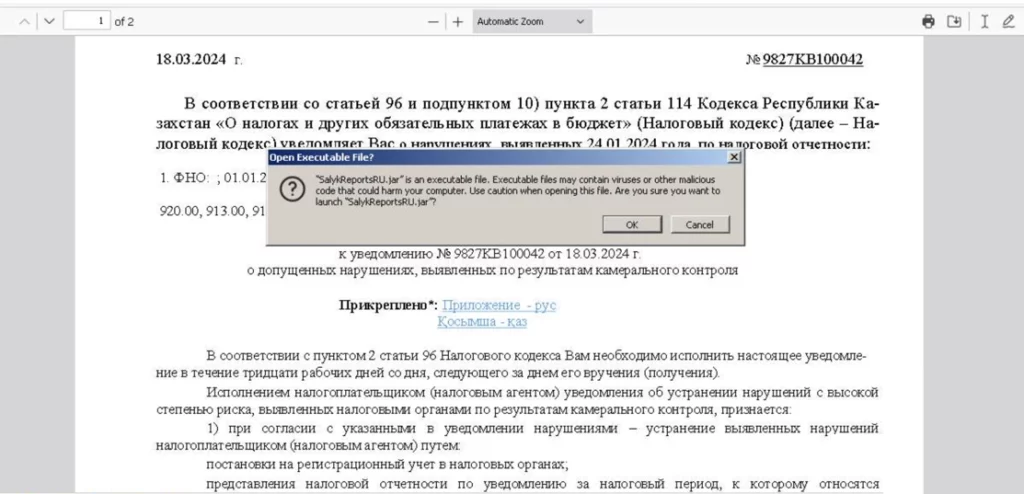
A phishing campaign begins by spreading the initial loader via phishing emails. The goal of these emails is to convince the user to download and run a malicious JAR file. This file acts as a primary loader that initiates a series of malicious actions on the infected machine.
Primary Loader
Once launched, the primary loader downloads a secondary malicious file from the aforementioned repository on GitHub. The file is launched using a command pointing to the Java file execution:
"C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\AppData\Local\Temp\64e8cb522a3a4664791c27512d94a911bc2fbcbae09b625976ff8ac6809819d3.jar"
Persistence and disguise
Then, malware creates a copy of itself in the AppData\Roaming directory and registers a task in the Windows scheduler to automatically restart every 30 minutes. Interestingly enough, malware tries to mimic the Skype application, judging by the name of the task it creates. This ensures the permanence of the malware on the system.
cmd /c schtasks /create /sc minute /mo 30 /tn Skype /tr "C:\Users\admin\AppData\Roaming\64e8cb522a3a4664791c27512d94a911bc2fbcbae09b625976ff8ac6809819d3.jar"
Collecting information about the system
Next, the malware gathers information about the system, including a list of disks and the presence of installed security programs, using the following commands:
cmd.exe /c "wmic /node:. /namespace:'\\root\cimv2' path win32_logicaldisk get volumeserialnumber /format:list"
cmd.exe /c "wmic /node:localhost /namespace:'\\root\securitycenter2' path antivirusproduct get displayname /format:list"
One of the malware programs, in this case Vcurms, uses PowerShell command to dump the passwords kept in Windows, rather than in the third party tool. Obviously, it gathers data from browsers, too, but in a different manner – by accessing their data directly.
powershell.exe "[void][Windows.Security.Credentials.PasswordVault,Windows.Security.Credentials,ContentType=WindowsRuntime] $vault = New-Object Windows.Security.Credentials.PasswordVault $vault.RetrieveAll() | % { $_.RetrievePassword();$_ }"
I assume this command is related to Vcurms as STRRAT does not exhibit password stealing functionality.
Strengthening cybersecurity
This case shows vigilance and cooperation in cybersecurity. This phishing attack showed that even trusted platforms like GitHub can be used as a tool to spread malware. Cybersecurity experts offer the following tips to protect against such threats:
- Firstly, always verify the sender and avoid opening attachments or clicking on links in emails that seem suspicious or unexpected. If an email asks you to confirm payment details or personal information, it is better to contact the sender directly through another channel.
- Then, enable spam filters on your email to reduce the number of phishing and junk emails reaching your inbox.
- Make sure your antivirus software and all systems are updated to the latest versions. Regular updates help protect against known threats and vulnerabilities.
- Also, regularly monitor systems for suspicious activity and respond quickly to cybersecurity incidents. Use analytics and intelligent detection tools.
- And last, back up important data regularly and store it in a safe place. This will help you recover information in the event of a successful attack.