
Conti Ransomware
Why so rude?
The Conti group seems to have no conscience and compassion. Appeared back in 2020, they had hospitals and healthcare organizations as their beloved targets. This fact was complemented with very high ransom amounts - average ransom they used to ask is almost $850,000. Such a sum of money is pretty big for the companies that ransomware attacks, and it was paid pretty fast, since such critical infrastructure orgs cannot conduct their activity without the document flow they have on their computers. Though, healthcare sector was not their only target – Conti opted for governmental companies and govt contractors as well. Some say its administrations was associated with Russian special services, but no concrete evidence is available.
The majority of ransomware groups who apply the same distribution scheme - ransomware-as-a-service - take care to instruct all affiliates to avoid attacking “vital” facilities (in this case they are literally vital). That makes the “image” of these fraudsters slightly better, and helps the group to avoid the increased attention from FBI or other authorities. But not in the case of Conti ransomware.
Ransomware-as-a-service, or shortly RaaS, is a very popular spreading scheme. The developers of ransomware do not have to do a dirty job, which may lead to their capture - they delegate this work to third parties. Darknet is full of offers from various ransomware groups, where crooks offer you to buy the ransomware samples and get the right to distribute it. Of course, purchasing the ransomware is not a cheap action, but it may bring you a very large profit. However, spending it when you are imprisoned for committing cybercrimes is a quite hard task.
As with almost every ransomware group that aims at corporations, Conti ransomware used additional malware to steal the files and/or confidential information you have on the computers in your network or on your server. Then, criminals ask about the additional ransom payment - to prevent publishing the stolen information or reselling it to the third parties in the Darknet. Sometimes, especially when the stolen data is really interesting for someone, the ransom amount for data may be even bigger than the initial ransom.
| Note | readme.txt |
| C&C Servers | [923.82.128.116], [62.244.80.235], [85.93.88.165], [185.141.63.120], [82.118.21.1] |
| File Extension | CONTI, COSWH, UAKXC, RHMLM, UAKXC, AWSAK, TJODT, SYTCO, TJMBK, FBSYW, KCWTT, KLZUB, MBRNY, EXTEN, PVVXT, ANCIF, WENZW, GFYPK, ALNBR, HJAWF, FMOPQ, XMEYU |
| Algorithm | ChaCha20/8 |
| Features | Can perform the encryption, using up to 32 CPU threads |
| Damage | Deletes Volume Shadow Copies. Disables Microsoft Defender. Steals the data from the disk drives of infected machines. |
| Contact | [email protected] [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected] |
| Distribution | Email spam, phishing |
Encryption and further actions
Exactly after the injection, Conti ransomware manages to delete all Volume Shadow Copies that are present in the system. These copies are, exactly, the copies of your system disk drive with all files stored on it. This could be a pretty easy way to roll back malicious changes and recover the files - but not with the case of Conti. Meanwhile, the majority of other ransomware variants do the same - cybercriminals who develop them know perfectly about that feature.
The encryption mechanism used by Conti ransomware is ChaCha20. The encryption module is capable of using up to 32 threads of your processor, so the more powerful your system is - the faster the encryption happens. Deals a blow to the companies who purchase Threadripper CPUs for some purposes!
When the encryption is completed, the virus creates a readme.txt file on the infected desktop. Variants of the ransom note:
Your system is LOCKED. Write us on the emails: [email protected] [email protected] DO NOT TRY to decrypt files using other software.
The network is LOCKED. Do not try to use other software. For decryption KEY write HERE: [email protected] [email protected]
Your system is locked down. Do not try to decrypt, otherwise you will damage fails. For decryption tool write on the email: [email protected] [email protected] If you do not pay, we will publish all private data on hxxp://conti.news/
The system LOCKED. For decryption key write on: [email protected] Do not try to use other software.
The system is LOCKED. Do not use OTHER software. For DECRYPTOR write on the emails: [email protected] [email protected]
How is Conti ransomware spread?
Conti used pretty classic methods of malware distribution. Their bread and butter were malicious email messages and phishing. Why do you need to improve or change something that works so well? The efficiency of those methods is exceptionally high, and they’re cheap enough to keep the margin high. Moreover, it is quite hard to establish the protection from this way of penetration: while vulnerable RDP ports, that are used by Dharma virus, can easily be closed, you are not able to prevent the malicious email spam appearance.
The only way to make the chance of successful Conti infiltration lower is to show the employees who work with email messages how to distinguish the counterfeit with malicious contents from the legitimate message. Fake emails usually have a dubious email address - something like [email protected] or [email protected]. Sometimes, fraudsters try to counterfeit a legit email address of the sender they try to mimic. But they still cannot get the domain of the corporation, so messages from [email protected] are definitely untrustworthy. Other signs of counterfeit are the absurd contents - changes in security terms of the bank you don’t use for several years are irrelevant for you. Even if this email is real - there is no reason to open it.
Cybercriminals also used to hide the Conti ransomware inside of the attached file. Microsoft Office has a pretty big security breach, known as macros. This function sometimes helps to make the document more interactive, but also acts as a perfect carrier for viruses. Because of the poor protection mechanisms, virus can easily pass the “sandbox” environment of MS Office and start actions exactly in your system. Microsoft set the macros disabled by default, and even introduced a specific way to forbid any active content execution for files that come from the Internet. But it does not help - there are numerous other ways to circumnavigate the obstacle and make the thing run.
The End
Cybercrime gangs rarely last for a very long time. Being in business for almost 2 years, as Conti did, is already good luck. The vast majority of ransomware gangs last for about half a year, ending up at their members' detainment, or – what is more often – simply going offline without explaining any reason. Some finals are rather bright and noteworthy, like Babuk’s source code release on the forum or eternal hunt on REvil members, led by the FBI. Conti had a pretty dramatic image and the same dramatic final.
Being a RaaS group means hiring people from different parts of the world. Conti, however, preferred threat actors from Russia or russian-speaking countries. The start of the Russia-Ukrainian war in 2022 has created a rift in this group. Some of its members who were from Ukraine declared tearing all contacts with Conti, which traditionally supported any Russian political activities. Possible relations with the Russian External Reconnaissance Service we mentioned above may probably added even more to the conflict. Political motivation is unusual, though not the most interesting part of this story. Members who left the gang published source code of the ransomware, making it possible for everyone to use it, nailing any possible way to monetise the product for RaaS gang. That also resulted in the appearance of a new ransomware gang, NB65, who used the leaked code in attacks against Russian companies.
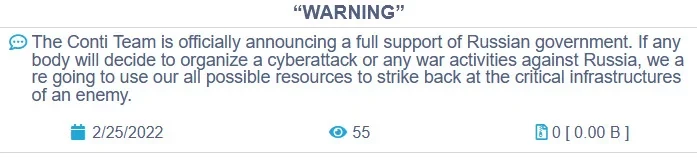
Despite the Conti’s administration attempts to pretend that nothing happened, they went offline in late June 2022. Crooks tried to imitate the activity, publishing older leaks and pretending them to be new breaches of the companies – but it was clear that something is wrong here. One summer night, their onion site went offline and was never back on.
However, this is only the end of the story of the brand. It is quite a common story for hackers to rebrand their brainchild after unpleasant occasions. Moreover, cybercrime gains and connections tempt, or sometimes force to continue working in that industry. Thus the saying may be true – once a cybercriminal, forever a cybercriminal. Some members reportedly moved to other groups. The aforementioned NB65 in fact may have consisted of Ukrainian ex-Conti members, who broke the rule to avoid attacking Russian companies. Some of the novice gangs, which appeared almost a year after the Conti ceased, use its code and some signature elements that may point at ex-members' activity.
More about Conti ransomware:
| 🔗 Angry Affiliate Leaks Conti Ransomware Gang Playbook |
| 🔗 Conti ransomware attacked the Health Service Executive (HSE) of Ireland |
| 🔗 Conti ransomware got its own website for stolen data |
