In the last couple of years, remote work has become integral to the world business landscape. However, to make remote work more efficient, employees need access to the company network wherever they are. A virtual private network (VPN) solves this by allowing remote employees to connect directly to the network, performing tasks as if they were in the office. VPNs use two basic types of security protocols, IPsec and SSL, and it’s essential to understand their differences to ensure security. Let’s compare IPSec and SSL encryption from a VPN end-user perspective.
The basics of VPN encryption
A VPN encrypts all your Internet traffic so it can only be decrypted using the correct key. Before leaving your device, the outgoing data is encrypted and sent to the VPN server, which decrypts the data using the appropriate key. From there, your information is sent to its destination, such as a website. This way, the encryption prevents anyone who can intercept the data between you and the VPN server from decrypting the content. This could be your ISP, a government agency, or hackers. In some cases, they may be synonymous with each other.
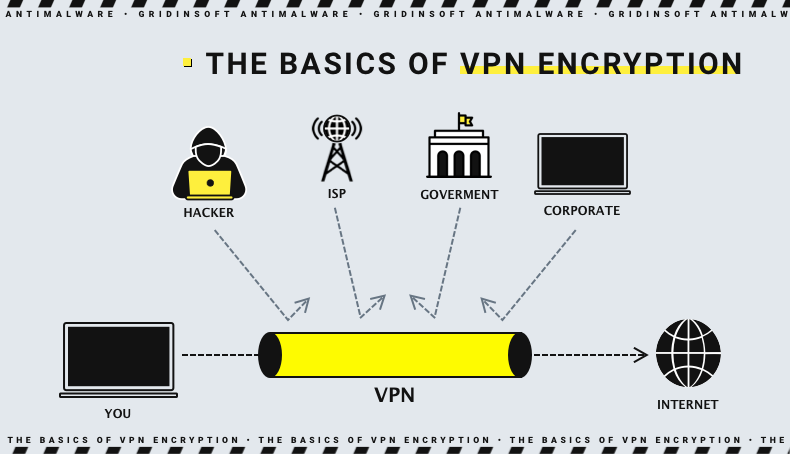
With incoming traffic, the same thing happens, only in reverse order. For example, when the data comes from a website, it goes to the VPN server first, gets encrypted, and arrives at your device. Your device decrypts the data, and you can browse the website as usual. All of this ensures that your Internet data remains private and does not fall into the hands of unauthorized parties. But, of course, if the VPN provider does not keep much data about its users and will not provide it by order of the police.
Encryption types may differ in the following ways:
- The persistence of encryption, or the method and degree to which your data is encrypted.
- How encryption keys are managed and exchanged
- What interfaces, protocols, and ports do they use
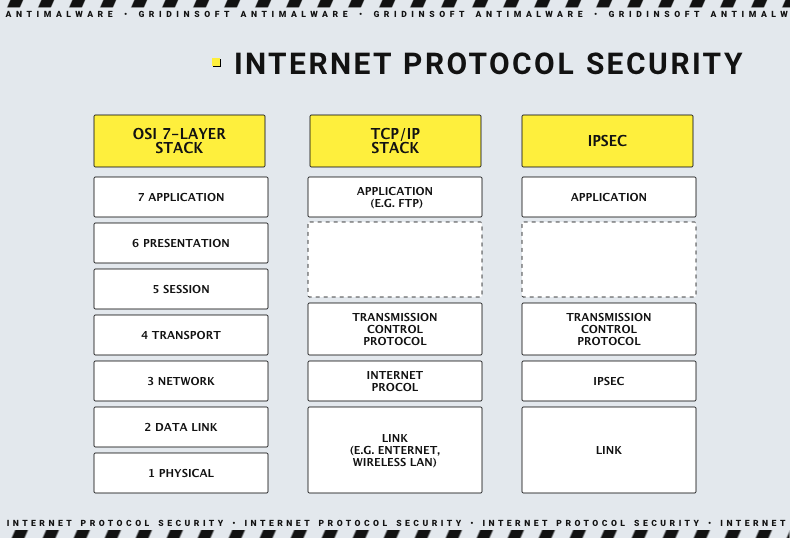
- What OSI (Open Systems Interconnection) layers do they operate on
- How easy is it to deploy
- Performance (read: speed)
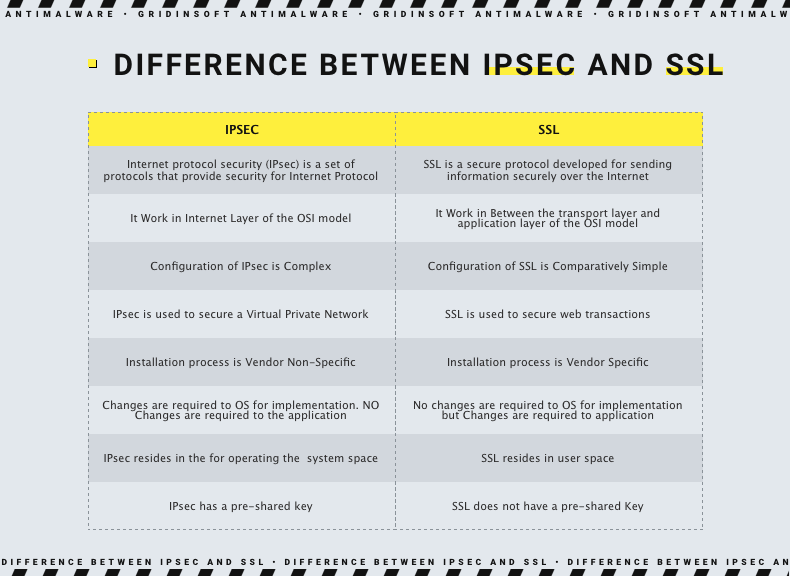
Difference between IPSec and SSL: Security
In a nutshell, a slight advantage in favor of SSL. IPSec connections require a shared key on both the client and the server to encrypt and send traffic to each other. However, sharing this key allows attackers to hack or capture the pre-shared key. SSL VPNs are devoid of this problem because they use public key cryptography to negotiate the handshake and exchange encryption keys securely. Unfortunately, TLS/SSL has a list of other vulnerabilities, such as Heartbleed.
Some SSL VPNs allow untrusted self-authenticating certificates and do not verify clients, which are especially common in SSL VPN browser extensions. Such virtual private networks allow anyone to connect from any computer and are vulnerable to man-in-the-middle attacks. However, this does not apply to most of OpenVPN’s clients. Likewise, SSL usually requires frequent patches to update the server and the client.
The lack of open source for IPSec-based VPN protocols may worry people who fear government spies and spyware. Thus 2013, Edward Snowden reported that the U.S. National Security Agency’s Bullrun program was actively trying to “insert vulnerabilities into commercial encryption systems, IT systems, networks and communication endpoints used by targets.” The NSA allegedly used IPSec to add backdoors and side channels that hackers could exploit – even the ones hired by the government. In the end, strong security is likely the result of experienced and careful network administrators, not protocol choices.
Firewall traversal
In short, SSL-based VPNs are better suited for bypassing firewalls. However, most Wi-Fi routers and other network equipment contain NAT firewalls. So they reject unrecognized Internet traffic and data packets without port numbers to protect against threats. IPSec encrypted packets (ESP packets) do not have default port numbers assigned to them. Therefore, NAT firewalls can intercept them, which can interfere with IPSec VPN workflow.
To avoid this, many IPSec VPNs encapsulate ESP packets into UDP packets. This assigns the data a UDP port number (usually UDP 4500). Although this solves the problem of NAT traversal, your network firewall may not allow packets through this port. Thus, network administrators at airports, hotels, and other locations may only allow traffic through certainly required protocols, and UDP 4500 may not be one of them.
SSL traffic can go through port 443, which most devices know as the port used for secure HTTPS traffic. Since almost all networks allow HTTPS traffic through port 443, it is likely to be open. In addition, although OpenVPN uses port 1194 by default for UDP traffic, it can be redirected through UDP or TCP ports, including TCP port 443. This makes SSL more helpful in bypassing firewalls and other forms of censorship that block port-based traffic.
Speed and reliability
Although both are reasonably fast, IKEv2/IPSec negotiates connections faster. Most IPSec-based VPN protocols take slightly longer to negotiate connections than SSL-based protocols. However, this does not apply to IKEv2/IPSec. IKEv2 is an IPSec-based VPN protocol that is more than a decade old. Nevertheless, it is still popular among VPN providers. Its crucial feature is quickly reconnecting whenever the VPN connection is interrupted. This makes it especially useful for mobile iOS and Android clients who don’t always have a reliable connection or frequently switch between Wi-Fi and mobile data.
As for the actual bandwidth, things are not clear here, as there are arguments on both sides. However, according to some claims, IKEv2/IPSec can offer higher throughput than OpenVPN, although both protocols typically use 128-bit or 256-bit AES encryption. The extra layer of UDP that many ISPs add to IPSec traffic to help it pass through firewalls adds to the load. This means that more resources may be required to process it. However, most people won’t notice the difference because, in most consumer VPNs, throughput is determined by server and network congestion, not the VPN protocol.
Ease of use
IPSec is more versatile, but most VPN provider applications users will not notice the difference. Because IKEv2, SSTP, and L2TP are built-in IPSec-based VPN protocols in most major operating systems, they do not necessarily require an additional application to run and work. However, most consumer VPN users will still use an ISP application to connect. In addition, although SSL works by default in most web browsers, you will need a standalone application to use OpenVPN. From an end-user perspective, IKEv2 offers a more user-friendly interface. This is because IKEv2 connects and handles interruptions faster. That said, OpenVPN is more versatile and may be better suited for users who can’t get what they need with IKEv2.
If we talk about corporate VPNs, they aim to provide access to the company network, not the Internet. The consensus is that SSL is better suited for remote access, and IPSec is preferred for VPNs between networks. Because IPSec operates at the network layer of the OSI model, it gives the user full access to the corporate network regardless of the application. Consequently, restricting access to specific resources can be more difficult. On the other hand, SSL VPNs allow businesses to control remote access to specific applications at a fine level.
Generally, network administrators who work with VPNs find that client management using SSL is much easier and less time-consuming than using IPSec.
Conclusion
If you have both options, we recommend using IKEv2/IPSec first, and if you have any problems, try OpenVPN. IKEv2 connection speed will be more comfortable for everyday VPN users while offering comparable security and speed. However, it may not work in some circumstances. Until recently, OpenVPN/SSL was considered the best VPN combination for most consumer VPN users. It is fast enough, secure, open-source, and can overcome NAT firewalls. It can also support UDP or TCP.
In turn, IKEv2/IPSec is a new competitor to OpenVPN. It improves L2TP and other IPSec-based protocols with faster connections, excellent stability, and built-in support for most new consumer devices. In any case, SSL and IPSec boast reliable levels of security with sufficient bandwidth, safety, and ease of use for most commercial VPN service customers.




