
Man in the Middle Attack
Man in the Middle attack is considered an obsolete threat. Most applications can successfully filter the attempts to sniff the traffic and hijack the keys. However, that does not mean you can freely join any network and do whatever without fear. Just as any other old-timers, it bears upon recklessness and low awareness.
What is a Man-in-the-Middle attack?
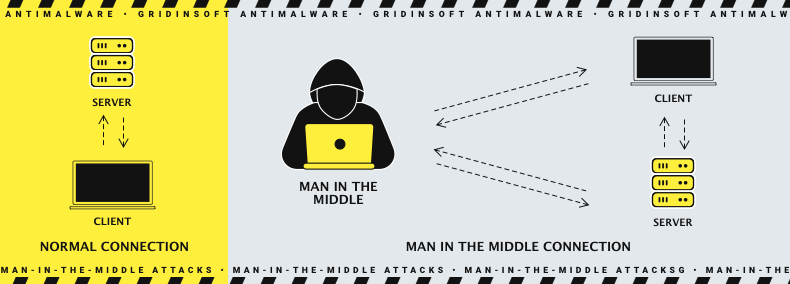
A Man-in-the-middle attack, or MITM, is a specific way of eavesdropping that supposes injecting the third party into the communication of two. In the computer world, such eavesdropping may occur when someone from the outside (primarily the threat actor) - can see the packets sent from the client to the server. The ways to realize this attack, as well as possible profits, may be very different - depending on what threat actors want.
How does the MITM attack work?
Let’s review the easiest man in the middle attack example. You dropped in the bistro which has unprotected Wi-Fi. That is very convenient - you don’t need to ask the waiter for a password and can relax by scrolling the feed while waiting for your lunch. But Mr.Doe, who sits in the other corner of that restaurant, doesn't think so. He can check all the internet packages passing through the router with special software. Seeing those packages is not enough if they are encrypted - but they are not: the network is not protected. Hence, all messages you send through this network could be read by Mr.Doe.
Such a basic method of MITM attack may easily be mirrored by package encryption on the stage of exchanging it with the server. You may see the “HTTPS” mark at the beginning of any website URL. That means that all packages you send to this site, as well as the ones it sends to you are encrypted with HTTPS protocol. It is impossible to read those packages without the special key available only to the client and server. However, as the proverb says, if you cannot deal with something - lead it.
Active eavesdropping
The more advanced example of the MITM attack is when the threat actor not just sniffs the packages in the network but also acts as an intermediary in the connection between the user and server. Such an approach requires more advanced software but gives way more profit from such an attack. Moreover, an attacker also needs to have full control over the network - the specific firmware for the router in perfect conditions. The basis for this attack may be the access point placed in a crowded place, which already has a Wi-Fi network. The attacker names his network similar to the naming of a legit one and waits for the connection. Unaware guests will connect, thinking this network is just another one offered by the establishment. They sometimes do so - to offload the routers and allow all guests to use the stable connection. That’s why such a disguise is pretty effective.
Full access to the network allows the crooks to see the packages sent. They get all the requests the client sends to the server, as well as the corresponding server responses. Hence, when the potential victim attempts to connect to the server (i.e., open a certain site) and receive the public key, crooks receive all these requests. Then, they send these requests to the server, pretending to be the original user. The server cannot divide the crook from the legit user, so it just sends the public key and the requested information. Then, the man in the middle could easily read the packages, as they were not encrypted.
Classification of the Man in the Middle Attacks
The methods and the effects of MITM attacks are known and can be predicted depending on the circumstances. Nonetheless, for the non-expert, it is important to see the details to understand what is a Man in the Middle attack. This attack has existed for over two decades, so analysts have witnessed and recorded different types. Exactly, that is the reason why its efficiency, as well as spreading, decreased so much. Nonetheless, there are still enough situations when MITM attacks may play a significant role.
By package interception method:
First, when analyzing the MITM attack case, analysts try to determine how crooks got the packages sent to or from the victims’ devices. There are three main ways crooks use to do that.
IP Spoofing
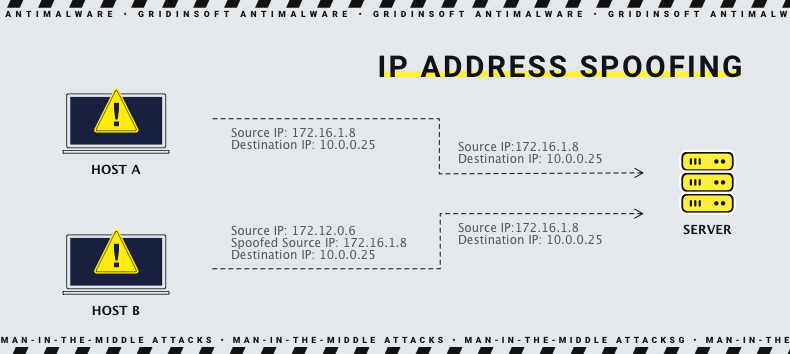
This method was partially mentioned in the paragraph above. The threat actor sits right between the server and the user and can see the packages sent from site to user and vice versa. However, it lacks the decryption key to read those packages. To make it possible and prevent any alarms, rascal spoofs the initial IP package where the client device receives the public key. Then, having this key, the attacker collects all the requests from the client, reads them, and then sends them to the server. Both victim and server will not likely expect that there is a third party.
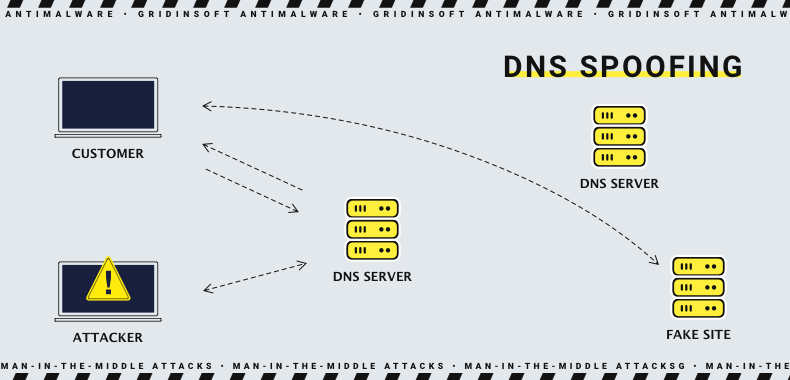
DNS Spoofing
A more sophisticated trick with a bigger chance of setting off the alarm. Connecting to any website requires finding this site in the Domain Name System (DNS). Controlling the router allows the rascals to apply a fake DNS to the chosen site, which will lead to the address chosen by the hackers. When the victim tries to connect to this site, it will be instantly redirected to the counterfeited page. Exactly, the one needed by crooks. That page is often a phishing website that repeats the design of a login page of a popular social network or online banking site.
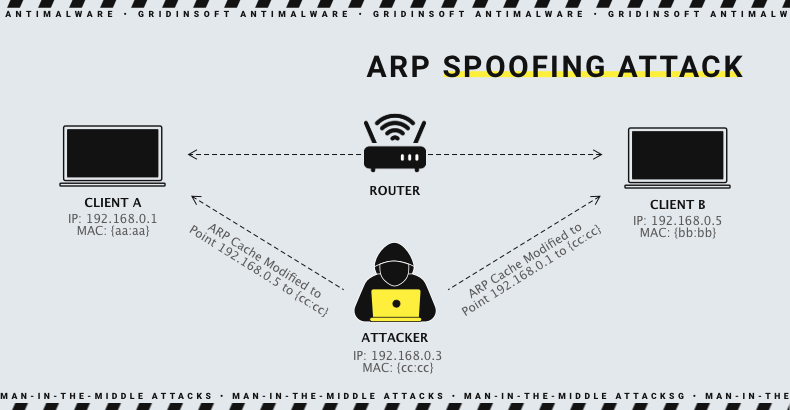
ARP Spoofing
That tactic is almost unused since it is effective only in the local area network. But it still may be effective - when the crooks act from inside the corporate network, using the computers, they manage to take over. Threat actors continuously send modified ARP messages into the network. In this manner, they make all computers in the network believe that this computer is the other one, or even a server. When the victim tries to connect to that address, it connects to the machine under the hacker’s control. And, as in the previous methods, it can read all the packages sent by the victim. To keep the visibility of a normal connection, crooks send the packages to the original endpoint.
By data decryption methods:
As mentioned, the intercepted packages are useless if ciphered. And most modern web browsers and networking applications have data protection features that make it impossible to read the packages even if they are sent through an unprotected network. Nonetheless, ones who commit Man-in-the-Middle attacks have some trumps up their sleeve.
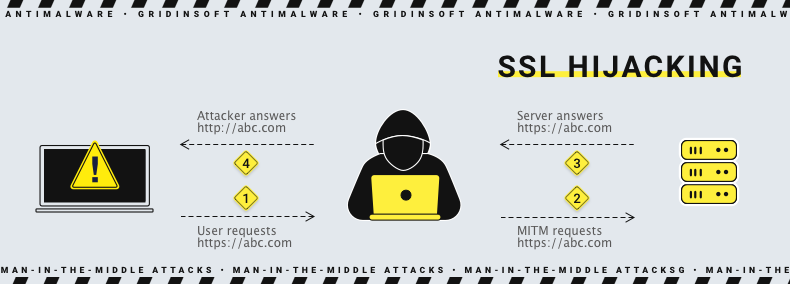
SSL Hijacking
SSL is an encryption protocol that provides a secure connection between client and server. To ensure that the connection is legitimate, each party receives a public key in the process of a TCP handshake. The rascal breaks in and give both sides the forged public key. Then, the server and client exchange the packages, thinking they have a secured connection. Meanwhile, the real connection is controlled by the man-in-the-middle.
SSL Stripping
This attack vector supposes the interception of TLS authentication at the initial connection stage. Then, the threat actor downgrades the connection from HTTPS (where “S” stands for “secure”) to HTTP. The latter supposes the data are transferring without any ciphering. Therefore, the man in the middle may easily read what the victim sends to the server - since there is no encryption. This method is risky since some web browsers can to re-check the connection type to ensure the use of the secure one (HTTPS).
SSL BEAST
Such an attack aims at TLS 1.0 vulnerability exploitation. That approach requires injecting the malicious JavaScript code into the victim's PC. With this thing, the threat actor can intercept the packages. The CBC (cipher block chaining) is getting spoofed in that way. Therefore the crooks can decrypt the cookies and auth tokens. They may easily log in from your accounts on the sites you visited through the infected network.
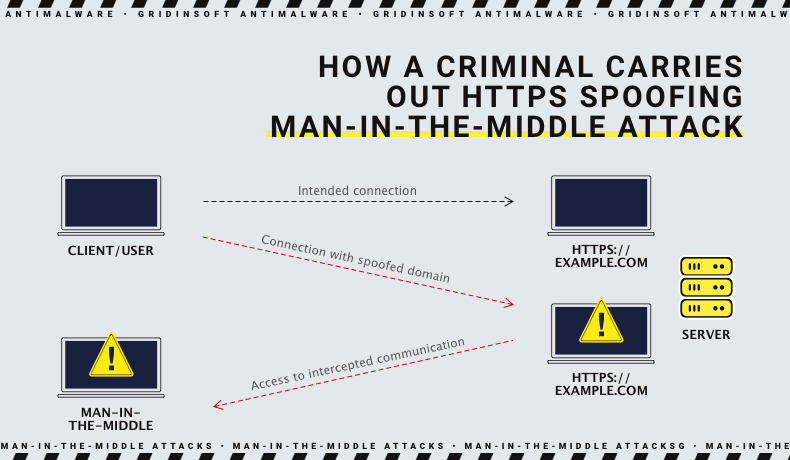
HTTPS Spoofing
That tactic supposes creating a fake certificate and sending it to the victim’s browser while the latter connects to the site that is originally considered safe. The victim exchanges packages with the server, thinking they are encrypted and secure - but they are not. Hence, the man in the middle can easily read all the packages.
Outdated variants:
There are also two ways of file decryption that are not so popular these days. That is generally caused by the complicated techniques and the exploitations of the technologies that are not in use nowadays.
Using the network sniffer. Sniffer is a program that copies all the packages sent from the designated device. Crook may install it into the router firmware and the victim’s machine. Since most modern websites use the HTTPS connection, those packages are encrypted with end-to-end encryption. Therefore, you still need to get the key somehow.
Impersonating the cellular tower requires even more effort. Special hardware equipment, in addition to the specific information from the telecom company about the frequencies and authorization, is expensive and hard to obtain for the ordinary person. And still, having the victim connected to your tower means only having to get its packages in a ciphered form (98% of cases). Sure, you can also eavesdrop on the phone calls and read the SMS - but is that worth it?
Counteracting the Man-in-the-Middle attack
Thanks to the cybersecurity advancements, most MITM vectors were blocked at the root and, what is more important - globally. The vast majority of the websites now use the HTTPS protocol, asymmetric encryption, and web browsers apply the double-check of the connection type. Browsers like Chrome or Edge will ask you twice before connecting you to the site through the HTTP connection. However, as you can see in the chapter above, they can still circumvent the encryption. So here are several tips for Man-in-the-Middle attack prevention.
- Avoid unprotected and unknown Wi-Fi connections. As you have likely read above, crooks can only read the packages if they can reach them. Sure, they can still create a protected access point - but how would they get enough victims in such a case? Or do they hang around asking everyone they meet to join their network?
- Don’t use public networks when working with critical information. In cases when you have no choice but to use unprotected networks, try to avoid the things that may expose you to any danger. Managing the bank account through online banking and working with confidential information about your job is risky. Watch out for the things you don't want to risk.
- Never ignore the security notifications. The browser and antimalware program you use will likely detect that something goes wrong. They will try to notify you about it - don’t ignore those messages! Most of the tactics crooks rely upon are based on spoofing the HTTPS connection, and this procedure will set off the alarm. Advanced antimalware software with internet protection features may also notify you about the fake websites and malicious redirects caused by the faked DNS address. Gridinsoft Anti-Malware is one you can trust in this question.
Frequently Asked Questions
However, We already mentioned the most basic advice. Hackers will never attack you via a network they don’t control. Thus, joining only the original network protected with a password (WPA3/PSK for the best effect) will keep your conversations far away from the risk of a man in the middle attack. That doesn’t mean you must be afraid of free Wi-Fi - check the SSID diligently, or ask the waiter to help you connect to the network.
