After the pandemic, work-from-home jobs became much more common around the world. Many predict that even after the pandemic subsides, remote work will remain prevalent in many sectors. On the one hand, working remotely from home is convenient. It has many benefits, but on the other hand, it also exposes individuals and businesses to various cybersecurity risks. That’s why it’s important to pay serious attention to work-from-home cybersecurity aspects. By following best practices, you can quickly mitigate much of the cybersecurity work-from-home threats.
7 Best Practices for Secure Remote Work Access
Secure remote access means using robust solutions and security strategies to create a network that can only be accessed by authorized personnel, no matter where they are located. This means that it must be impervious to unauthorized people. To provide the most secure remote access possible, organizations must work on two fronts – both at the employee and enterprise levels. There could be dozens of different approaches to providing the security, but we will mention only the most prominent ones.
1. Use the Zero-Trust Model
Zero Trust is a model developed by former Forrester analyst John Kinderwag in 2010. Since then, the Zero Trust model has become the most popular concept in cybersecurity. Recent massive data breaches only reinforce the need for companies to pay more attention to cybersecurity, and the Zero Trust model may be the right approach. Zero Trust refers to the complete absence of trust in anyone – even users within the perimeter. The model implies that every user or device must be checked up before access to a resource, both on and off the network. With a zero-trust model, management can be assured that no unauthorized person will gain access to sensitive data. It is essential to conduct checks periodically to determine if the strategy is working effectively.
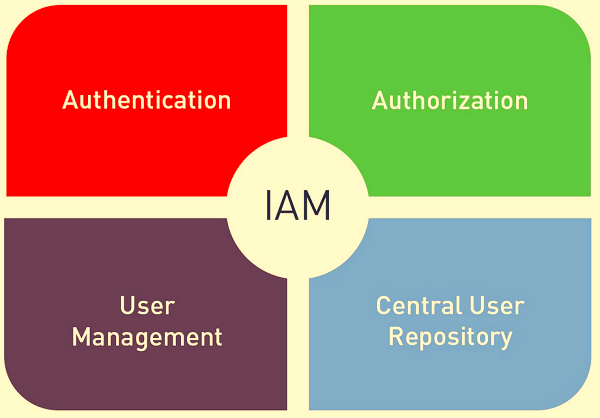
2. Apply identity and access management (IAM)
The IAM model limits access to information to employees as needed. Thus, if an employee does not need access to a particular piece of information, they are not allowed to access it. In the IAM, even the most trusted employees do not have access to information they do not need for work.
-
Users: Management will determine what information should be shared with each employee, and users are vetted before granting access to the network.
-
Devices: The company determines employees’ devices to access sensitive data. For example, management can make it so that only company-issued devices can access the organization’s sensitive data. If an employee attempts to access this data from an unauthorized device, they will not be able to do it.
-
Location: An organization can only provide access to sensitive data in specific areas. For example, you might make some sensitive information available only at company headquarters. This restriction protects data from being stolen or compromised by man-in-the-middle attacks.
-
Content: The IAM model not only restricts access to data but can also limit user access to specific Web sites, such as non-HTTPS sites or sites that may facilitate phishing activities, such as gambling or adult Web sites.
-
Network: The organization may require employees working remotely to use the company’s virtual private network (VPN) or other secure networks. However, an unsecured network can leave the organization vulnerable to an attacker-in-the-middle.
3. Protect all endpoints
When setting up secure remote access, it is crucial to ensure that you have protected the endpoints as much as possible. Often companies protect devices on their side but fail to do the same for their employees’ devices that connect to their network. Allowing employees to bring their unsecured or potentially infected devices onto your network can be a liability for the company. If their devices aren’t secure, the network isn’t safe. In the past, endpoint security was all about installing legacy antivirus software on endpoint devices. But now, with the rise of malware, upgrading your organization’s overall security is also necessary. Unfortunately, sometimes antivirus alone is not enough. We will now look at a few critical components of endpoint security:
Server Security
Since the server is connected to all remote employees and stores most of the data within the organization, firewalls and malware protection software should protect the server as much as possible. In addition, you should regularly update the server hardware to eliminate patched vulnerabilities. Finally, you should only grant access to the server to people who need it to do their jobs – as I have mentioned above.
Secure authentication
Secure authentication is the first line of protection against cyberattacks. However, despite having all the other protections in place, your network and systems can be vulnerable to cyberattacks if your authentication measures are unreliable. Here are some rules to help ensure stronger authentication for your networks:
- Passwords: use stronger and longer passwords with memorable characters, numbers, and capital letters.
- Passphrases: use passphrases instead of passwords. They are way easier to remember and use;
- Multifactor authentication: MFA for logging into your accounts is much more secure than passwords or passphrases.
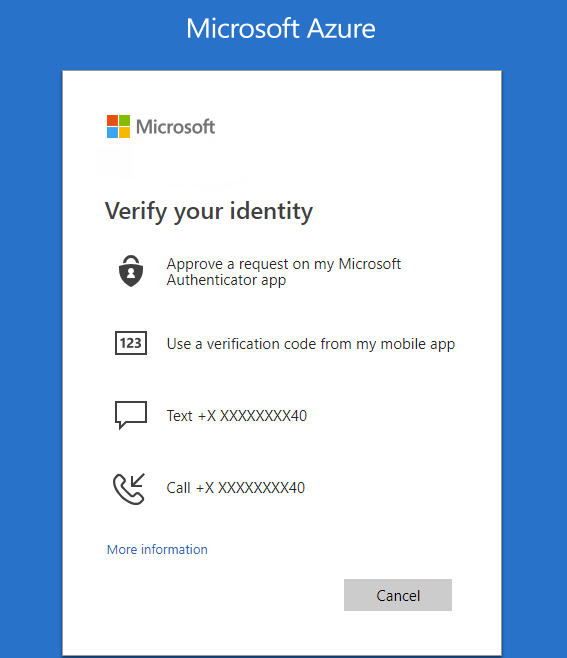
- No-Password Authentication: Passwordless authentication is a method of verification using two types of factors, the ownership factor, and the complicity factor. This method provides strong protection because it combines ownership (something you have) and inalienability (something you are).
Data Security
Company data should be protected in every status, both in motion and at rest. Using secure protocols such as TLS, HTTPS, FTPS, SFTP, etc., can help you protect your data on the go. In addition, data at rest can be protected with encrypted disks. And you should also forget about the physical security of the data because the data carrier can be lost, stolen, or physically damaged. Access to data in the cloud should be based on a zero-trust model, with access granted only after proper verification of all users and devices. When you choose third-party cloud providers, it’s essential to check their security features before contracting with them. Many cloud providers have additional security features, including penetration testing, perimeter firewalls, intrusion detection, and data encryption at rest. These security procedures protect your data from cyberattacks.
Threat Detection
Threat detection analyzes the entire security ecosystem to identify any malicious activity that could compromise the network. Several methods can help detect known and unknown threats. The most common are leveraging threat intelligence, analyzing user and attacker behavior analytics, setting intruder traps, and conducting threat hunts. If a threat is detected, you should take actions to properly neutralize it before it can exploit any existing vulnerabilities. Internal teams or external security experts should keep their eye on that 24/7.
Website security
Every organization’s website must have a valid TLS certificate to protect sensitive company and customer data. Also if you accept online payments or collect customer data, you are required by law to protect that data. Regulations such as GDPR, CCPA, HIPPA, and PCI DSS are designed to ensure citizen privacy. Suppose your organization experiences a data breach as a result of non-compliance. In that case, you will likely face massive fines, lawsuits, reputational damage, and other losses.
Device Security
All employee’s devices, including IoT devices, must have proper malware protection, firewalls, and endpoint security solutions. One way to make your devices more secure is to safelist the applications used on corporate devices and block the ability to install other applications. Also, limit specific remote desktop applications to admin users only. Cell phones are often used as a second authentication factor for MFA. If a cell phone is lost or stolen, care should be taken to secure accounts before criminals hack into them. Ensure your employees are using their mobile phones safely and securely.
Risk Assessment
Even with all of these steps in place, your organization’s ongoing cybersecurity risk assessment is critical. This process involves regular audits of network activity, software, and hardware to alert the organization to emerging issues and potential threats.
4. Raise cybersecurity awareness among employees
The weakest unit in any security system is the human element. Training your employees to think consciously about their online activities can prevent many unpleasant things from happening. It is critical to provide regular training and ensure employees follow company policies. Security training for employees should cover:
- A guide to good password practices
- Privacy and data confidentiality policies
- Which devices to use and how to keep them secure
- Guidelines for secure device and software upgrades
- Using multi-factor authentication for accounts and devices
- How to detect social engineering and phishing attempts, fraudulent websites, and other threats
- What to do if an incident occurs
5. Protect Data in Transit
Data in motion means when it moves from one location to another. This includes internal data transfers between endpoints and data transferred to and from a remote server. Under that process data can be vulnerable to man-in-the-middle attacks, so creating a secure channel for transmitting this data is imperative. An effective way to protect this data on the move is to use SSL/TLS certificates. It is also essential that the TLS certificate is valid. An expired or invalid certificate or the one with a compromised key does not provide sufficient security. Therefore, renew all certificates before they expire and update them as needed.
Another method to prevent cybercriminals from accessing your network is to use a VPN. This service allows employees who work remotely to connect securely to your network. Before the COVID pandemic, 22% of employees worked remotely, according to statistics. After the pandemic began, that number rose to 58%. Network security for remote access is much more than protecting data on the go and includes the following:
Configuring hardware controls
Hardware controls include protecting routers, cables, devices, and other equipment used in an organization, whether in offices or remote locations. It includes protection for all material equipment used in the organization, whether in offices or distant locations. Equipment should only be purchased and maintained from authorized vendors.
Implementing software management tools
Software management tools include purchasing, implementing, upgrading, and dropping software according to the organization’s security needs. It should be constantly updated to avoid security threats, as outdated software is full of vulnerabilities that cybercriminals like to exploit. If employees use their own devices (i.e., bringing their device or BYOD environment), only trusted programs and websites should be allowed on the device. Sometimes insecure apps and websites can infect the device and, in turn, the corporate network.
Implement administrative controls
Remote employees should be prohibited from using open networks like cafes, hotels, restaurants, or libraries. Open networks cannot control who logs in and can leave your company vulnerable. In addition, attackers can access your network on an open network through a remote employee’s device. For that situation, the company should provide access to a VPN for more secure network requirements.
In addition, you must effectively train employees to understand the need for security procedures. They should apply the standards set by the organization in their daily lives. The organization should have clearly defined passwords, devices, network requirements, and software and hardware rules.
6. Secure the Remote Desktop Protocol
RDP is one of the primary protocols for remote desktop sessions, where employees access their office computers from another device. Many companies rely on RDP to allow their employees to work from home. To reduce the risks, change the default port (3389) to any other port, use a firewall to limit access to listening ports, and use MFA for authorization. It is also recommended to use NLA to protect remote desktop access.
The importance of RDP securing is the sad statistic of the last few years, when a huge share of cyberattacks on corporations were done through the RDP breaches. After getting into the one PC that had a poorly-secured remote access, hackers are starting to brute force all other computers in the network and the domain controllers. If the computer they have managed to get in has administrator privileges, it is very easy for hackers to infect the whole network in just an hour.
7. Physical Security While Working Remotely
Never leave your devices or laptop in your car
Employees are strongly recommended never to leave their work computers or devices in the vehicle. It is always advisable to keep work laptops and devices with you when you travel. And the trunk of your car is no safer.
Don’t use random flash drives
The classic hacking method is to drop some high-capacity flash drives near the company you hope to attack. Unfortunately, the chance that an unsuspecting employee will take the flash drive and use it is surprisingly high. So avoid using a flash drive unless you know where it came from. Likewise, don’t keep using it if you’ve plugged it into a system you can’t honestly vouch for the security of.
Use a USB Data Blocker when charging at a public phone charging station
Sometimes we need to charge our phone and the only option is an unknown USB port. In that case, an intelligent measure would be to use a USB data blocker to prevent data sharing and protect yourself from malware. This type of USB protection allows the device to connect to a power source without connecting the data pins inside your device; it connects the power wires, not the data wires.

