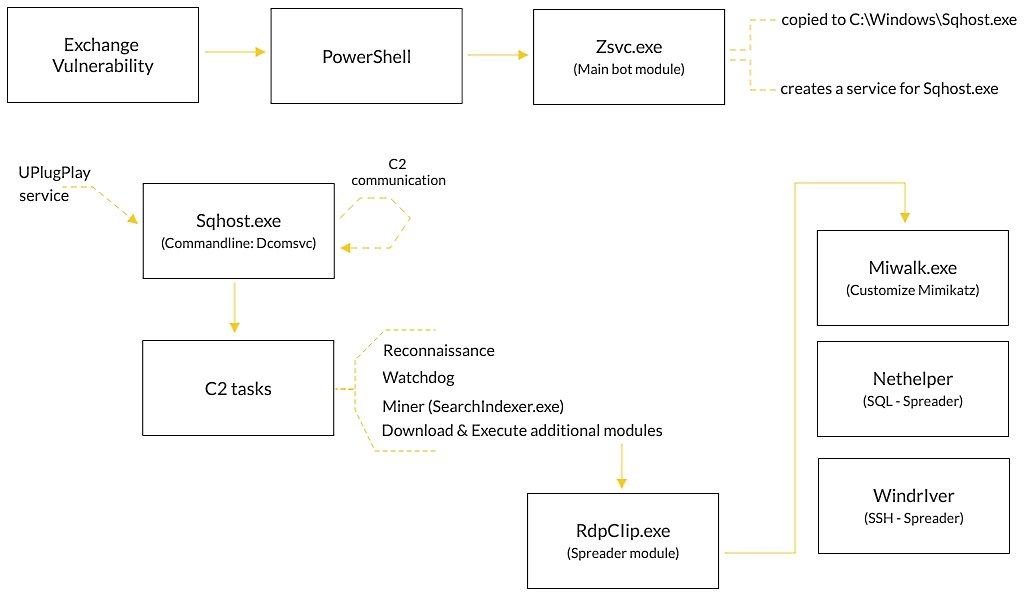
Since the patches for ProxyLogon problems were still not installed, cybercriminals continue their activity, for example, the updated Prometei botnet attacks vulnerable Microsoft Exchange servers.
Researchers from Cybereason Nocturnus discovered Prometei malware, which mines Monero cryptocurrency on vulnerable machines.
In early March 2021, Microsoft engineers released unscheduled patches for four vulnerabilities in the Exchange mail server, which the researchers collectively named ProxyLogon (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065).
These vulnerabilities can be chained together and exploited to allow an attacker to authenticate on the Exchange server, gain administrator rights, install malware and steal data.
In early March 2021, attacks on vulnerable servers were carried out by more than 10 hack groups, deploying web shells, miners and ransomware on the servers.
According to statistics released by Microsoft last month, approximately 92% of all Internet-connected Exchange servers have already received patches.
This modular malware was first detected last year. It is capable of infecting Windows and Linux systems, and has previously used the EternalBlue exploit to spread across compromised networks and compromise vulnerable machines.
Cybereason Nocturnus experts write that Prometei is active at least since 2016 (judging by the samples uploaded to VirusTotal). The botnet was recently updated and “learned” how to exploit ProxyLogon vulnerabilities.
Thus, now Prometei attacks Exchange servers, and then installs payloads for mining on them, and also tries to spread further along the infected network using the EternalBlue and BlueKeep exploits, detected credentials and modules for SSH or SQL.
The updated malware has backdoor capabilities with support for an extensive set of commands, including downloading and executing files, searching for files on infected systems, and executing programs or commands on behalf of the attackers.
Let me remind you that I also talked about the fact that FBI removed web shells from vulnerable Microsoft Exchange servers without informing owners.