Forescout and Medigate Labs issued a report on NUCLEUS:13 problems – A Set of 13 vulnerabilities which affect Siemens Software Library that is widely used in medical devices, automotive and industrial systems.
NUCLEAUS:13 affects Nucleus NET, the TCP/IP stack that is part of Siemens’ RTOS Nucleus. Typically, Nucleus runs on SoCs in medical devices, cars, smartphones, IoT devices, industrial equipment, aerospace, and so on.
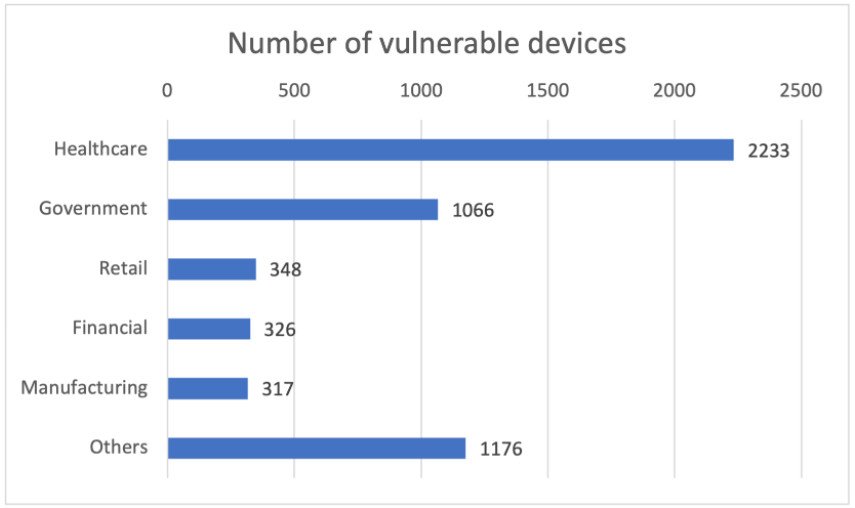
According to experts, more than 5,000 devices are still using the vulnerable version of Nucleus RTOS, and most of these devices are in the healthcare industry. The problems discovered by researchers can be used to capture and disable such devices, as well as to “drain” information.
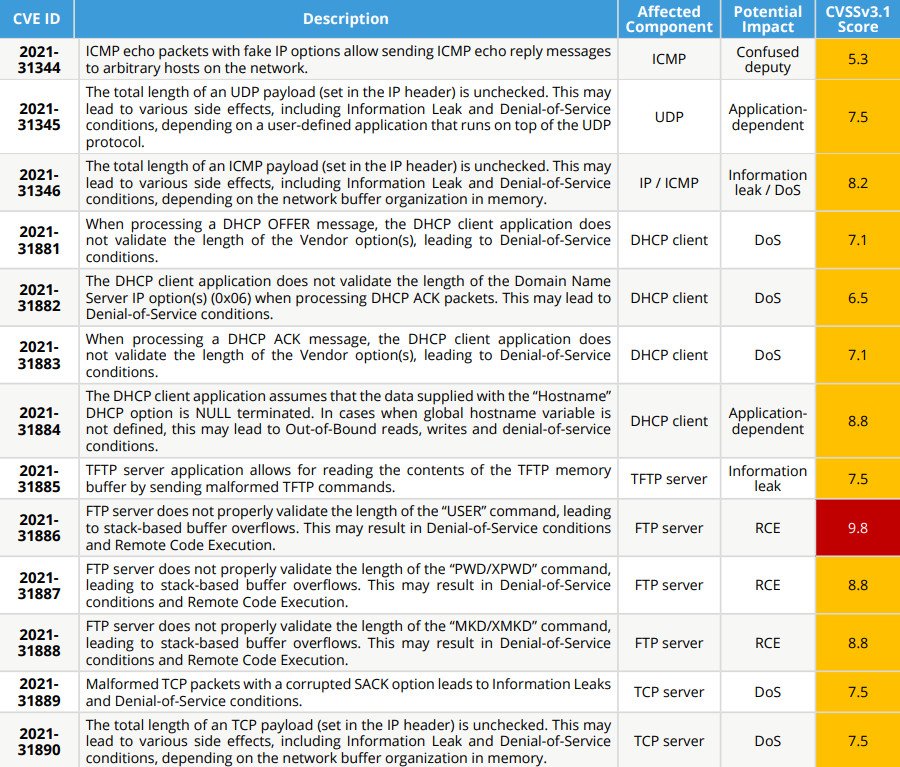
The most dangerous vulnerability from the NUCLEUS: 13 “suite” is named CVE-2021-31886, which scored 9.8 out of 10 on the CVSS vulnerability rating scale and allows remote arbitrary code execution (RCE). Other bugs are rated as medium to high severity issues.
The researchers also released a proof-of-concept video demonstrating how NUCLEUS:13 vulnerabilities can be used in practice. The video shows that the attacker only needs to have a network connection to the vulnerable device, since the attack takes only a few seconds to complete.
Forescout says it has partnered with Siemens engineers and the ICS-CERT team to notify developers and manufacturers of issues and fix them prior to publishing the report to the public.
ICS-CERT has already published its own security advisories to draw organizations’ attention to NUCLEUS:13 vulnerabilities.
In particular CISA recommends users take defensive measures to minimize the risk of exploitation of this vulnerability. Specifically, users should:
- Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.
- Locate control system networks and remote devices behind firewalls, and isolate them from the business network.
- When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize VPN is only as secure as its connected devices.
Siemens has also released security updates to all of its customers.
Let me remind you that I also talked about the fact that The PwnedPiper problem poses a threat to 80% of US hospitals.