A new cybercrime tool called “AuKill” has emerged, which attackers use to disable endpoint detection and response (EDR) defenses used by enterprises before deploying ransomware.
AuKill malware uses malicious device drivers to infiltrate systems. Recently, researchers from Sophos discovered an attacker using AuKill before deploying Medusa Locker ransomware and another attacker using it on an already compromised system before installing the LockBit ransomware. The trend is a response to the growing effectiveness of EDR tools, which provide security vendors with a significant advantage in spotting attacks. Threat actors are targeting the tools, causing them the most trouble.
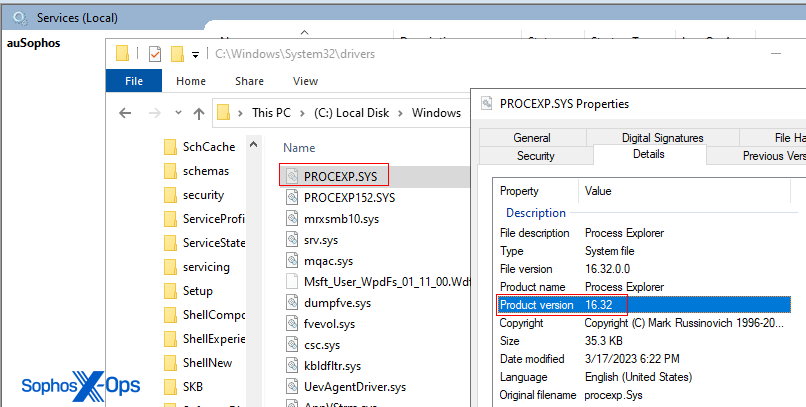
AuKill drops a driver named PROCEXP.SYS from release version 16.32 of Process Explorer into the exact location as the legitimate version of the Process Explorer driver (PROCEXP152.sys). Once on a system, the tool abuses the legitimate driver to execute instructions to shut down EDR and other security controls on the compromised computer. Sophos has analyzed six different versions of AuKill and noticed some substantial changes with each new version. Newer versions now target more EDR processes and services for termination.
These attacks are similar to a series of incidents reported by Sophos, Microsoft, Mandiant, and SentinelOne in December. In those attacks, threat actors used custom-built drivers to disable security products on already compromised systems, leaving them open to other exploits. Like other drivers, the vulnerable Process Explorer driver that AuKill leverages has privileged access to installed systems and can interact with and terminate running processes.





