According to ransomware attacks status statistics, the trend of incidents related to this type of malware will decline in 2023. But is this really the proper conclusion, or is it not all clear-cut? Today we will look at analysts’ opinions and determine why ransomware activity is decreasing.
Some statistics
According to the X-Force Threat Intelligence Index 2023, ransomware’s share of incidents decreased by 4% between 2021 and 2022. While ransomware accounted for 21% of all incidents in 2021, it dropped to 17% in 2022. However, for some groups, 2022 was not the most successful year. For example, the Russian group Trickbot was forced to terminate Conti ransomware operations and decommission two known malware families. This resulted from joint sanctions imposed by the United Kingdom and the United States against group members. LockBit, on the other hand, took the lead in the market and covered all 17% of incidents for 2022.
What caused the decrease in the number of incidents?
On the one hand, the decrease in incidents may be due to reduced incident reporting. For example, the FBI claims that only about 20% of victims report an incident. That is, some affected organizations do not report the incident. On the other hand, experts attribute this to the recent problems faced by threat groups. In addition, experts say that this is a temporary phenomenon and do not rule out that the criminals are regrouping and starting new operations. Also, lately, some attackers have begun cooperating with other “colleagues in the industry,” which only strengthens their results.
Efficiency of protective measures
Another important reason ransomware attacks are becoming less effective is to pump up and improve EDR solutions. EDR solutions are practical and significantly reduce the negative effect of ransomware attacks. However, there are still many effective means against cyber attacks, including firewalls and UBA/SIEM/SOAR technologies. These technologies detect and analyze abnormal behavior of users and entities in an information system. In addition, they collect, aggregate and analyze data on security events, allowing you to identify potential cyberattacks and take appropriate security measures. Experts emphasize that the more organizations invest in protection, the less effective ransomware attacks will be, which is obvious.
War in Ukraine
The war in Ukraine has created significant problems for the ransomware industry. Since most of the gangs are based in Russia, the latter’s full-scale invasion of Ukraine has disrupted the business model of ransomware attackers. Some gangs – even major ones, like Conti – had members all over Eastern Europe, thus the war outbreak inevitably influenced their operations. In addition, U.S. sanctions against cryptocurrency exchanges, which Russian criminals use to launder ransoms, disrupted the activities of these bad actors. Therefore, the decrease in ransomware activity is closely related to Russia’s situation on the world stage.
Disruption of Darknet marketplaces
There have been significant recent successes in the fight against cybercrime. Intelligence agencies have shut down two major darknet sites that had served as essential trafficking points for criminals. We are talking about Breached Forums and Genesis Market, which significantly impacted cybercriminal activity. Purchasing malware, accesses, and merchandising stolen data is now way harder than it used to be. Not surprisingly, the closure of these sites created problems for cybercriminals.
Fewer organizations willing to pay ransoms
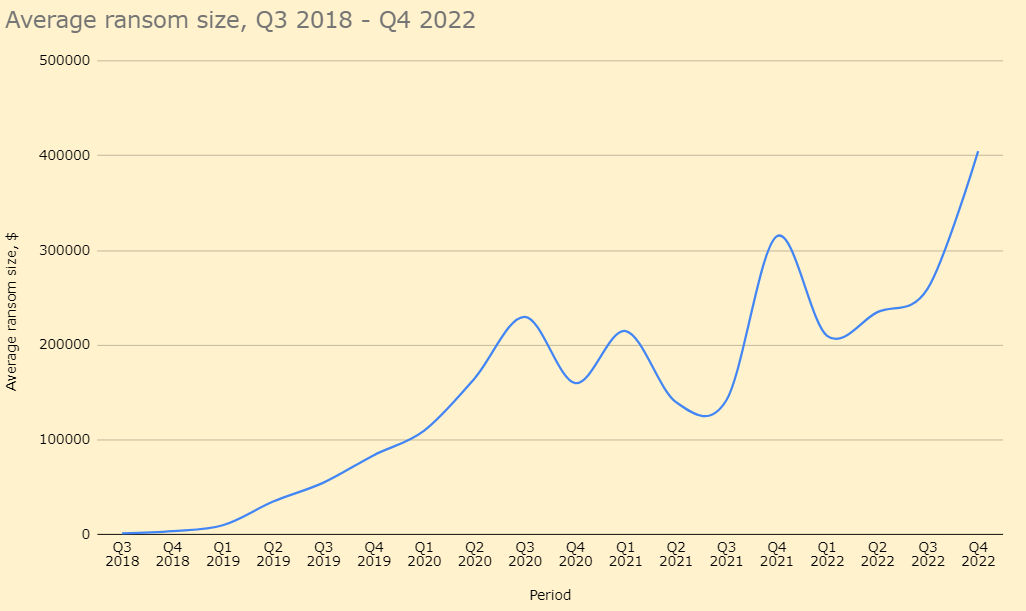
According to statistics, the number of victims willing to pay ransom in 2022 has also dropped by 14% compared to the previous year. While in 2021, the percentage to pay criminals to decrypt files was 82%, in 2022, the number was 68%. This could also have been influenced by an increase in the average payment of almost 71% compared to the previous year. If we talk about the reasons pushing victims to make this decision, there are several:
- Paying a ransom does not guarantee data return but doubles the recovery cost. In addition, statistics show that 1 in 4 victims do not receive encryption keys.
- More and more organizations are using practical data backup tools.
- Paying a ransom indicates a successful attack and encourages criminals to go even further.
Information Sharing in Incident Response
Effective threat prevention strategies require robust defense mechanisms, including information sharing. While there have been improvements, there is still much room for progress. As one expert noted, “Information is power and, in cybersecurity, it’s the power to prevent similar events from happening.” Cybercriminals target sectors that cannot be idle by ransomware. It may be in mining and industrial sectors, where operational interruptions can result in millions of dollars in losses. ISACs have a critical role to play in helping industries combat ransomware attacks.
Analytical note
Experts find it hard to say whether the incidents have decreased. Still, the number of ransoms being paid has gone down. This may be due to organizations improving their backup protection and the risk of paying due to OFAC (Office of Foreign Access Control) sanctions. This trend may continue in 2023. Analytics is hopeful about the decline but also concerned that groups may adopt more extreme tactics to increase their conversion rates. Specifically, groups may use stolen data to target customers and business partners. The current trend is to target businesses and sectors that cannot afford to be affected, have significant tech debt, and are likely to pay to alleviate the damage. However, this does not only apply to Fortune 500 companies. Small and medium enterprises are also vulnerable to these attacks.
Recommendations to prevent ransomware attacks
To avoid ransomware attacks, organizations should implement various measures. For example, application control, disabling macros from email attachments, and adopting a zero-trust posture. In addition, experts suggest taking a proactive approach to cybersecurity, especially in areas vulnerable to such attacks as identity and access controls. It can be achieved by using methods like password vaulting and multi-factor authentication. Implementing frequent data backups, establishing an incident response plan, and investing in cyber insurance are essential. Threat intelligence platforms can also help track ransomware gangs and their tactics to prevent attacks. Organizations can prevent ransomware actors from launching a debilitating encryption attack by catching the initial intrusion or malicious activity. In addition, I have a couple of solutions that can significantly reduce the problem of ransomware:
- Make it absolutely illegal to pay the ransom. As long as some companies/organizations keep paying, it would never stop. However, financing crime needs to be absolutely illegal anyway. Not to mention, why ransomware gangs would still continue doing attacks in countries which absolutely ban ALL ransomware payments? Wouldn’t that be just a lot of cost/effort/risk w/o making any money for them?
- Make it mandatory for all companies/organizations do periodical (automated) full data backups. They all need to have a plan ready to reinstall all their software & reload most recent backup data. Aside from the ransomware, regular automated full data backups help safeguard against various risks such as hardware failures, natural disasters, and human errors. By periodically backing up data, organizations can capture and store a snapshot of their critical information, ensuring they have a recent copy available for recovery if data loss or system failure occurs.