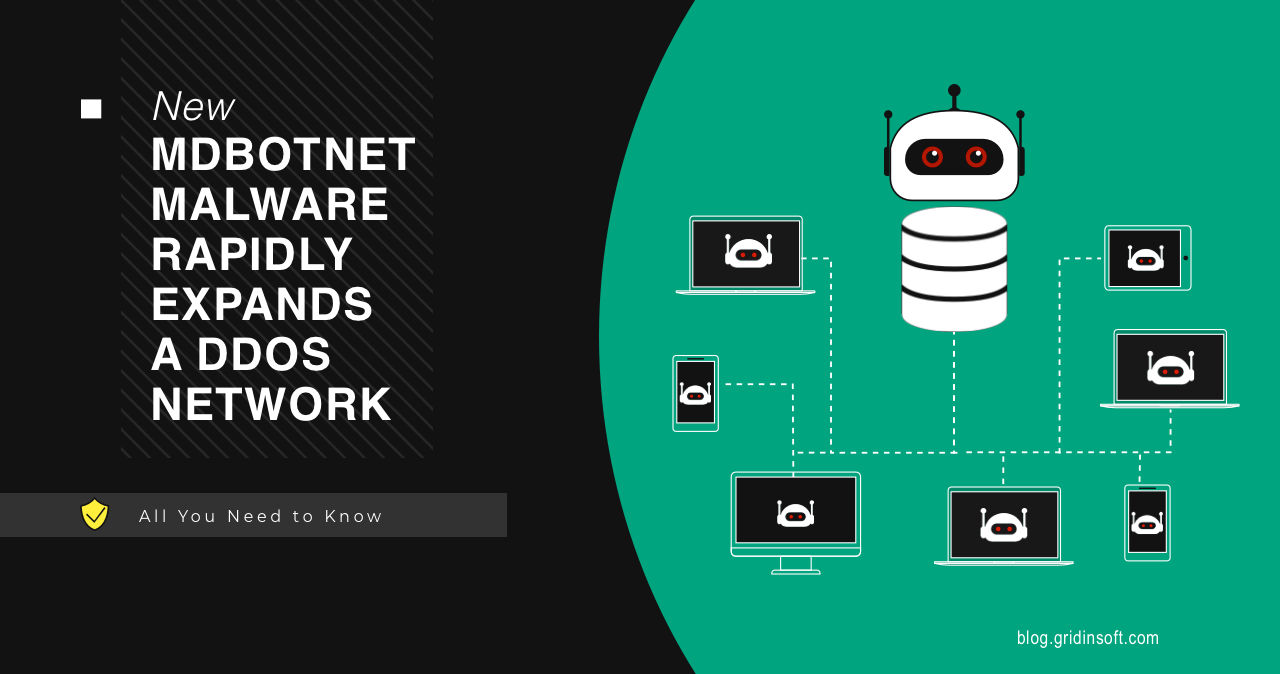
MDBotnet is a new malware strain that appears to be a backbone of a botnet, used in DDoS-as-a-Service attacks. Being a backdoor biassed towards networking commands, it appears to be another sample of russian malware. Analysts already report about the IPs related to this botnet being used in DDoS attacks. Let’s see why it is so special and how you can avoid having troubles with MDBotnet.
MDBotnet Malware Description
Darknet posts that offer DDoS attacks services are not something ridiculous. MDBotnet developers published a copy-paste post that promotes their services for just 2,500 rubles (~$31). They promise the ability to attack any kind of web resource, and even offer testing their capacities in short attacks. The DDoS-as-a-Service model is still pretty new, so hackers likely attract clients by offering pretty low pricings, support and refunds. Strange detail here, however, is that right below the statement about the price they say that prices for all resources are individual.
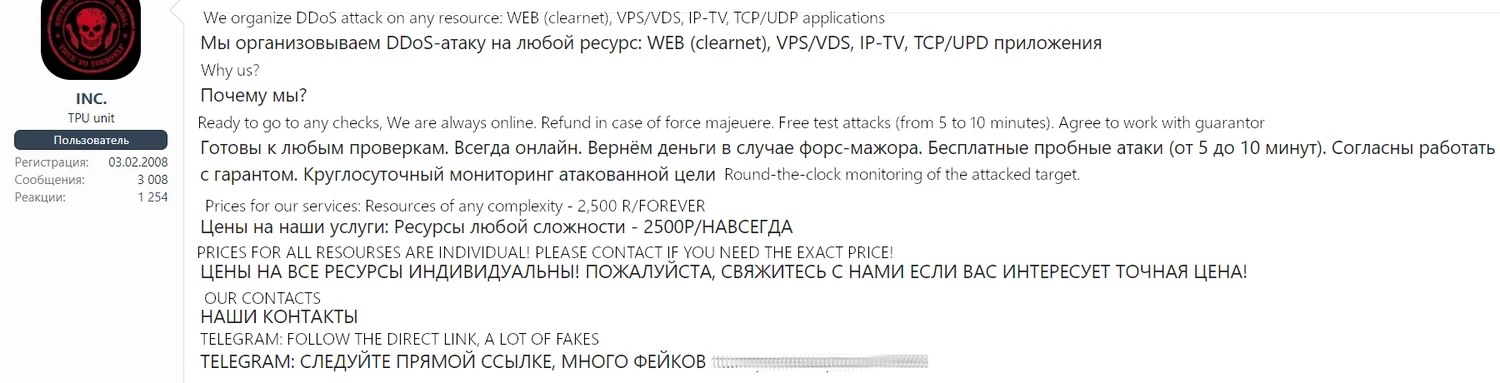
All negotiations happen in the Telegram channel, which becomes a new trend. Moreover, hackers are not selling the malware itself – just the ability to use its botnet. This can make the reaction to the changes of this threat slightly harder. Fortunately, the samples of MDBotnet malware are widely available despite such a conspiracy.
MDBotnet analysis
The currently circulating samples of MDBotnet do not appear to be protected in any way. Neither encryption, nor encoding is applied; malware does not use any kind of obfuscation or PE section bloating. That, however, may be the outcome of the attempt to deliver the samples with dropper malware; on an already infected system, there’s no need to boggle the antivirus program. However, it could possibly be just an ignorance towards protective measures. Other malware families typically offer a suitable workaround for payload encryption, but I could not find any recommended or used with MDBotnet.
The payload assembly contains 2 sections and 3 modules; the Config section appears immediately after the initial C2 connection, where malware receives the configuration file. Modules, however, mostly say for themselves, as they are responsible for the key program functionality – DDoS attacks done with different methods. Malware is capable of performing SYN Flood attack and HTTP GET attack. It also carries an updater module, that periodically connects to the C2 and requests possible updates. This is an uncommon approach, as most malware typically have the updates initiation from the command server side.
DDoS attack capabilities
I’ve mentioned SYN Flood and HTTP GET attacks as ones MDBotnet can perform. The latter, however, is not very exciting, as there is nothing sophisticated or extraordinarily efficient about this attack. In this mode, malware simply sends an HTTP GET request to the target server, hoping to jam it. Though a botnet large enough can promptly jam even pretty big sites.
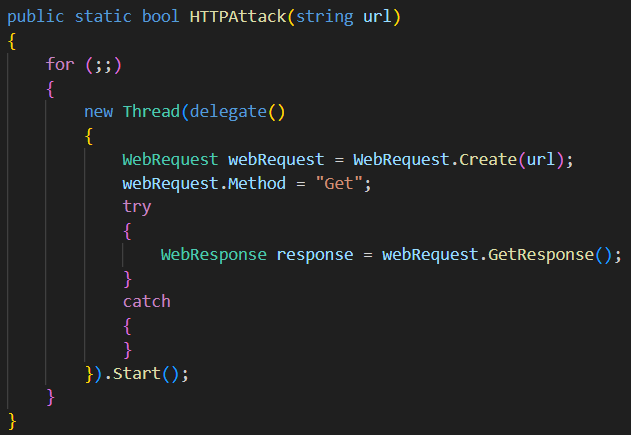
SYN attack, however, has some interesting details. Instead of sending the packets to the target server, malware in this mode will repeatedly request to establish the TCP connection with the target. In this attack course, during the TCP handshake, the target server will respond with the SYN-ACK packet, but never receive the ACK packet back from the attacker. That makes the connection establishment procedure stuck; by sending numerous connection requests, it is possible to seriously disrupt the server workflow.
The interesting detail about the MDBotnet configuration is the fact that SYN module addition may be disabled at the compilation. It may be the sign that this malware may receive more functions in future, and modules that allow other attack vectors will be delivered by a command from the C2 server.
Protection Against MDBotnet
The answer to the “how to protect” question here depends on the type of a threat you are trying to protect yourself from. Avoiding being a part of the botnet requires a different treatment than preventing DDoS attacks. Let’s review them one by one.
Avoid malware sources as hard as possible. These days, those are most often software cracks and email spam. While the former is pretty easy to reject, email spam may be tricky, as hackers sometimes do their best to make the email look more convincing. Though, they cannot repeat all the details at once – be attentive to email addresses and naming conventions.
Use anti-malware software. Having a proper protective tool will make it much easier to avoid the infection. Even if the threat is already running, an anti-malware software will make your system clean in just a few clicks. However, to make sure that even most evasive threats will not get away, you should use advanced solutions, like GridinSoft Anti-Malware. It is effective even against most novice threats that feature packing and encryption.
For corporate protection, there is a separate class of solutions. It is quite attractive for botnet masters to add an entire corporate network to their possession. To prevent this from happening, consider choosing an appropriate EDR/XDR solution, depending on the size and extensiveness of your network. Auxiliary solutions that will ease data collection and response orchestration will be a pleasant addition.
Apply network monitoring tools. This advice works both against an active threat within your network and attacks from outside. Even a simple firewall, when set up properly, can excise malignant traffic – regardless of where it comes from. Fortunately, IP addresses of large botnets that are currently active are commonly available in dedicated places. NDR solutions, on the other hand, will not only filter out the traffic, but also help with preventing further issues.