DDoS Attacks: 6 Tried-and-Tested Methods How to Prevent It
Before considering how to prevent DDoS attacks, we first consider this definition. Because without understanding what is at stake, it will be hard for us to take action. The DDoS attack is a cyberattack “denial of service” that aims to harm the user and make the target system, network, service, or server inaccessible through a massive amount of fake traffic.
In practice, this happens in the following way: attackers generate many requests or packages, the purpose of which is to overburden the target system. This way, services become unavailable, and the company suffers extended system downtime. As a result, the attacker must use many controlled or hacked sources.
DDoS Attack Meaning, Сommon Motives
Some hackers use this cyberattack to work like extortion software. For example, blackmailing a business, asking for a ransom, and the like. But the most common motives for DDoS attack are:
- Communication or service disruption
- Damage the brand
- Gain a business advantage while competitors’ website is malfunctioning
- Divert the Cyber Security Group’s attention for another purpose
Types of DDoS Attacks
Attackers use different strategies to achieve a positive outcome in the end. So because of its various methods, all DDos attacks are divided into three main types:
- Application-layer attacks
- Protocol attacks
- Volumetric attacks
Application-Layer Attacks
This attack’s purpose is to disrupt a particular application’s operation rather than the entire network. During the attack, the attacker generates many HTTP requests that exhaust the ability of the target server to respond. According to the statistics from cybersecurity specialists, the typical targets of such attacks are web applications, cloud services, and user apps. Preventing an attack of this level is quite tricky because it is not so easy to distinguish legitimate HTTP requests from malicious ones. Also, the peculiarity of this type is that a hacker can make an attack using only one device at the level of applications.
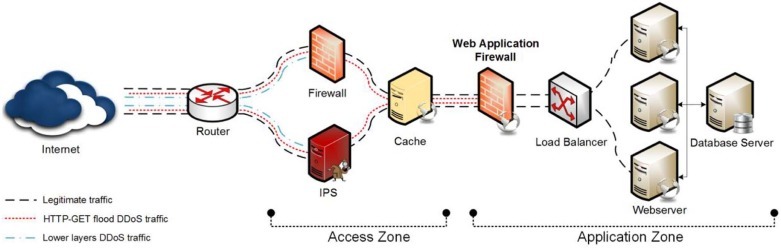
Protocol Attacks
These cyber attacks target the vulnerabilities that drive Internet communications, protocols, or procedures and slow down the entire network. Protocol Attacks have two main types:
- SYN floods: In this case, the attacker is paired with TCP. The attacker sends TCP requests to his victim and waits for the target to respond. After that, it does not respond to the termination of operation, resulting in the accumulation of a large number of requests and, ultimately, a system failure.
- Smurf DDoS: In this case, the attacker takes malware as helpers to create a network packet attached to a false IP address. The message that is the package contents requests a response from the network. In response, the hacker sends back the answer to the network IP address and thus forms a closed circle.
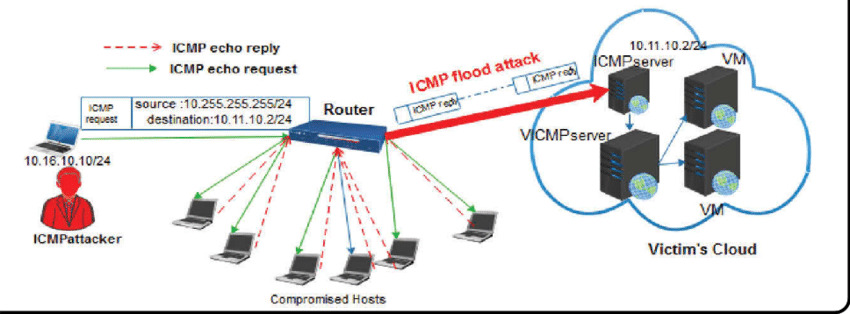
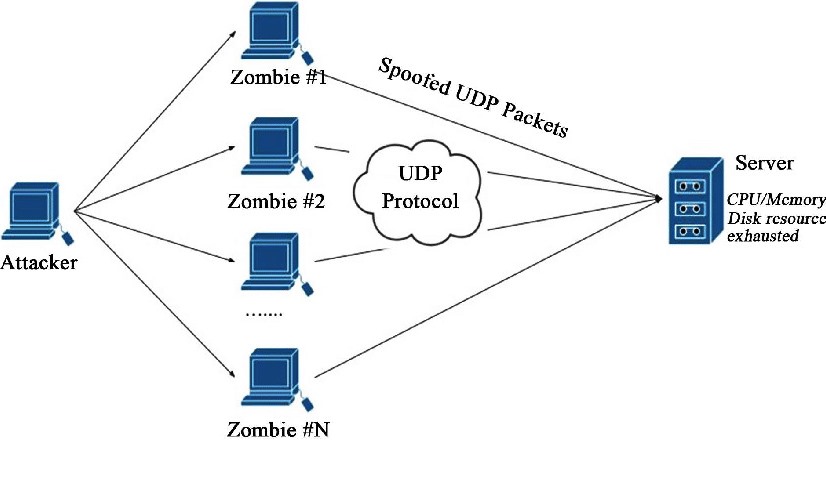
Volumetric Attacks
This attack differs from the others in that it consumes the victim’s available bandwidth based on the number of false requests that overload the network. In addition, the attacker creates traffic that blocks access to legitimate user services and thus prevents incoming and outgoing traffic. List of the most common volumetric DDoS attacks:
- UDP floods: This attack allows an attacker to restart ports on the target host of IP packets that contain the UDP protocol without saving the state.
- DNS amplification (or DNS reflection): this attack can redirect many DNS queries to the target IP address.
- ICMP flood: This strategy involves querying false ICMP errors to restart network bandwidth.
6 Best Practices for DDoS Attacks Protection
The proper network usage habits will help you warn yourself against suspected attacks. Therefore, below we will consider the most ordinary precautions against DDoS attacks.
1.Create a DDoS Response Plan
If you want to learn how to react to the intended DDoS attacks, you should develop a plan for yourself and your company. This is to protect yourself from all sorts of risks.
- Clear, step-by-step instructions on how to react to a DDoS attack.
- Escalation protocols.
- Go-to staff members.
- A list of mission-critical systems.
- A checklist of all necessary tools.
- Team responsibilities.
2.Ensure High Levels of Network Security
Network security is one of the essential elements of preventing any DDOS attack. To protect your business from attacks, rely on the following rules of network security:
- Firewalls and intrusion detection will be excellent barriers to scanning traffic between networks.
- Antivirus software that can detect and remove malware and viruses.
Web security tools. Their goal is to filter the threats, block anomalous traffic and find indicators of compromise (IoCs). - Tools that can prevent spoofing and check the source address to match the traffic to the original address.
- Network segmentation divides the systems into clusters with individual protocols and security controls.
3.Have Server Redundancy
To make the attacker’s work more complex, you must use multiple distributed servers simultaneously. In this case, if the hacker successfully launches a DDoS attack on one device, the other servers remain unaffected until the target system is back in operation. Servers must be located in different locations and processing centers to ensure that you do not have single points of failure. You can also use CDN (Content Delivery Network) to help distribute the load evenly between different servers.
4.Look Out for the Warning Signs
Keep an eye on what’s happening on the device and network to understand new changes. Here are the standard features of a DDoS attack that tries to cause damage:
- Poor performance
- Communication failure
- High demand on the endpoint or one page
- Traffic flow from users with ordinary traffic
5.Continuous Monitoring of Network Traffic
Another excellent method for detecting DDoS activity traces is to use continuous monitoring.
ensures that you can detect DDos attack with it before the attack is complete. The group can present everything about typical network templates and network traffic activity. Constant monitoring can ensure the detection of signs of an attack that occur at any time, whether working or non-working days.
6.Limit Network Broadcasting
The hacker who oversees the entire attack most likely sends requests to every one of your devices, thus increasing the impact. But if security limits network broadcasting between devices, it will be able to counter that. Limiting broadcast forwarding is an effective way to counter a hacker’s attempt to attack.




