What is Trojan Dropper?
Trojan Dropper, also known as "Trojan Dropper Agent", is a type of malicious software that has no functions but the delivery of other malware to the attacked system. To make the impact more massive, droppers commonly feature the ability to unite into botnets – networks of computers that subordinate a single command and control center. Then, at some point, all this mass of bots receives the command to deploy malware. The latter may be anything – from adware and browser hijackers to spyware and ransomware. However, more sophisticated and advanced things like the latter are preferred, as there are more simple and cheap ways to distribute advertising malware.
That class of malware was first classified as a separate one around 2007. Different examples of malware, particularly trojans, were detected to be capable of loading other malware even earlier – but no one called it a determinative feature. Droppers always were – and remain – eminent greases of malware spreading. The ability to deploy malware to the botnet is available for sale on the different Darknet forums. Still, there are a lot of cases when these networks were flooded with different malware, and any new activity made no sense as all the valuable information was already leaked.
Trojan Dropper Overview
Same as any other malware, Trojan Droppers should first find their way into the system. One of the prevalent ways of spreading these days is email spam – and that remains true for droppers as well. But as this malware is particularly oriented on single users rather than corporate networks, methods like software cracks and adware are appreciated as well.
Email spam is supposed to fit the dropper into the file attached to the message. This practice appeared long ago but gained immense popularity only over the last 5 years. Any type of file that can run the script (and desirably carry this script under a disguise) will fit. In most cases, an MS Office file is put to use, but changes to file execution policy made by Microsoft forced crooks to get back to seeking other forms. Regardless of the file type, running it activates the script, which contacts the command server and gets the payload.
Cracked software contains the same script, or sometimes even the exact payload within the installation file. Handymen who manage to circumnavigate the license protection of a program/game often seek monetization, as their job is not particularly easy and is outlawed. Hackers, on the other hand, offer a pay for each malware installation. Donations or any other form of rebate for their job is not that stable and promising – thus there are enough people who decided to bend the rules once again.
Droppers Analysis in 2026
After making its way into a system, droppers don’t do a whole lot of actions. To help the command server distinguish a new system, collects a small blob of information. It is generally the OS version and builds, system IP, username, and presence of antivirus software. After that, malware receives configurations from the command server and starts idling, waiting for orders to deliver malware or self-delete. The self-removal action is especially often when the dropper belongs to a so-called non-persistent type. Overall, infected devices (a.k.a. bots) will emit a config message periodically, to notify the C&C if they’re still running.
When it’s time for the action, the command server sends a message to all the bots, which contains the IP address of a secondary server where malware can get the payload. It may be both a stand-alone server rented for a single day, as well as a compromised website that used to belong to someone else. The contents, however, will remain the same – DLLs with malware that the dropper should download and run. Running it, however, is not a routine procedure.
There are a lot of possible ways to make the malware run. Normal .exe file run, however, is not an option, since it is too easy to track. For that reason malware opts for a DLL file format – it is way easier to run stealthily. The latter is done by loading the library to the memory using the system process called rundll32.exe or by injecting it into an application that has bad to no DLL checkup.
Types of Trojan Droppers
Despite their initial simplicity, droppers have their classification that derives from the time they are going to be present in the system. Those types are called persistent and non-persistent. Still, most of the modern droppers are created to be switchable from one mode to another, depending on the needs of its master.
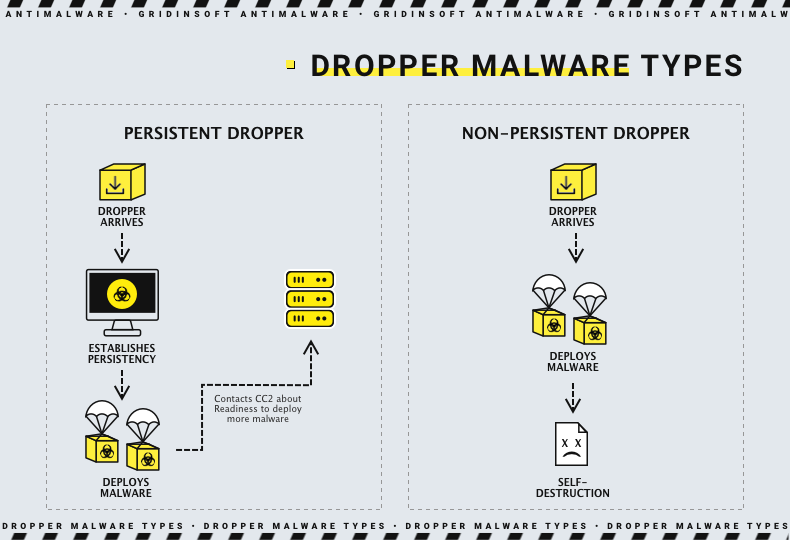
Persistent droppers keep running in the background of an infected system unless there is a command from the C2 server to stop. Usually, "stopping" means not only suspending operations and command execution but also self-removal from the system. Persistent droppers are generally used when hackers want to create a network of infected systems and take payments for bringing more payloads.
Non-persistent droppers aim at hit-and-run tactics. They never stay in the infected system, preferring to self-delete as soon as the payload is brought. This functionality is mostly demanded when the dropper is loaded into the system with the use of another loader. Alternatively, hackers may perform a targeted attack that does not involve botnet establishment, and the fewer paths remaining in the system – the less the chance of early detection.
What is the purpose of Trojan Doppers?
It may be not that clear what is the need for dropper malware. They use pretty much the same spreading ways, and perform actions similar to other malware – so why another entity is needed? The answer requires a bit deeper understanding of how the malware world works.
The vast majority of droppers malware are used as infrastructure elements, i.e. botnet establishment tools. Contrary to botnets under the rule of backdoors, ones controlled by droppers do not commit DDoS attacks or serve as proxy servers. Instead, these networks are offered to malware masters who want to perform mass-spreading of their malware. It may be any kind of the one – spyware, ransomware, stealers, or backdoors. But the result is always the same: the network is flooded with various pests, and the owner of this dropper network receives a hefty pouch of money. It is not about hacking, it is about making money by offering services to hackers…with a bit of hackery beforehand.
Another case, which is even more specific, is when the crooks use the aforementioned non-persistent droppers. The peculiarity of this situation lies in the fact that in this case dropper is not for creating a network, but for hit-n-run action. High-precision attacks require to be sure that the environment suits the attack. Dropper in this case acts like an initial access tool, the one which will get into the target environment, check if it is not a honeypot, deceptive trap, virtual machine or any other trap. If everything is smooth, the entire payload will be delivered.
Droppers Malware Examples
The peculiarities of droppers do not end up with the reasons for their usage. Loaders were evolving not from scratch, but from malware samples that were capable of delivering other payloads. Furthermore, malware samples that were designed to have certain functionality got modifications that made them droppers as well. As a result, it is quite hard to say if a certain malware is a pure trojan dropper, or if it is more correct to classify it differently. For that reason, we will have a look at the most notable examples of trojan droppers that can deliver payloads along with its main functions.
Emotet
Trojan Emotet is probably the most known example of malware that gained loader capabilities with time. The thing is, at some point, these capabilities became dominant over the initial functionality – data stealing. Being a successful stealer, Emotet features numerous detection evasion techniques. In combination with the ability to introduce various other malware, it becomes a challenging quest to find and disarm this malware before it strikes badly. Apart from that, Emotet networks are divided into eras, which rely on different software and feature different architectures. The only possible way to get this structure down is to physically stop the servers from running – and that is what was done in January 2021. That did not kill this malware though but made its activity way more random.
Amadey
In the background of Emotet - a successful jack of all trades, Amadey Dropper may look dimmed and dull. Still, it is an original dropper, the one which cares about nothing but loading the other malware. It does not steal a lot of data about the system, offering instead stealthiness and efficiency in payload delivery – essential qualities for the loader that forms a botnet. Appearing in 2018, it remains active and regularly appears at the top of the single-user infections chart.
TrickBot
The second name of this malware – TrickLoader – says for itself. It is yet another example of malware that can be used for both spying on the infected system and spreading other infections. Contrary to Emotet, TrickBot was designed already featuring the dropper capabilities. Moreover, it has native appliances to perform lateral movement in the infected network – and do the same to payloads it brings into the network. Being openly ruled from Russia, TrickBot was used in numerous state-sponsored cyberattacks against government organisations in the USA and Europe.
QakBot
Yet another example of a multi-functional threat that was designed as spyware with malware dropper functionalities. QakBot is also known for being one of the oldest malware families currently running – it started its activity in 2007. Being able to deliver any payload, it generally concentrates around Conti and Ryuk ransomware. Sophisticated detection evasion and anti-analysis techniques allow it to remain potent despite its age and ill fame.
CobaltStrike Beacon
CobaltStrike is far from being a typical malware. It is a special malware orchestration toolkit, developed and marketed specifically for red team hackers – but was leaked to villain hackers at some point. It contains best practices for detection evasion, lateral movement and retaining stable control of the environment. The client part of the toolkit, called Beacon, is actually a simple dropper, that allows master to access the system, and spread instances of a Beacon to other computers in the network. Constant updates, together with masterful design and numerous features that help it to fit almost any demand make CS an enormously serious threat.
How to Protect your PC?
The vast majority of dropper malware rely on remaining stealthy, even though they can deliver a “noisy” malware – the one which will definitely attract attention. But that is a part of the plan: victims are getting distracted by the disastrous consequences of a ransomware attack, ignoring that it could not appear out of the blue. The most efficient way to counteract the downloader threat is to prevent its appearance at all.
Be careful with the emails you receive. Threat actors should be inventive – and they are, otherwise they will not keep up with the modern trends. Topics they use to make the victim react may be pretty general, as well as ones reflecting the surrounding events. In some situations their emails became convincing enough to be hard to distinguish from a regular one. However, there are a couple of details crooks cannot counterfeit.
Email address they use to send the message will always differ from one that the organisation uses for mailing. They will probably try to pick the closest email address possible, but you will still be able to see the difference, if you have ever received an original message. Another thing is conversation style: threat actors rarely know their victim’s name, thus their option is using depersonalised appeals. Companies know your name, or at least a nickname, thus seeing “Dear User” or your email address instead of the common naming should be a red flag.
Stop using cracked software. It may be very tempting to use a program or play a brand new game for free. This, however, breaks the copyright law, and may end up with very unpleasant legal consequences. Moreover, cracked programs and apps that allow circumventing the licence checking are also a popular source for a wide range of malware. Cracking the program supposes rehashing internals of a program/game, and adding malicious code at this stage is a pretty easy task. Apps for breaking licence checks – keygens, licence spoofing tools or things like KMSAuto – often require your antivirus to be disabled for correct work. And if that program contains malicious code (and that is likely due to its illegal nature), nothing will stop the infection.
Don’t interact with dubious advertisements. By design, ads on the Web are not a thing you should avoid. However, the latter is true for the banners you see on legitimate websites. Ones published on forums, sites that spread pirated software or films, or other less than trustworthy places may deliberately contain something malicious. A common thing met under such banners is potentially unwanted software, adware and trojan viruses. The latter may have any functionality, from spyware to ransomware or trojan droppers.
It is also important to remain vigilant even with trusted advertisements. After Microsoft banned the execution of macros in MS Office files that came from the Internet, hackers started seeking for an alternative way to disguise their malware. As it turned out, moderation in Google Search ads may sometimes malfunction, ending up with numerous counterfeits of advertisements of legit freeware. Trying to follow these ads will throw you to a copy of a downloading page, but the file you’d get is a malware installer.
Use anti-malware software. Attention and awareness is not always a guarantee of successful malware avoidance. Sometimes, crooks overwhelm themselves with a completely new tactic that is impossible to predict. For that reason, having a software that will take care of these unpredictable situations is essential. GridinSoft Anti-Malware will fit perfectly for protecting the system from trojan-dropper, ransomware and pretty much any other threat. Its advanced scanning system will detect even the most modern hazards, and proactive protection will safeguard your daily activities – including ones on the Internet.