Deception Technology
Cybersecurity Deception Technologies are toolkits that offer the functionality for tricking hackers into compromising themselves. With these kits, it is possible to create an artificial environment that will attract hackers, revealing their penetration methods, steps after the initial compromise, and targets in the network. Deception Technologies are the ideological successors of honeypots, with more automated and specialized software used for this purpose.
What is the difference between honeypot and deception technology?
Honeypots serve with the same targets - attracting the breachers and tracking their activities in the attacked environment. In that way, cybersecurity teams can know more about the tools their company is about to be attacked with, how the hacker breaks in, the steps it takes after the penetration, and so on. In rare cases, using honeypots, it was possible to compromise the hacker itself, or at least get the information that can be valuable for executive authorities.
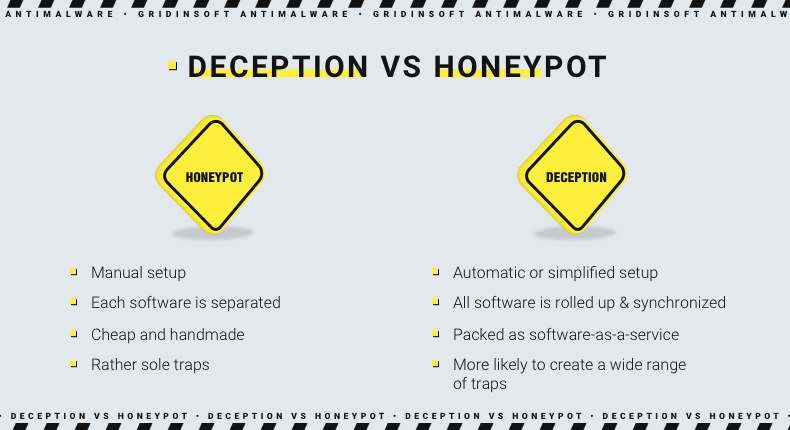
However, no software was designed to establish honeypots. Most traps are about to be set manually, using the programs already used in the network or third-party ones that fit the need. That makes honeypots inconvenient, especially when the security team aims to gather as much information as possible from these traps. The other problem is that using non-specialized software is related to risk. You can unintentionally expose the facts that should not be available to the ensnared hacker. Moreover, if you are not skilled or attentive enough, you may easily make it possible for hackers to move forward to your network.
Deception technology solutions offer software specialized in establishing and maintaining the decoys. It already contains everything needed to automate this action and make the environment as secure as possible. This automation makes the net of snares easy-to-scale. After the integration into the event management solutions that are running in the network, deception technology becomes a perfect provider of information for proactive attack mirroring.
Importance of Deception Technologies
Both malware and ways of its distribution were always evolving fast enough to get ahead of anti-malware software development. That eternal race - malware analysts after malware developers - is going with much higher temps these days. Staying aware of new attack vectors and penetration approaches became even more important, as new hazards appear twice a week. Simply deploying the anti-malware solution and following the basic cybersecurity rules is efficient. Still, it does not train your cybersecurity team for the actions in case of a security breach.
Corporate security is not about just pressing the button “remove malware” after the anti-malware software detection. Sure, security solutions are able to detect and remove the threats automatically, but that is not over. To effectively protect the environment, the security team should not just delete the malicious element but also block the way it gets inside and make the steps inside the network impossible for further intruders.
Cybersecurity Deception Technologies can uncover the breaking point and analyze the behavior without any losses for the corporation. Sure, the next attack will likely have a different path, but you will be aware of one of your weaknesses and can eliminate them all one-by-one. When you are not losing a thing, it is possible to repeat this “exercise” as many times as possible, increasing the cybersecurity team’s skills and effectively revealing the breaches. And Deception Technologies can create a dummy for hackers that will be as realistic as possible.
How do Deception Technologies work?
As it was mentioned, the key point of both honeypots and Deception Technologies is to trick the hacker into acting inside of the artificial environment as it acts inside of a breached network. Hackers are rarely reckless enough to start the actions without a check-up of the environment. Some badly-established traps based on virtual machines can be uncovered by just opening the Task Manager - and finding the process that is related to CPU virtualization. After uncovering such a poor decoy, crooks usually do nasty things, like flooding the environment with insulting notes and disgusting pictures or leaving the zip-bomb before disconnecting.
So, as you can see, one of the key functions of deception tech is the art of disguising the trap. At a certain moment, hackers will likely understand that they are acting within the artificial environment. The main question is how many actions they will do before uncovering the trap. Each step they do on the compromised machine will be recorded, analyzed, and then considered to enhance corporate protection.
Another important part of the deception technology's functionality is securing the environment which is about to be penetrated. Once you give the hacker a chance, you should give it no ability to go further. That will be a very unpleasant experience when the crook manages to perform a lateral movement - from the trap into the live network. Moreover, it is important to place the information that is not very important for the company but may attract the crooks.
When the trap is set, you must wait for the hackers to start the attack. If created by proper software, they will look like an easier and more obvious target - an exposed endpoint or the secretary’s computer. That’s no reason for hackers to search for a harder entrance point, especially since it does not look suspiciously easy to reach.
Setting up a trap with Deception Technologies brings much pleasant information for cybersecurity improvement. Usually, decoys are set in a manner that makes legitimate connections impossible. Hence, all external connections to the fake systems are counted as malicious, so the info about this connection will be a great addition to the network ban list. Along with the IP-address, the cybersecurity team may also be able to see some information about the device and operating system that is used by the crook. But, of course, the main piece of information that is the most valuable output of any deception system is the steps the hackers take inside the network.
Deception use cases
We discussed the general cases of using a decoy without detailing the exact purpose. However, the effectiveness, role, and even information delivered by the deception system differs depending on the chosen form of the decoy. Most software solutions offer public-facing assets, network elements, and endpoints. Let’s check out what differences these decoy variations have.
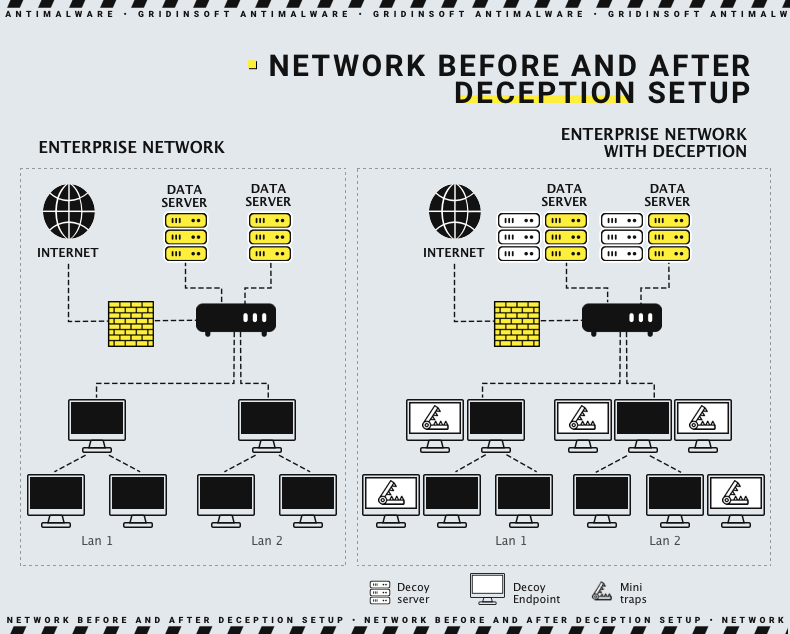
Normally, >public-facing assets are the resources available to a broad public, so everyone can connect and see the contents. Meanwhile, they always receive a certain amount of malicious traffic, which is quite hard to filter. Decoys can be set up to be perceptible during the network scanning with specific tools, but they will be unreachable to normal users. Such dummies will attract the attackers along with regular assets, so security administrators can ban the IP addresses connected to the decoy from connecting to any of the assets. This kind of deception technology is effective against DDoS attacks and brute force attempts.
Network elements - workstations, local area networks, and IoT devices - are the usual intermediary targets of any cyberattack. Before going to the endpoint, hackers try to infect as many machines inside the corporation as possible. Decoy among them will likely be the easiest target, which looks like an obvious beginning for the hackers’ walkthrough. As it will not be reachable by regular users, any actions and states of this machine different from the standard are considered indicators of compromise. Deception like that one is great at collecting information about the attackers’ methods and can act as an early warning.
Endpoint decoys are rare and hardest to set up properly, as they are located deeper in the network than all other types of snare. First and foremost, there is an increased risk of breakthrough into a normal network or the uncovering of the trap. The fact that the hacker managed to reach the endpoint means you have done something wrong or your higher-level decoy worked perfectly. Such traps should be linked to the network element decoy. Otherwise, getting this deep means your network is compromised. Endpoint traps set with a deception system give a view of the attacker’s targets and also reveals the software it uses for the last stage of the cyberattack.
Should my company use deception?
Almost every company faces cybersecurity incidents each week. Although it could be just DDoS attacks on public resources, or a brute force of a login form, one day, the attack could take an unusual vector. To slow down or completely confuse the crooks, it is better to have a decoy that may distract their attention. If they attack these traps first, you will be warned about the possible attack, and, more importantly, be aware of the methods of penetration, used software, and possible targets. For middle and large companies, deception technologies are essential to deal with threats and improve security systems.
However, Cybersecurity Deception Technologies are not ultimate and have their imperfections. When used solely, they still require high personnel skills, as they should manually analyze all the outputs of the decoys. Most deception software solutions usually use SIEM and SOAR systems, which can automatically analyze the data and offer the corresponding actions. Another, more classic sort of security software - EDR or XDR variants - is also recommended since you never know if the decoy is the first target. To keep the environment secure, and be able to apply the changes, all of these software solutions should work jointly. Still, it is pretty expensive and thus unavailable for certain companies.
Using deception technology is strongly recommended for medium and large companies, who have both qualified personnel and security software that will intake the information. Despite being useful in small companies as well, it may be too expensive to maintain this system.
Frequently Asked Questions
Cybersecurity experts define 3 types of deception technology applications - attack detection, active defence and disruption. Attack detection deceptions are set up in the manner that makes them an early alarm system. They are most likely to be the first targets of hackers, and any activity inside of these decoys is an indicator of compromise.
Active defence decoys are supposed to give the crooks as much freedom as possible, in order to bait them for uncovering the details about the used tactics, software, and maybe even personal information. That sort of trap is quite hard to create, since it should have minimum signs of being a pitfall.
Disruption is a technique that confuses the hackers during the attack. While they are trying to move through a network, deception will likely distract them and gouge about the next steps they will need to take. Disruption decoys are more about a proactive approach, as they should be managed during the ongoing attack.
