
What is Honeypot?
Honeypot is a particular system established at the endpoint to monitor the activities from applications and incoming connections, imitating the original endpoint. In this manner, the security system and the specialists can detect potentially malicious activities and create a counteraction. That may be the counterfeit of an internal server, a computer in the network, a website server, or whatever can attract cybercriminals.
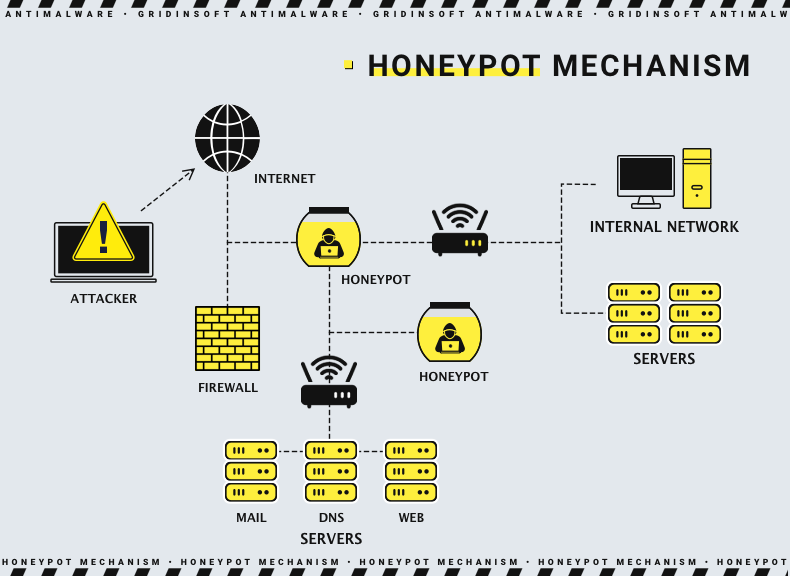
Honeypot can be established manually - by a cybersecurity specialist, or with the EDR system. The latter offers more automation, but in some cases, the linearity it creates may decrease the effectiveness of such a trap for cybercriminals. The manual setup gives more flexibility but is risky when you lack the experience of such a thin environment. Wrong honeypot settings can reveal the honeypot presence or even completely ignore the malware.
History of honeypots
Although cybersecurity as a science formed only in the early ‘00s, the honeypot, or at least the environment that had the same functionality, appeared in the late ‘80s. The use of such a system is described in The Cuckoo’s Egg, the book issued in 1989. Its author, Clifford Stoll, set up a trap on an unknown hacker after revealing his presence in the Lawrence Berkeley National Laboratory’s network. To get more information about the intruder, Clifford performed the steps that exactly repeat the modern honeypot approaches. In the end, he uncovered the type of connection, the hacker’s location, and, what is more important - how did it get into the network.
The first example of what exactly functioned as a honeypot was documented in 1991 by the same Clifford Stoll while he was working for AT&T Bell Labs. The hackers tried to get the password files from the attacked system - but were intercepted by Mr. Stoll. He established an environment that was hard to distinguish from a real system and observed all the steps hackers did in the honeypot.
These days, honeypots generally serve corporations of different sizes, helping them to mirror the attacks. You will not likely read about the successful usage of this technique in newsletters - since it is not as interesting and clickbait as the information about cyberattacks and a huge ransom asked. And, exactly, the absence of the latter is strictly related to the efficiency of the former.
Types of Honeypot systems
Cybersecurity vendors classify the honeypots depending on their complexity and the type of system they mimic. By complexity, they divide low-interaction and high-interaction honeypots; for the chosen decoy, they name email (spam) traps, database, malware honeypots, and spider honeypots. Let’s look at them from the last to the first.
Spider Honeypot
Spider honeypot is a type of trap aimed at web crawlers or spiders. They are searching for the specific IP addresses that can be useful for the attack. Since that address will likely never be seen by a normal user, all connections to that IP address can be considered malicious. In such a way, system administrators gather the database of malicious external IPs - correspondingly to the incoming connections to the “exposed” spider honeypot page.
Email (spam) traps
Email honeypots are similar to the spider ones since they suppose a similar approach. To confuse the bots that stalk the websites searching for email addresses, administrators add a specific address that is not used for regular mailing. Again, it is not visible to the users - hence anyone who texts on this email uses illegitimate email collecting and thus must not be trusted. All messages received to this address are considered spam, and the sender’s emails are added to the spam list for “white” mailing addresses that are not involved in the honeypot.
Database Honeypot (database decoy)
Database decoy supposes the use of several exposed databases. Usually, such a lure contains several exploitable elements that attract cybercriminals. The data inside, however, has no value - it may be the 10-years-old report about toilet paper shopping. Sometimes, these databases repeat the structure of the currently used in the company. Such a step is done to use the hackers as a red team without their willingness. Crooks reveal the vulnerabilities and exploitation techniques, which are then diligently acquired by system administrators. It's a perfect way to secure the existing breaches and create a counteraction to the approaches used by crooks.
Malware Honeypot
This trap type sounds strange, but it has properties close to the database decoys. Malware honeypots are the lures that imitate the bunch of apps, or the API, to bait the crooks to act as they would in a regular environment. In that way, cybersecurity analysts can collect the data on the potential attack vectors, including the used vulnerabilities and connection ways. That gives the company the chance to get ready for the possible attack - set up the security solution, prepare the internal environment, and so on.
High-interaction Honeypot
High-interaction honeypots suppose that the trap will have a lot of elements to interact with. The more things crooks will touch - the more paths they will leave, giving the company more information about what they need to be ready for. Such honeypots usually imitate a bunch of databases or even the internal network cluster - the target size will surely attract the crooks. If everything is set up properly, a high-interaction trap will be almost impossible to uncover. However, it has several disadvantages that must be considered - such a large honeypot will require the corresponding amount of computing power/server space. Moreover, the complexity of such a structure creates a significant risk of compromising - crooks can move further from the honeypot to a genuine network.
Low-interaction Honeypot
Unlike the previous type by complexity, low-interaction traps contain fewer elements to attract the hacker’s attention. Meanwhile, they are easier to configure and maintain and have fewer penetration risks. Nonetheless, it is not a great way of reconnaissance - hackers cannot leave a lot of paths in this type of honeypot. But it is still enough for having some kind of alarm about the attack attempt.
Hackers and Honeypots
Honeypot looks like an ultimate solution against intruders. It not only distracts the attacker from the genuine server or network but also compromises its methods. However, hackers have the trump up in their sleeve, too.
Setting up a honeypot that hackers will not detect is not an easy task. It is like an eternal race - security specialists doing their best in the setup while hackers are trying to find the trick. In some cases, the prudential settings in the malware they are going to run can detect the signs of a honeypot and prevent it from running. Such settings can be triggered by a specific process running in the attacked system, an unusual graphic adapter, or the system configuration that is not typical for a normal environment. That does not save the crooks from exposure - they still show their connection IP address and the actions they did before the malware refused to launch. But that does not show all the steps they do.
Besides the chance for a honeypot to be detected, there is also a high chance that crooks will try to attack several surfaces. Well-orchestrated cyberattacks rarely start without a diligent reconnaissance of the targeted network/server. Therefore, hackers will likely know about the other weak spots and will exploit not only the weakest (the honeypot) but also the several tougher ones. That may give the crooks the desired result - getting inside the corporate network. For sure, the actions on the honeypot will trigger the alarm - but the actions must be taken as soon as possible since you never know if the crooks will succeed at hacking the other places.
Pros and Cons of Honeypots
As you can see by the description above, honeypots are handy applications in corporate cybersecurity. However, they are applications - not a stand-alone security solution that may run autonomously. The data about the attackers gathered by the trap must be analyzed, and the corresponding actions must be taken. But let’s divide all positives and negatives of honeypots on separate lists.
Honeypots are good at:
- Gathering the info about threat actors. Other monitoring systems cannot give you such clear information about the attackers. Even when you have an EDR system that records each little action, the notes will surely be confused with the actions of regular users. Meanwhile, honeypots face you tet-e-tet with what attackers try to do in your system - without excessive noise.
- Extended detection range. Security solutions - both EDR and regular antiviruses - rely on the protection from external threats. They are physically unable to detect or counteract the insider threat - meanwhile, it is considered one of the most dangerous threat types. On the other hand, Honeypots can attract the internal intruder and compromise it.
- Reusability & Evolution. Once established, honeypots can be used continuously to gather information about the attackers and distract their attention. You can reconfigure them for your needs after one attack, and they will successfully withstand another one later. After processing the data received from the honeypot, you will be able to make it more suitable for usage in the rapidly changing malware environment.
However, honeypots have the following disadvantages:
- Risks of use. The proper configuration of the honeypot will give suitable protection rates. However, any weak spots or unprofessionalism can be punished by hackers - they will get through the trap right into the entire network. Hence, honeypot setup requires not only the shell and EDR solution monitoring but also twice or even triple check-ups of all elements connected to the internal network.
- Hackers’ reaction. Usually, hackers who discover that a honeypot fooled them are not pretty happy. To revenge, they can begin spamming the environment with random commands, upload random files and do whatever they want - to make the obtained logs useless to read. In cases when the honeypot mimics the system, crooks may launch vandal malware that will destroy the established environment. That will not harm the internal network or servers, but the practical main effect of the honeypot is getting lost.
