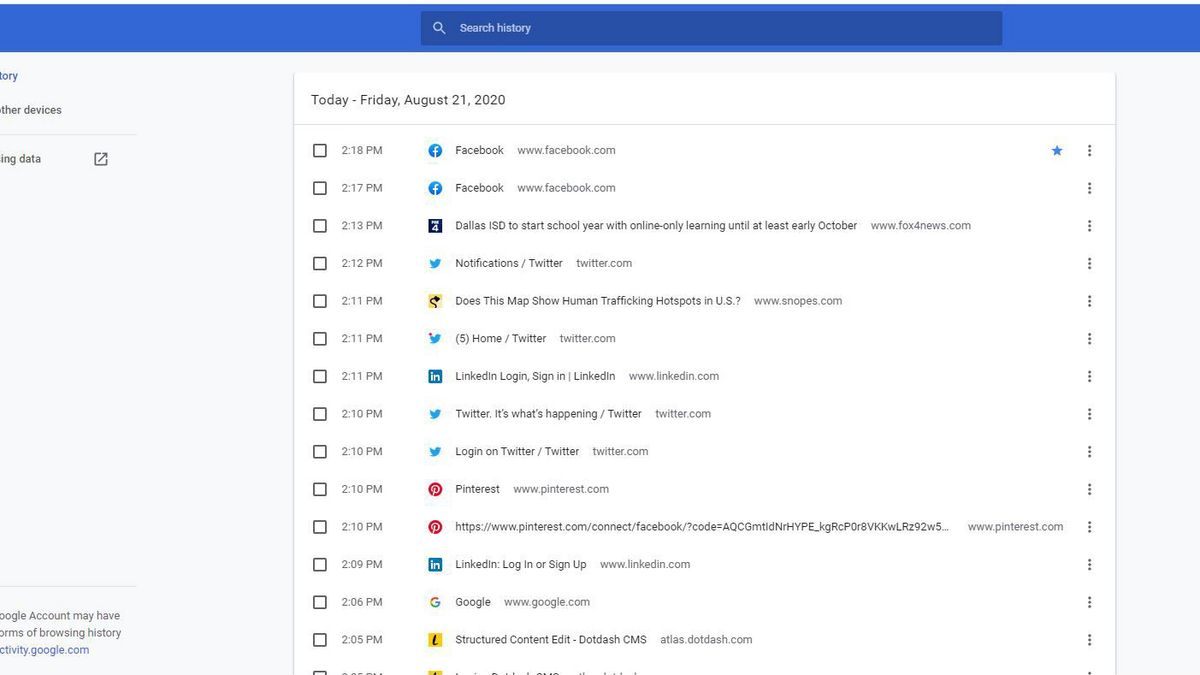
Digital Footprint
Digital Footprint is the compound of your network activity, visualised is different form. It can be represented as a list or as the image of your person - generally depending on the type of footprint that is supposed (or available) for use. A passive digital footprint consists of browsing history, cookies, and similar information - they don’t say much about the person. This type of information is a welcome find for advertisers, in particular - social networks that offer targeted ads.
Active footprints are more about uncovering the user's personality. The latest purchases in the online stores, posts on social networks, and workplaces mentioned on LinkedIn - such stuff creates a wider and more relevant view for the person. Active digital footprints may be the object of interest of employers, people who are interested in your person, or even criminals. The methods of digital footprint exploration are represented in open-source intelligence.
Who uses a Digital Footprint?
Employers may need more information about you when applying for a vacant position. That is especially needed when there are several candidates on a single seat. To make a decision, HR-managers may dig a bit of information about the job candidates. Then, the psychological profile is made based on social network posts and other available data. Besides the search on social networks, this approach to digital footprint exploration also supposes the use of specific search engine queries that allow getting the data that is usually hidden from the human eye.
Interested party. When you are a celebrity of some kind, it is obvious that you will be the object of someone’s interest. Therefore, it is not surprising that those people will dig into the places you were active at. Subscriptions in social networks or blogs, purchases in online shops, even financial activities - they will be happy to see all these things. Such a survey is much closer to net stalking. However, people rarely react when someone stalks a celebrity.
(Cyber)criminals. We put the word “cyber” into brackets since the criminals who pay attention to someone’s digital footprint are not obligatory cybercriminals. The detailed information about your person, at least the facts you share with the public, makes planning the crime easier. Much more interest is paid to those who own something valuable or have a decent income - they have something to steal. And there is no difference in how it will be stolen.
Privacy Concerns
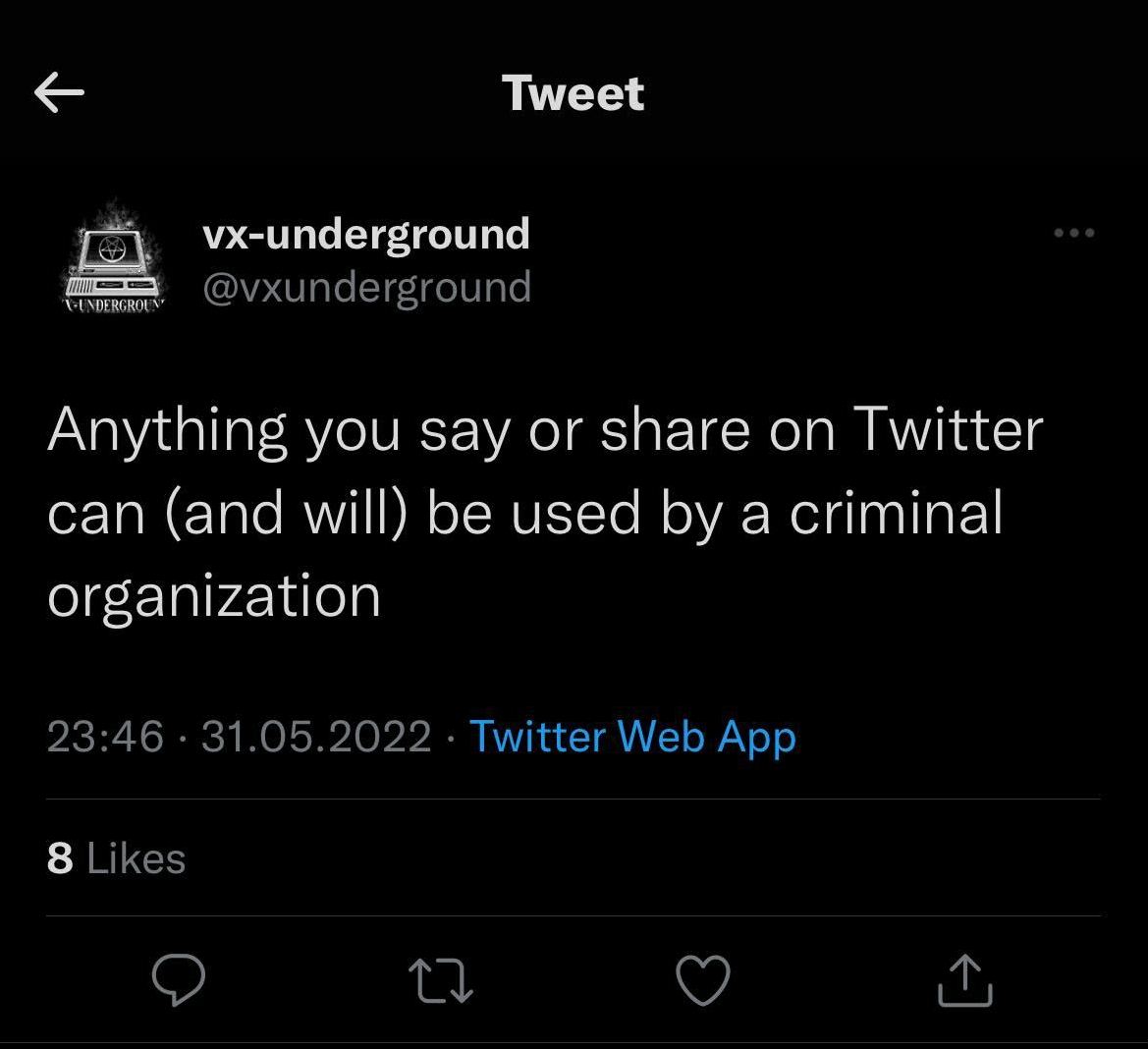
Just as anything that touches private information, digital footprint causes a lot of disputes online and offline. Digital footprints are the object of OSINT - not all things the latter collects are related to the former, but a lot of them do. And saying about collecting the information online ignoring the privacy concerns is inconsistent.
When we are talking about privacy, it is important to remember that it does not have a commonly-accepted red line. “Collecting the information about me is good by that point, but all further steps are counted as spying” - saying at least that sounds not pretty linear. Each person will set up its own “point”, even inside the separate categories. Therefore, it is better to describe all possible threats digital footprints may carry, and each reader will figure out for themselves if that is critical or not.
Social Networks Tracking
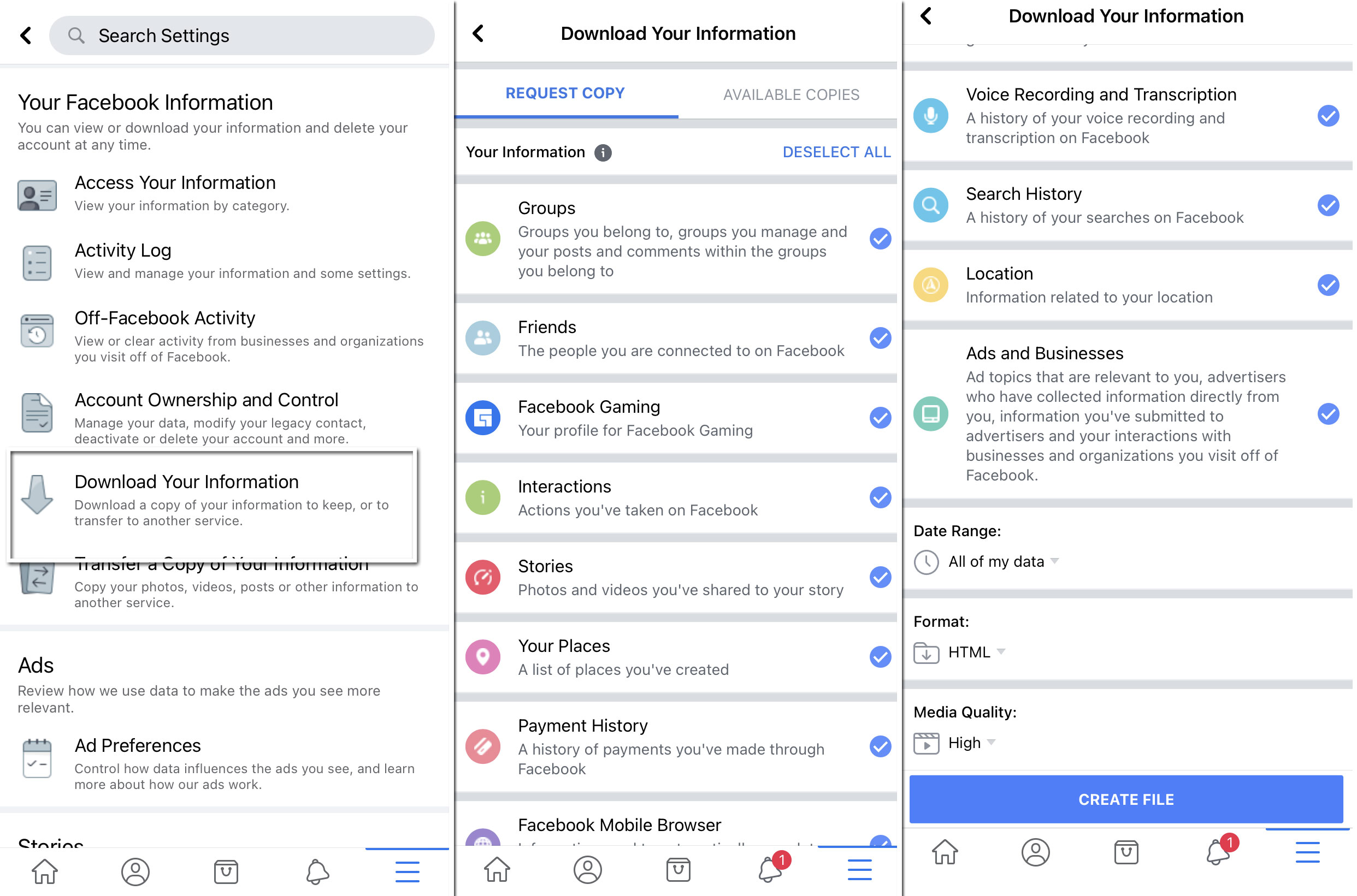
The vast majority of social networks and messengers we use track our activity. That may not be the problem while the collected information is not publicly available and can be restricted manually. Public availability is a questionable parameter since social networks do not share information about where the raw material for digital footprint goes and how it is stored. In case of a data breach, it may be exposed to the public or even to criminals - massive email spam or spear-phishing campaigns are frequently based on such leaks.
Another side of the problem is the ability to create a digital footprint of a person even without touching the data breaches. All you have to do is observe the account for a while. The aggregation of static information, stories, posts, and photos will create a footprint. Therefore, making your life public may be dangerous for you. Of course, the users may intentionally distort the information to skew the final result, but that case is rare when unaware.
Cyber-vetting
We have already mentioned this situation above. When you apply for the vacancy, your employer may be interested in collecting more information about your person. Sometimes, it is used as a stage of the employment process. That sounds legit, but the analysis of the footprint is pretty subjective. The person can be a high-skilled professional but will be rejected just because their political or other views differ from ones preferred by the HR manager. In rare cases, the candidate may be denied employment because of the absence of social network activity. From that point of view, it is better to spoof the digital footprint than to use your original one.
Identity Theft
Digital footprint is exactly the cast of your online identity. And you have the footprint collected means the ability to replicate it and use it anywhere. It is a significant hazard in the current state of social networks - you may miss the differences between the original account and the counterfeited ones. But it becomes a real mess when we talk about metaverses, where the crook may prove his “originality” with the facts from the digital footprint.
Obtrusive Advertisement
It is obvious that everyone dislikes excessive ads. Even when they are targeted and correspond to the things you are interested in now, seeing a dozen of them on each page is annoying. Social networks usually limit the number of ads you will see in the feed - otherwise, users will stop using them. However, ads on sites and social networks are not the only way of product promotion. Emails, direct messages, SMS, and even phone call spamming - all these things become incredibly efficient when you have a digital footprint of a victim. Spear phishing, which abuts spam ads, becomes more realistic as well.
How a person may use a Digital Footprint?
We said a lot about the disadvantages of digital footprint. It may be a hazard to your privacy and expose you to unnecessary problems - just because it exists. Still, it is possible to use it for your benefit. Keeping the information about yourself published can increase your trust in yourself. And in the digital era, people seek trustworthy persons on the Internet based on what they see. Still, there is a risk that the person will intentionally skew the information - to make the digital footprint more attractive.

Who can use a digital footprint to demonstrate itself to the public? Generally, those are people of public professions - like doctors, hairdressers, trinket manufacturers, or car repairing masters. They find most of their clients online, and even when someone advises this master in oral form, it will likely be reviewed by the online profiles. Facebook, Instagram, Pinterest - the pages on these social networks will depict each element of the person's professional activity. That allows the clients to review the quality of the job done by a master even before meeting it.
How to protect your Digital Footprint?
The risks related to the digital footprint are discussable since user opinions are divided among many parties. Similar to how we described the privacy concerns, we will explain the solutions that solve all possible problems. Each reader will be free to choose what he needs.
- Limit the types of data you share. A pretty obvious advice, but still effective. The less data about your person will be available to the public, the less the attack surface. However, certain risks are related to the absence of any footprint of yours online. That’s why choosing the complete absence of information about you is not the greatest idea. Ideal categories to restrict or completely cut off public access are your shopping activities, travel plans, and detailed banking information. These categories are used the most often when it comes to spear phishing.
- Actualise the footprint. When you cannot completely remove your digital footprint, manage to make it at least more actual. Seeing the more relevant ads and offers is better. So you need to remove the old accounts, clean up the subscriptions you are not reading, and delete the programs you are not using. That will actualize your digital profile, make it smaller, and may even save a penny for the ice cream.
- Use only HTTPS-protected connections. Most websites these days connect only through the HTTPS connection, which supposes using advanced data encryption technologies. Third parties cannot read the packages, even if they can reach the traffic flow. Sure, man-in-the-middle attacks are not very widespread these days, but still possible. And they may give the crooks the full set of confidential information they need to form your digital identity.
- Pay attention to the breach notifications. Even the worldwide-known companies with perfect images are not resistant to zero-day vulnerabilities. And when cybercriminals use these breaches, no good things will happen. They may use the access to the internal data as they please - cipher it, leak it and ask for a ransom, or use it for further attacks. Therefore, after the news about the data breach, it is important to review what dangers you have. Sure, crooks are not obliged to use this info against you - in phishing attacks or blackmailing, but it is important to be ready to react. Be ready to ignore the messages that may refer to the leaked data.
- Review the most sensitive information. Even when you are not publishing confidential information - such as banking data or medical info - it may leak in this or that form. Sharing it even with someone you trust is not a good idea, especially when you are sure this person has this information, but it assures that he forgot the details or lost the file. The fewer people know it - the better you sleep.
Frequently Asked Questions
- 1. Try to find yourself in a Google search.
- 2. Deactivate old social media accounts and check the privacy settings on existing ones.
- 3. Hide the information you don't want to share on messengers and social networks. If this is not possible, write false information.
- 4. If you can't remove the data from the site, get in touch with tech support and ask them for help.
- 5. Opt out of unnecessary newsletters and subscriptions.
- 6. Set up an extra email account for newsletters or registrations if you don't want to make your leading one light.
- 7. Think about the "right to be forgotten," recently enacted in Europe. This means that search engines will have to remove links to publicly available news from their search results.
- 8. Check e-commerce and retail accounts. If you have Amazon or eBay accounts that you don't use, consider deleting them.
- 9. Cover your tracks.
- 10 Create new accounts and start your online life from scratch.