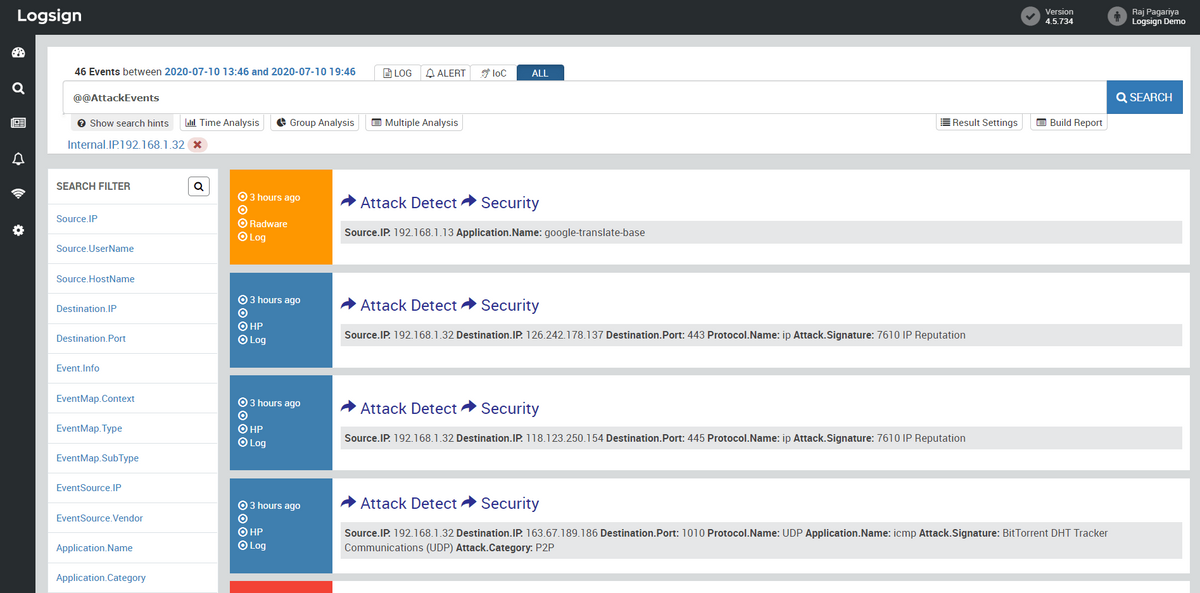
What is SIEM?
Security Information and Event Management (shortly SIEM) is a bunch of tools and techniques for researching the events in the environment where this system is applied. SIEM consists of two technologies that were growing separately from each other - Security Event Management (SEM) and Security Information Management (SIM). The former is responsible for monitoring and alarming the incoming events in the network (new connections, possible issues, and dubious behavior). SIM, on the other hand, is about analyzing logs and providing the corresponding conclusions to the analysts' team.
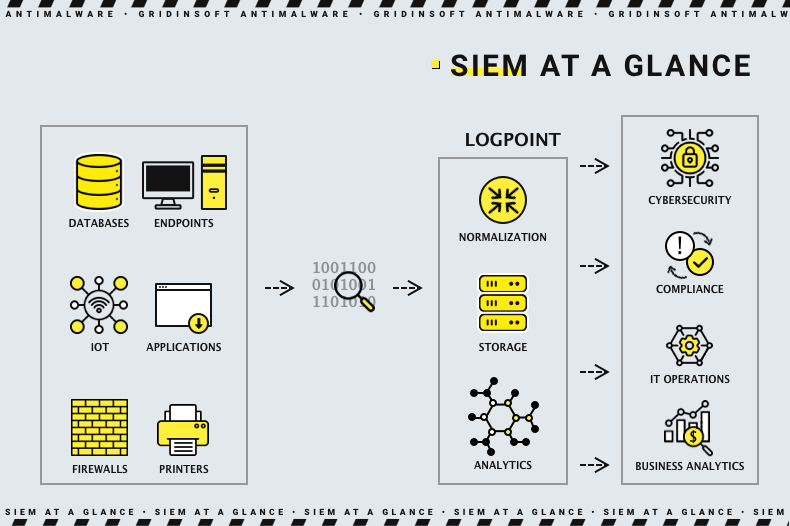
SIEM conjoins both of these approaches, offering a simultaneous logging of all events in the system and their analysis. This technique allows the cybersecurity teams to monitor the happening, detect the threatening elements and react to them. The reaction usually requires skills and software that make it possible to secure certain areas of the network. For a more effective and convenient response, companies opt for EDR/XDR solutions that allow them to apply the needed actions automatically for all of the units.
What are the SIEM components?
The SIEM process consists of 4 logical steps. The software that provides them is unitary, but these procedures are easily divisible. These are data collection, data consolidation, event notifications and policies of actions. All of them are running on a repeated and continual basis. Let’s check out each one, top to bottom.
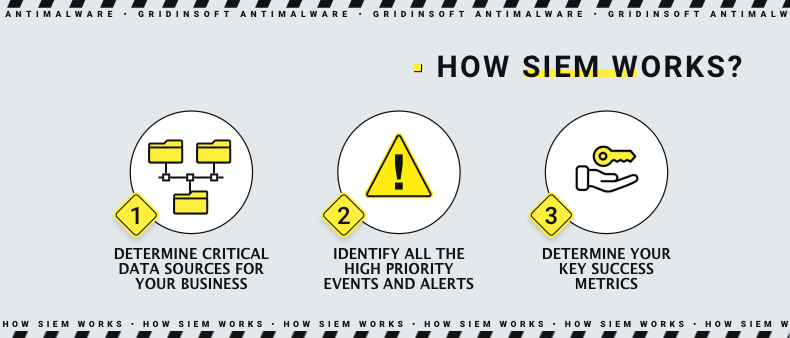
- Data collection is a part where the system collects all possible information about the events in the network. The sources for this information are workstations, endpoints and network facilities (i.e. firewalls, network switches etc.). Additionally, SIEM can gather information from cybersecurity software if the one is present and configured to share data with security information and event management systems. At this stage, the dataset needed for further analysis is formed.
- Data consolidation is the stage where the gathered information is analysed. To make it more convenient for systems and specialists, SIEMs automatically sort the incoming information. Then the data is grouped by categories, and event correlation is determined. This information is enough to make the conclusions and trace the cause and effect relations. The latter is critical when it comes to investigating cybersecurity incidents.
- Event notification is the least extensive procedure, as it simply supposes a certain manner of notifications about the predefined events. The way and the cases where these notifications are sent are set during the SIEM deployment in the protected network. These alerts are serving as markers for the cybersecurity team about where they should pay attention .
- Policies of actions is a list of predefined states of the controlled area in certain circumstances and the alarms and notifications that correspond to them. The analysts create so-called “profiles” that set how the environment looks and acts in a normal situation and during routine cybersecurity incidents. Policies are needed to make the SIEM able to define whether the system functions normally or is exposed to a hazard.
How does a SIEM work?
As you can see by the paragraphs above, the key function of SIEM is to gather and group the information about the things that happen in the environment. It is also able to provide advice on how to deal with potentially dangerous events, but these tips are more like a supplement than a recommendation. The cybersecurity team must make the decisions, and the exact SIEM can make only minor adjustments.
The standard algorithm of the SIEM work consists of the four steps above but with deviations according to the current situation. When nothing happens, the system is idling and passively monitoring the events. However, when something unusual happens - for example, a new user is connected to the network, or a workstation is rebooted at an unusual moment - SIEM starts working. It pays attention to the suspects, analyses the information, and, if something valuable is spotted, reports it to the cybersecurity team.
Security information and events management is not an autonomous cybersecurity process. It cannot protect your network when you’re away, as its general function is to journal and process the information. Most often, cybersecurity in corporations is provided by EDR/XDR solutions, and SIEM is a complementary system that eases the tracking of events.
Types of SIEM
By the form of implementation, SIEM can be divided into 3 categories - cloud, in-house and managed. Most of the other differences that may be used for classification are too minor and differ from one vendor to another.
Cloud SIEM, as you can suppose by its name, is a security information and event management system that bears on cloud computing. This variant became popular after the global spreading of cloud computing solutions in corporations. It gives the SIEM functionality with much less effort spent on the deployment. However, it is slightly less adjustable for the needs of each separate corporation. Another problem is the increased attack surface: the data collected and processed by the SIEM system may be leaked not only from the client company but also from the cloud service provider as well as intercepted on the way to the server. However, the flexibility of tariffs and no need to purchase and maintain the hardware makes it pretty attractive, especially for medium businesses.
In-home SIEM supposes implementation of the system on your own hardware and software. That provides maximum integration since, usually, the in-home model supposes the extended adaptation of the software for the needs of a certain company. Usually, such integration is opted for by the companies which use an all-encompassing protection measures that form a full-size security centre. Such an approach requires way more skilled specialists to take part and costs much more money but will be as effective as possible. The security center will provide the peak performance of all security solutions applied in the environment, and in particular, the security event and information management process.
Managed SIEM is a type of system that may be based on both in-home and cloud forms but with the help of an outsourced analyst team. The technology provider offers both the calculation power and the qualified staff who will make decisions, constantly or on-demand. This service is attractive for companies that lack the corresponding staff or do not want to hire additional personnel.
SIEM Evolution
Cybersecurity researchers define three stages of SIEM evolution that happened through time.
- In the first stage, which started in the security information and event management solutions were just a combination of SIM and SEM. Due to the absence of proper logging in most of the contemporary programs and operating systems, first-generation SIEMs were pretty restricted on their control area.
- The second generation of SIEM software featured some enhanced mechanisms for working with large arrays of data. The increased number of applications and environment elements covered by the solution boosted the data flow exponentially. Additionally, second-generation SIEMs paid more attention to the historical data - they became able to compare the current events with past logs.
- The latest, third generation, appeared as a concept in 2017, featured the UBA/UEBA functionality and SOAR additionally to classic SIEM functions. User behavior analytics and security information and event management systems are similar in their purpose but were aimed to track different areas of inner activities. Such a joint action increases the solution's efficiency and improves coverage. On the other hand, security orchestration and response solution is software that makes responding to any threat more convenient and fast. In conjunction with SIEM/UBA notifications, SOAR makes it possible to deal with threats in a miserable period.
Why do we need the SIEM tool?
SIEM is a great complement to the anti-malware protection that is already present in the corporate network. Although it can present the whole pack of information needed to monitor the network and understand the threats, it does not give any facilities for automated malware detection and removal. Moreover, without the XDR, SOAR, and UEBA, it is pretty hard to create any response at all - manual management of the security settings of a whole network is complicated even for a professional.
Using SIEM in cooperation with other security mechanisms will drastically increase the overall protection, as it raises awareness among cybersecurity personnel. Contrary to UBA, it will be effective even in small companies, as it does not concentrate on only users’ behavior . If you want your cybersecurity team to be aware of any little thing that goes beyond routine events - SIEM is what you need.
Frequently Asked Questions
There are three major problems in any cybersecurity system that lacks the SIEM - absence of proper content, time to react and information overload. Security information and event management system is offering the solution for all of them.
Absence of proper content is when the cybersecurity team finds it difficult to act because there is no relevant and easy-to-process information available. SIEM finds what is needed and makes it much easier to process. Information overload is a contrast point for the previous situation. When there is too much data floating around and there is no grouping for it, anyone will struggle to make a decision. Sorting and grouping functionality of SIEM allows to heavily mitigate this issue. Time to react is the problem that comes from the previous two. While having a massive information flow, or no flow at all, you will likely fail to react in a proper time frame. For cyberattacks, the momentum may last for just a few minutes. Solving the problems with structuring the data and giving the proper alarms sharply decreases the reaction time and increases the chances to deflect the attack.