
User Behavior Analytics
User behavior analytics, or UBA, is a cybersecurity process where the behavior of every user in the system is checked to detect unusual activities. Such operations are performed using special software solutions that log the behavior and may automatically analyze it. In particular, automated systems often feature AI-based analysis that makes it possible to detect potential threat actors automatically. Together with SIEM and a security solution like XDR or EDR, user behavior analytics form an enterprise-scale protection layer.
Why is behavioral analytics important?
One of the most dangerous and unpredictable types of cybersecurity threats for large corporations is an insider threat. While malware has a well-defined signature in its actions and files, users’ behavior is hard to track without a specific software solution. One may say UBA applications serve as heuristic analyzers for the employees and everyone who acts in the system. Once suspicious activity is spotted, the cybersecurity team receives a notification with information about the possibly malicious user.
The insider threat accounted for about 80% of all data leaks. The latter is not as dangerous and painful as the ransomware attack, for example, but still causes serious reputation losses. Moreover, leaking confidential documents for a corporation that cooperates with governmental organizations is very bad, as it may expose classified information. That’s why the UBA is almost obligatory for corporations that deal with valuable information.
Besides the insider threat, there could also be a common misuse of the privileges. It may happen accidentally but still lead to unwanted consequences. Once again, tracing why a certain action happened is a non-trivial task that is hard to complete without using the UBA. SIEM systems offer information about the activities without linking them to the users that originated them. This ability is exceptionally needed when researching cybersecurity incidents of any sort.
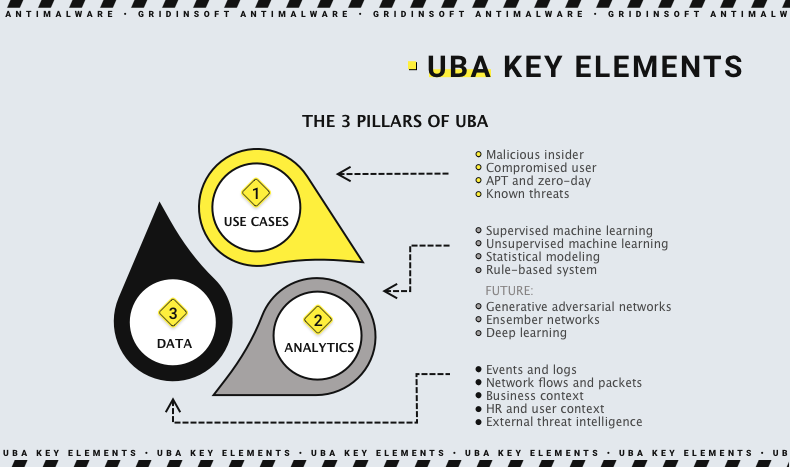
How does UBA work?
After being launched based on a corporate network, the UBA system performs an initial behavior analysis - to create the image of a typical user behavior. Then, this image is used as a reference when the analysis is performed. It pays attention to each user and their activities on workstations, devices they use in the network, shared directories, and applications. Additional attention is paid to the users with increased privileges, as they can reach the places others can’t. Then, the system calculates the deviation from what is considered normal and creates a report where all points of concern are specified.
UBA applications
Aside from cybersecurity, UBA-like systems also appeared in industries that rely upon information about users’ behavior as well.
- Online commerce effectively uses UBA to uncover user preferences and their typical interactions with the interface. That makes market analysis easier and helps the company improve the user interface if something does not meet users' wishes. Most often, trades will additionally be recommended to users, improving the targeted ads.
- Gaming platforms apply user behavior analytics to have a better understanding of users’ preferences. That makes it possible for them to make corresponding changes in the user interface.
- Program developers found UBA useful in understanding the user experience of their product usage. The more extensive view they receive - the more relevant changes will appear in the upcoming releases. Moreover, it also helps to find and fix bugs.
What is UEBA?
User and Entity Behavior analysis is almost synonymous with UBA since, these days, they have the same functionality. Earlier, UEBA was distinguished as a security system that tracks the behavior of entities - , i.e., devices in the network. IoT elements, as well as some of the networking devices , may be compromised by hackers to exfiltrate the information from the network. UEBA can detect these devices' malicious behavior and report it to analysts.
Privacy issues and UBA
Like in the case of any system that tracks human behavior, there could be certain privacy concerns. Tracking what employees do during their workday is unpleasant, especially when talking about the systems some tech giants apply to track their employees' presence. However, the UBA concept does not suppose personal tracking - it records only the behavior that is valuable for cybersecurity analysis. Its conjunction with SIEM, EDR, XDR or any other cybersecurity solution may expand the range of recorded information. Still, it will likely never pay attention to what employee posts on Facebook from the workstation. The key points of application for UBA are network connections, removable drives, shared directories, and endpoints.
Why should companies use behavioral analytics?
As it was mentioned, UBA, as well as UEBA, is very effective at detecting the malicious behavior of any user or device in the network. That is likely the only practical and proactive way to mitigate or remove the insider threat. While malware-related threats are nailed by solutions like EDR or XDR, insider threats are pretty hard to deal with without a monitoring tool like the UBA. The combination of anti-malware software (in the form of EDR or regular anti-malware) and UBA/UEBA is a perfect way to have your corporation secured. However, it has not only advantages.
The key problem of any software combination is compatibility. Even though vendors ensure that their software has 100% compatibility with additional modules, problems may happen. Sometimes the promised compatibility may be reached only with the applications from the same vendor, and all third-party apps will integrate poorly if they can be integrated. The UEBA and EDR/XDR/SIEM may conflict with access rights, decisions on incidents, and notification policies. Additionally, unoptimized apps may lead to serious issues with hardware overload, which are just the other pain in the neck.
Another issue is the price of these combos. Having these apps separately may sometimes be pretty expensive, and opting for several things simultaneously may cost even more. The support (as a part of the SaaS form) of different programs will make the retention expensive enough to make it impossible to carry on by small companies. And overall, small organizations have no reason to use such a complex solution. UBA will have no application since when you have less than 100 employees (you do not have many unusual behaviors to track).
