
Computer Worm
Computer worm is a kind of malware that aims at destroying certain programs, or even the entire system, by damaging the files. Additionally, it replicates itself in a predetermined manner, and often aims at other computers in the network, if the ones are present. This kind of malicious software appeared long ago – among the first malware that was ever invented. An infamous Morris worm, appeared in 1988, was the first example of a successful worm - although it was naught on the payload. Its sole purpose was to spread its files through the university network. However, it was already enough to make contemporary systems sluggish, and create significant networking issues.
The evolution of malware led to the paradigm shift that created a huge demand on crimeware – malicious software that is created specifically for making money. Worms were forced to evolve and adapt. Their ability to precisely destroy certain program elements can still be on hand during cyberattack – worms are used to disable the security solutions and bare the vulnerabilities. The latter may be especially effective when the breach is patched manually, with some simple edits to the program files.
How do computer worms work?
Legacy computer worms – the ones that were widespread in the ‘00s – were making their way into your computer through the system and network exploits. The latter, actually, was used when a worm was attempting to get to the computer from another infected machine in the same network. Breaches in the programs, in particular the ones that make the privilege escalation possible, act as a way to start the malware on the first device.
Once injection happens, the worm starts its malicious activity. Older versions of this software had little to no precision, damaging and deleting all the files they could reach. In this way, malware was making certain programs barely usable, as they were showing you dozens of errors. If the worm had no limitations on damaging the system files, it could easily sever a couple and thus cause a BSOD. What’s even worse - it can damage a crucial file, which is needed for system loading, and you will see a blue screen on each boot attempt. Only system reinstallation will help in such a case.
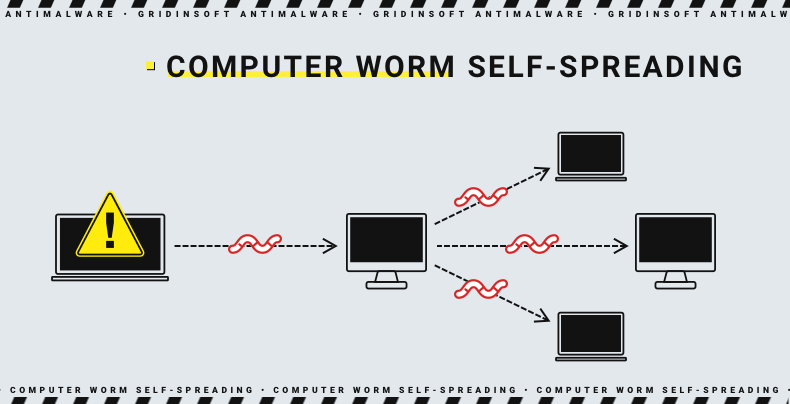
However, the described model is impossible to monetise. The first worms were rather vandal programs, whose purpose was just to create problems for a victim - no ransom, no advertisements or traffic arbitering. Modern computer worms have this problem solved – a payload trails along with the worm, which in this case acts as a locomotive that drags all the things in.
The payloads may be different – but most often choise is malware which has the fastest pay-off period. Crooks stop their choise upon things like ransomware, spyware, and so forth. Worms are appreciated fort their ability to spread themselves inside the network, which makes all other malware spreading efficient as well.
How do I know if my computer has a worm?
This malware type is not a stealthy one, since its sole purpose is to vandal files on your computer. Aimed or not, it will make the programs or certain system elements non-functional – and you will definitely notice it while using your PC. Furthermore, you may even experience system failures. If the worm is launched with high privileges, it can even damage the drivers and firmware, so the system will experience some large issues with even basic functionality.
In the case when worm was used to make the way for other malware, you will not likely distinguish the issues from different malware types. Once they are mixed, the last thing you’d want to do is try to launch different apps in order to determine their workability. Still, that is a pretty rare case when we talk about a stand-alone PC. That will not pay off the price of a worm and the ransomware affiliate’s commission, and there is no use for the key ability of a worm – self-spreading through the local network.
In any case, if you see the consequent failures of the applications, the overall slowness of the system, and hear the same complaints from the people who use the same LAN – it's definitely a worm. As it was also mentioned, this malware can jam the connection inside of the network, as it spams the requests to other machines, checking if they’re infected or not. But the best way to be sure about the nature of a strange behaviour of your PC is to use anti-malware software. A proper tool, like GridinSoft Anti-Malware, will be able to detect even the newest samples by its behaviour. That is a cost and time-saving solution that will make your life much easier.
Computer virus vs Computer worm - what is the difference?
Worms and viruses are the pioneers of the malware world. They’ve appeared at the dawn of a computer era, and both have some usage. Moreover, some of their properties are similar – that confuses some users who try to learn something on this topic. Let’s see the differences between computer worm and computer virus.
| Characteristics | Worm | Virus |
|---|---|---|
| Delivery methods | Email spam, malicious scripts, exploits | Adware banners, email spam |
| Way of action | Deleting the files or severing them by deleting their sections | Replicating itself into other programs and files |
| Abilities | Can infect devices in the LAN | Can make the program act as it wants |
| Effects | Programs failures, or the failure of an entire system | Program failures, rarely damage to the OS |
| Application | Targeted cyberattacks, ransomware/spyware deployment | Almost unused nowadays |
What damage can a computer worm cause?
Imagine having a large mechanism of gears, with several consequent branches. They are working perfectly and synchronously, outputting the power on a final gear. Then try to remove a random couple of gears from the inner parts of this chain. The entire branch will stop going, and the efficiency of the transmission will do as well. Another couple of parts – and you have cut the productivity in half. Worm acts the same – by detaching random elements of the programs you have, it blocks certain functions, or even breaks the app completely.
Since the worm can reach and delete any file type, it can hit precisely the thing which attacker needs. In particular, this ability is sometimes used to remove the security barriers created against exploiting the vulnerability in a used software. It can be both a hand-made solution, as well as an official patch, but the overall poorness of the bugfix makes it possible to revert the changes and use the breach as before.
Computer worm examples
Most of the examples of worm usage refer to old times, when this threat was more actual. Once malware became much more commercialised, worms evolved into quasi-locomotives that pull all other malware into the network. Still, the usage cases are so rare that there is almost no information in the network. So, let’s look at what is publicly available.
| Malware name | Date | Description |
|---|---|---|
| ILOVEYOU | May 2000 | Aimed at self-spreading through Outlook. Its file was named as LOVE-LETTER-FOR-YOU.TXT.vbs |
| Blaster | August 2003 | Was spreading through buffer overflow exploitation, displayed a message billy gates why do you make this possible ? Stop making money and fix your software!!. Additionally, forced the attacked systems to DDoS the Microsoft Update servers. |
| Mydoom | January 2004 | Was spread through a poorly-made email spam, but its massiveness made it one of the most spread worms. |
| Daprosy | July 2009 | Acted as a keylogger, was deleting the folders that contained .exe files. Performed mass mailing for self-spreading |
| Stuxnet | June 2010 | According to the rumours, a US government-backed worm, targeted on Iranian companies related to the nuclear program. In particular, it was aiming at supervisory control and data acquisition systems (SCADA). |
