What is SmokeLoader?
SmokeLoader is a backdoor-type malware that can act as a tool for remote access, malware downloader and data stealing tool. Appeared back in 2014, it is generally used to establish botnets which were then exploited for DDoS-attacks and additional malware delivery. For the approach it uses to deploy other payloads, it was classified as a worm by some analysts. Overall, even in 2026 it remains a major threat for both companies and single users. Its design features allow it to act stealthy and be invisible and invincible to antivirus programs.
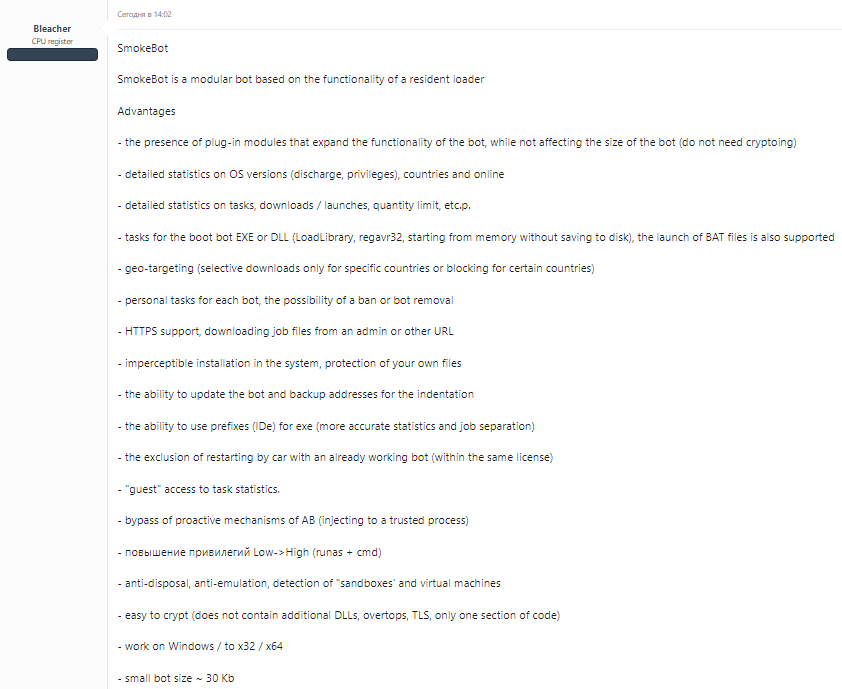
Among key features of SmokeLoader is its immense obfuscation and the choice of C/Assembly as programming language. For the price of $1650, a buyer receives malware and admin panel. Additional plug-in modules can be delivered after the initial injection, but are available for a separate payment. Such a modularity makes this malware way smaller than its counterparts – only 30KB, while most backdoors typically have a size around 150-200KB. Developers of this backdoor usually release an update 1 time a year, bringing new features and modules.
Malware description
SmokeLoader is a typical example of backdoor malware which, however, has an orientation on malware delivery by its design. It contains botnet creation capabilities as well, which allows the infected computers to serve the commands sent from the command server. Because of a constant development and the flexibility of a chosen model, malware accreted with up to nine modules. The latter extends SmokeLoader functionality to create a remote access to the infected systems, grab passwords, keystrokes and redirect the traffic through spoofed DNS requests.
Another specific moment related to SmokeLoader backdoor is the way it is coded. First and foremost, low-level langs like Asm are rarely used for malware creation, though C is met quite often. Deeply obfuscated and encrypted, the code remains unreadable even during the malware execution. Once it needs to perform another API call, it encrypts the part it stopped using and deciphers the one it needs. Such an approach provides strong security against reverse engineering, but the execution generally takes longer than usual.
The payload this malware delivers to a target device does not contain a PE header, thus cannot be executed in a regular way. That confuses some of the antiviruses that consider it a broken file and therefore ignore it. To make itself running and provide persistence, it hollows the code into a system process, and enumerates the DLL locations in order to be able to use them when needed.
SmokeLoader distribution
To have a clear understanding of how malware works, it is important to see how things happen chronologically. The way malware gets to the target machine is always the first step of any infection – so we’ll review it first.
SmokeLoader backdoor is known for being used in a wide range of propagation ways. Its high price does not stand in the way of its popularity, so a lot of different cybercrime groups use it to fulfil their needs. For that reason, actually, this backdoor is seen to be spread in an enormously wide variety of approaches. Email spam, drive-by downloads, exploit landing pages, delivery by dropper malware and even within the unlicensed software – all these ways serve for SmokeLoader delivery.
It targets both individuals and corporations, hence in the case of former malware will most likely get in through cracked programs and drive-by downloads. Email spam serves for both parts simultaneously, while exploit sites and downloader viruses preferrably do their job in attacks against corporations. Most common among them, as you can guess, is spam emails — an absolute alpha and omega of malware spreading. In that case, SmokeLoader is loaded with the help of a malicious macro hidden in the document.
Disguise of a cracked app, hacktool or a questionable utility supposes the use of a script that will be executed as soon as you run the app installer. The outcome is pretty much the same – malware connects to a command server and pulls the payload. But the underlying mechanism is different: instead of exploiting vulnerabilities in macros, it receives admin privileges while posing as a part of installing app.
Exploit landing is a completely different story, as it supposes the use of an existing and unfixed browser vulnerability. Key trick there is to lure the victim to open this page. Exploitation toolkit will use the mentioned breach to inject malicious code into the browser and force it to execute that code. As a result, malware is getting installed without any interaction from the victim.
Smokeloader launch
SmokeLoader backdoor uses 2-stage unpacking that makes it possible to hide malware from detection as long as possible. Stage 1 contains a deeply packed and obfuscated malware that is about to be decrypted after passing the checkups. Stage 2, on the other hand, is a ready-to-run malware which, however, has certain specific details to describe.
Key information about the SmokeLoader at an early stage of its activity is the fact it makes a large number of check-ups. They are related to detecting if the execution environment is a virtual machine, sandbox or a debug tool. If such is detected, it exits the execution process. Another check-up that is hardcoded into the malware is location review. If it detects that the attacked system is somewhere from ex-USSR countries, it exits the execution as well. The peculiar moment is that you can’t disable this restriction by any means, so that’s possibly dictated by the origins of malware developers.
During the process of checkups we mentioned above malware loads several DLLs it needs for execution. Kernel32.dll and User32.dll are started first, then Shell32.dll and Advapi32.dll are loaded. Additionally, it copies nt.dll – yet another core Windows library – to a %Temp% folder. After that, it runs only this instance of the library. Such an action is likely done to avoid detection from EDR/XDR systems, that generally control apps that access the genuine nt.dll instance. If all checkups we mentioned above are passed, and DLLs are loaded flawlessly, malware checks the system architecture and then deploys the corresponding payload version – 32-bit or 64-bit.
Stage 1 execution
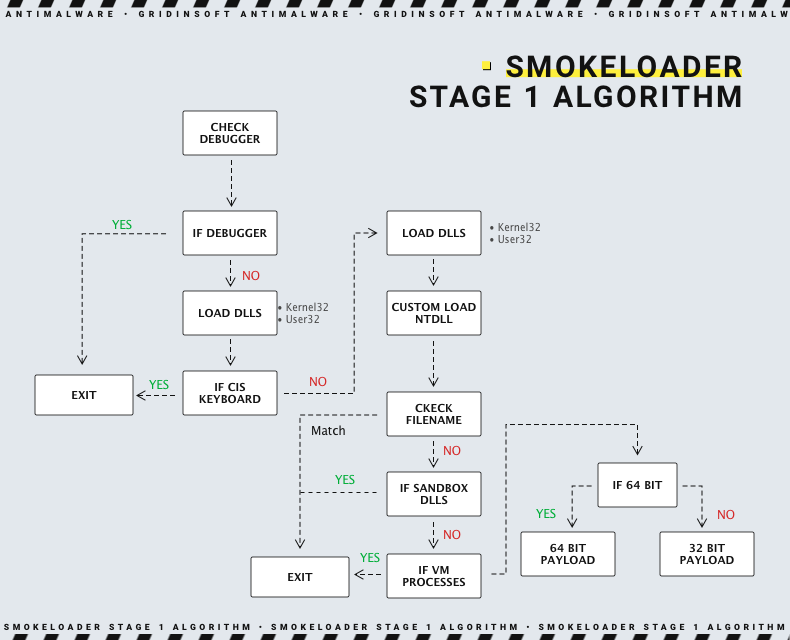
It is pretty hard to analyse the SmokeLoader’s Stage 1 payload, primarily because of the heavy obfuscation. It uses opaque predicate technique, which simply confuses any attempts to understand what the program is trying to do. Solving those predicates is not productive, leaving them be is either, as malware hides actual code rows amidst the spare opaque predictions. Still, it is possible to solve that problem through using scripts created specifically for that purpose, or with a special settings of the analysis tool.
Code encryption in SmokeLoader is implemented in a pretty strange manner. Almost 80% of the code is held encoded on a continuous basis, using LZSA algorithm. If the code from the encrypted part is needed, malware gets the size of a part it needs to decode, decodes it, gets the function, and ciphers back every other element, including the instructions it stopped using. Therefore, readable code parts are stored exclusively in RAM, while on disks you will see just a packed code. Moreover, there is no way to catch the snapshot where malware holds a significant part of its code decrypted.
After passing the checkups we mentioned above, SmokeLoader decompresses and unpacks its core and finally gets to the stage where it executes its main purpose – remote access and malware delivery.
Stage 2 execution
First noticeable thing about the SmokeLoader after its unpacking is the fact its final form does not have a PE header. Without that, Windows simply does not recognize the program as a valid executable file. At that point, it poses as a Shell code. That acts both for and against malware: making its detection harder, it also lacks the ability to use normal Windows functionality for programs launching. If succeeded, however, malware runs smoothly as nothing differs it from a regular executable file.

For that reason, SmokeLoader manages to get into other processes through the procedure called code hollowing. Using a row of system calls – GetShellWindow->GetWindowThreadProcessId->NtOpenProcess – malware manages to embed its code to a genuine Windows process. Usually, it choses explorer.exe as its carrier – the headstone of Windows as it is.
Key functionality stored in the final stage is communication with the C&C server and payloads delivery. To make these functions work, however, SmokeLoader also needs to find a way to call for the DLLs vital for its execution. To deal with that task, malware exploits an internal Windows structure, called Process Environment Block, or PEB. This thing contains the LBR field that contains all libraries that are currently running in the system. Knowing that, malware can choose from a list of already running libraries, thus resolving its dependencies takes much less effort. It saves the 4-bit hash of a DLL address to its own structure, so there is no problem with calling it when needed.
To run, SmokeLoader needs the following libraries loaded:
- User32.dll
- Advapi.dll
- Ole32.dll
- Winhttp.dll
- Dnsapi.dll
Keep in mind that it already loaded several DLLs during the stage 1 runtime. Therefore, the full list of libs it needs is more extensive. Overall, the DLLs it looks for at the stage 2 are generally needed to establish connection to the command and control server. But before getting to its final tasks, malware also starts 2 threads in order to see if there are any debug or malware analysis tools running in the system. SmokeLoader searches for a list of processes and window names. If there’s a match, malware recognizes the attempt to analyse its activity and stops execution.
- Procmon.exe
- X64dbg.exe
- X32dbg.exe
- Procexp.exe
- Procexp64.exe
- Autoruns.exe
- Ollydbg.exe
- Wireshark.exe
- ProcessHacker.exe
C2 communication
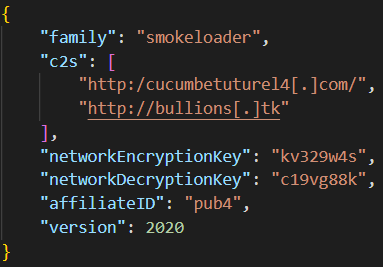
After all this extensive unpacking processes and checkups for the possible analysis, SmokeLoader finally comes to communication with C&C. It does this operation using the configuration blob that is built into each sample. Each one contains up to 10 IPs of command servers. Same config also contains a decryption key for incoming and outgoing packages.
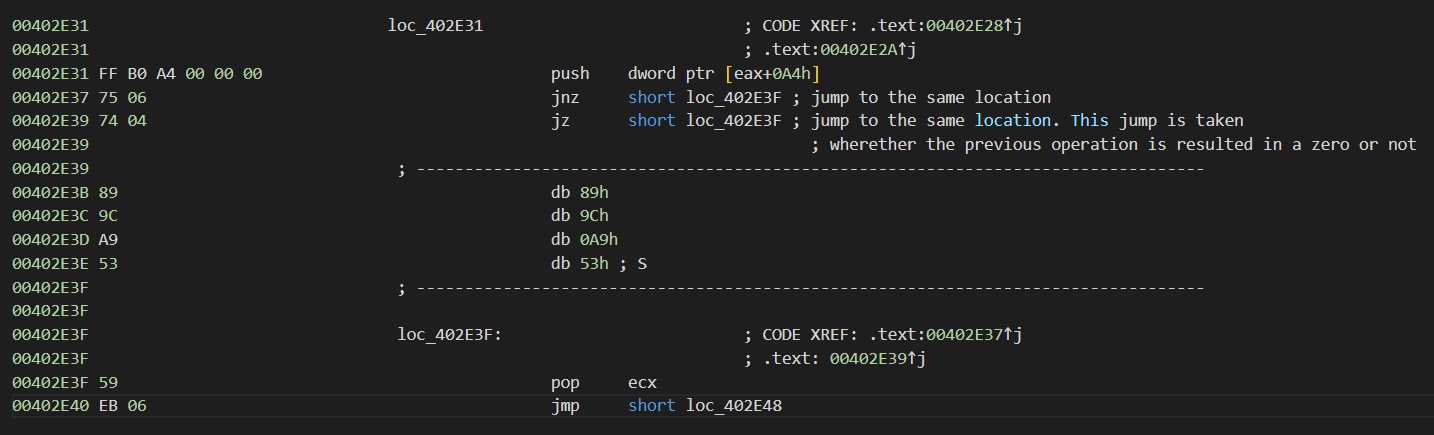
Despite being a dropper rather than infostealer, it still gathers certain information about the system it is launched in. That is needed simply to fingerprint the machine – and then distinguish from others in the botnet. Malware sends the following data categories to the command and control server:
- Bot ID (41-bit value, mix of digits and letters)
- Affiliate ID
- Malware version (repeats the year of release)
- Machine name
- Windows version
- Level of user privileges
Some parameters, in particular, bot ID and affiliate ID, are important to weed out random connections from bots that belong to other masters. Same does malware version – if it does not match with the one held in the admin panel, all packages from this bot will be considered invalid.
From the C2 server, the malware master can send only 3 commands to the malware. “U” command launches the updating process of the bot on the chosen machine(s). “R” (probably goes from “remove”) forces the bot to perform self-destruction. “I” command, at last, asks the malware to install persistence.
Malware delivery
As we mentioned above for multiple times, SmokeLoader’s key purpose is to download malware to the infected machines. Therefore, a botnet of hundreds of machines may simultaneously receive a pack of several different malware samples, depending on who pays the botnet master. Such behaviour led to the situation where all computers present in the botnet were infected dozens of times by a wide variety of malicious software. Still, that doesn't restrict crooks from keeping these vacant places for sale. The possibility of such a choice makes the affiliates free to spread whatever they want. Among typical types of malware are banking trojans, spyware and ransomware.
There is also a strange cooperation between SmokeLoader and STOP/Djvu ransomware. Instead of a regular malware delivery, backdoor is delivered along with ransomware and a couple of other malicious things – RedLine Stealer and Vidar Spyware. All of them are likely added by Djvu ransomware threat actors, in order to increase the margin of a single attack.
Additional modules
We mentioned that SmokeLoader developers also offer 9 extension modules for their malware. These modules extend the backdoor capabilities and make it pretty similar to spyware threats. Modules are not included in the basic supply, so each module is about to be additionally paid, over $1650 of the initial price. Here are 9 extensions available along with the backdoor:
| File searching tool | Finds the files of specified extensions or names |
| Procmon | Process monitoring tool, allows to list the programs in the system |
| Remote PC | Allows malware master to remotely connect to the infected PC, like with a classic remote access utility |
| Keylogger | Logs the keystrokes |
| Email grabber | Scans the system for MS Outlook address book and grabs it |
| Form grabber | Scans the windows for login forms and grabs everything that gets into the form |
| Password sniffer | Scans the Internet packages for login credentials |
| DDoS | Creates the environment on admin panel for controlling the botnet and forces infected systems to attack designated servers |
| Fake DNS | Spoofs the returns of DNS requests, making it possible to redirect the victim to the site you need |
SmokeLoader Backdoor IoC in 2026
| Trojan.Win32.SmokeLoader.bot | a7f605d4110bba430e02c7c5240e656fb3f1dd7f02dce985e9e5677169c9de55 |
| Trojan.Win32.SmokeLoader.bot | cc58ad1f7a097f077f06b78e21c1f5a01007cd98613b602bb22b95751920ba80 |
| Trojan.Win32.SmokeLoader.bot | 143310670009099214b1b1a812e98a485db3e2879ab35dca8ba63005a62a610c |
| Trojan.Win32.SmokeLoader.bot | 109d9077e847550b471e717986dec00400d4a49cccf438a462ec9630eda654c5 |
| Trojan.Win32.SmokeLoader.bot | 0c1f4caa4168d458ffedcd65213253b42d972964ea78d042d4c560d8a71973bc |
C2 URLs:
| monsutiur4[.]com | nusurionuy5ff[.]at | moroitomo4[.]net | susuerulianita1[.]net |
| cucumbetuturel4[.]com | samnutu11nuli[.]com | host-file-host6[.]com | host-host-file8[.]com |
| nikogminut88[.]at | limo00ruling[.]org | mini55tunul[.]com | tootoo[.]ga |
| eyecosl[.]ga | bullions[.]tk | mizangs[.]tw | fiskahlilian16[.]top |
| paishancho17[.]top | ydiannetter18[.]top | azarehanelle19[.]top | quericeriant20[.]top |
| xpowebs[.]ga | nunuslushau[.]com | linislominyt11[.]at | luxulixionus[.]net |
| lilisjjoer44[.]com | venis[.]ml | mbologwuholing[.]co[.]ug | quadoil[.]ru |
IP addresses
| 5[.]149[.]253[.]100 | 185[.]117[.]88[.]96 | 185[.]174[.]173[.]34 | 162[.]247[.]155[.]114 |
| 185[.]174[.]173[.]116 | 185[.]174[.]173[.]241 | 62[.]109[.]26[.]121 | 185[.]68[.]93[.]27 |
| 137[.]74[.]151[.]148 | 185[.]223[.]95[.]66 | 85[.]143[.]221[.]60 | 195[.]123[.]216[.]115 |
| 94[.]103[.]82[.]216 | 185[.]20[.]187[.]13 | 185[.]242[.]179[.]118 | 62[.]109[.]26[.]208 |
| 213[.]183[.]51[.]54 | 62[.]109[.]24[.]176 | 62[.]109[.]27[.]196 | 185[.]174[.]174[.]156 |
| 37[.]230[.]112[.]146 | 185[.]174[.]174[.]72 | 65[.]55[.]252[.]93 |
How to protect yourself from SmokeLoader Backdoor?
Backdoors are extremely sneaky malware, which are pretty hard to detect once they’re in the system. SmokeLoader is a tough nut even compared to other backdoors. Its anti-detection and anti-analysis measures make it a hard target for protection systems like EDR or XDR. Hence, preventing its appearance is first and foremost of what you should do.
- Use software for file-based attacks prevention. Most of modern cyberattacks rely upon slipping malware through files on a certain stage. That’s why the best prevention approach should aim at making that impossible. Software solutions like Content Disarm and Reconstruction can effectively defuse malware or malicious scripts that lay deep in documents and files that arrive at your system. Of course, this way to solve the problem is more about corporate security.
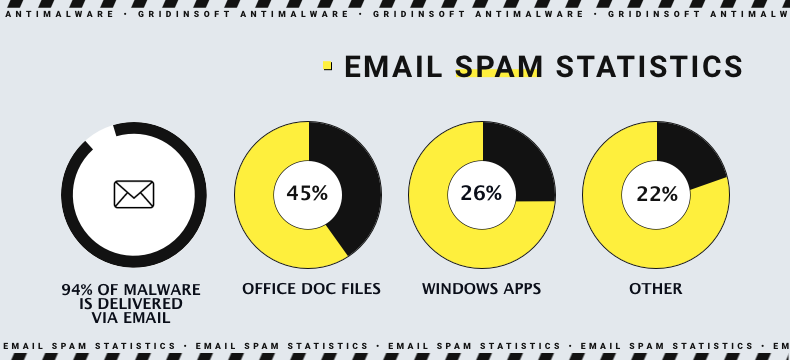
- Be careful with emails. The main source of malicious links and infected documents is email spam – the statistics of the last 3 years gives no chance to doubt that. Contrary to CDR systems we mentioned above, simple attention is available to anyone. Don’t hurry to open all emails you receive, especially ones that are controversial to what you are going to receive. Thoroughly review the sender’s address and message body to see any mistakes. Depersonalisation and false statements are common signs of a spam email. Attached files is not a common form of sharing information, so they are not recommended to open as well.
- Do not use cracked software. Cracked programs are another widespread source of problems, despite touching generally individual users. Malware sits in the installation file, or sometimes even substitutes the exact program at all. In combination with the request to disable the antivirus program (as it typically starts cutting up rough at modified program files) it makes software cracks a loved tool of different categories of crooks. Moreover, such approach at software usage is illegal, thus you can face legal actions – up to imprisonment.
- Keep an eye on the links you follow. Wherever you find them – in the aforementioned emails, on the websites you browse or in social media, they should not be trusted blindly. Your special attention should be paid to links that lead to pages built on site constructors, or a cheap top-level domain. Their price and ability to be rented with no papers makes them a crooks’ delight candy. For sure, such attention is not needed when you’re sure of both the target site and a person who gives you that link. But all other cases should be checked at least with attention.
However, proactive measures are not all you can do to remain secure. There are also a couple of things that will throw a monkey wrench into infection flow.
- Use network monitors. Malware that fails to connect command and control server is pretty much useless, or at least less dangerous. SmokeLoader, for instance, will not pose any danger if it cannot get through the network monitoring tool to connect the command server. You may opt for both full-fledged Network Detection and Response systems, if you aim at securing the corporate network, or simple firewall apps – if your target is your own system.
- Apply using security tools that feature advanced detection systems. SmokeLoader is not unique in the way it hides its presence and files. Unfortunately, low-grade antivirus software simply cannot detect malware under such a deep disguise. If you want to have proper protection against such cunning malware, use anti-malware software that has advanced detection capabilities. GridinSoft Anti-Malware, for example, can deal with malware using three different systems, that evaluate the events that happen in the system from different points of view.