What Is CDR?
Content Disarm and Reconstruction system is a specific type of security application that aims at dealing with threats incorporated into genuine files. It uses a specific approach to analyse the files and detect threats inside, if the ones are present. Afterwards, it removes the threat and reassembles the initial file while keeping its benevolent contents unchanged. This, however, is a simplified explanation of how CDR can work. Depending on its type, the way it mitigates the threat may differ from extracting malicious code to making it impossible to execute.
Key point of CDR application is file-based attacks. They include malware that is embedded into MS Office documents, printed document files (PDF) and other ones that should not contain any executable code. They may arrive at the perimeter as a file or in the archive; methods of delivery commonly include LAN, email messages and removable drives. Over the last years, attackers began heavily relying on email phishing as a way of gaining initial access to a corporate network. Other approaches include an insider job, who is supposed to deliver the infected file into the network. These are the best example of file-based attacks, and simultaneously the main battlefield of Content Disarm and Reconstruction systems. Key types of threats this system is called to deal with usually come from the network.
How does CDR work?
Imagine a procedure of a suitcase X-ray checkup in the airport. On the resulting image, any metal elements, or ones that have higher resistance to the X-rays will strike the eyes even for someone who never worked with such equipment. Once something that looks suspicious is detected, airport security staff will ask you to open the case and show them this item. If this thing is forbidden from carrying onboard, it will be taken away from you. CDR does pretty much the same, but with the documents that arrive to the network in any form.
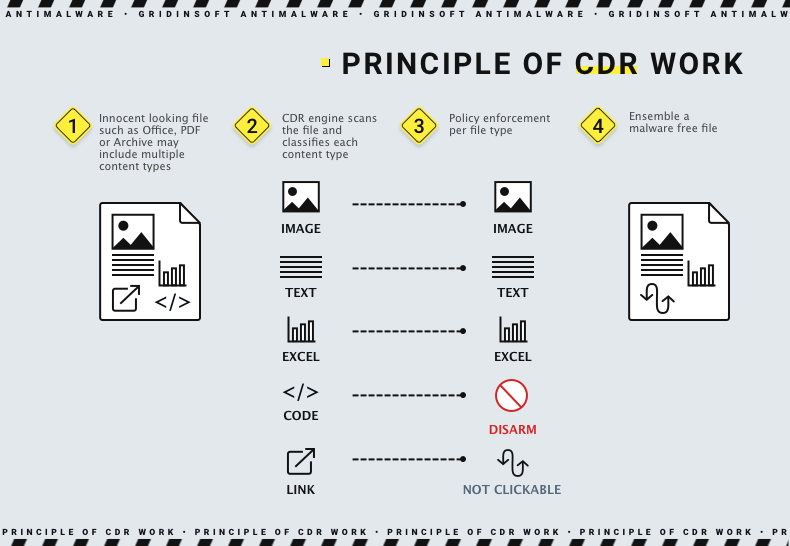
The Content Disarm and Reconstruction system thoroughly examines each document type that meets its checklist requirements. It searches for potentially dangerous elements that may be misused with malicious intentions. Those could be MS Office macros, executable code embedded into a PDF file, calls through the MS Office elements like Equation Editor, and so on. After detecting such a thing, CDR will apply the actions depending on its type.
- Type 1 converts the file to a naught PDF, a so-called flattened file. It is completely safe, as the original file does not exist anymore, and all you get is its contents you cannot interact with. The resulting file has nothing executable – only a picture. Such a tactic suits the cases when you need only the content of the file, and will not edit or interact with it by any means.
- Type 2 removes any kind of active content, regardless if it is clear or malicious. The exact file, however, is kept, and you can access it in the original form. In that case, a user retains the ability to interact with the file contents. That works great unless the file contains elements that can potentially be used for malicious purposes, but they were present with clearly benevolent intentions in that case.
- Type 3 reassembles the file trying to keep all the functional parts together. Meanwhile, it excises the parts that may be potentially dangerous. Such a practice requires a detection system since the program should be able to distinguish between good and bad elements. But the result is more promising than in other cases – malware is defused, and you can interact with the file as you should, with no restrictions.
After these operations, the files are returned to the end user. If the file(s) was delivered as archive, CDR will generally keep them compressed. Type 3 systems may also run the file in a sandbox, if there are any doubts on its possible functionality.
Why is CDR needed?
Over the previous decade, the use of paper documents rapidly decreased. More and more companies, even small ones, switched to electronic document flow. That includes not only in-company deeds, but also all incoming and outgoing correspondence. Paper documents had their vulnerabilities as well, but these days, potential hazards from email messages surpass them many times. Nowadays, email phishing is involved in over 60% of all cyberattacks, that include spyware, ransomware, and other nasty things. Messages may look, or even be legit – but infected with malware by a threat actor. Multi-stage malware attacks that include insider jobs or using the compromised computer from the inside of a network are one of the hardest to mirror.
CDR systems are a perfect way to mitigate the risk. It is not a stand-alone protection system, sure, as it cannot deal with other ways of malware injection. EDR, XDR and other examples of a next-generation antivirus tool are on duty for this. However, they can only block the entire malignant item, together with the exact document. Content Disarm and Reconstruction solves this issue, offering the ability to actually see the contents of this message and share it further, without the risk of infecting someone else.
Benefits of CDR system
Despite being an auxiliary system to the overall cybersecurity setup, it has some design features that allow it to be as effective as others, at least within its trade.
- Concept-level zero-trust. CDR systems that imply flattening the file or excluding all active content do not pay attention to the trust rating of certain components. If it can be used for malignant purposes – it will be excised, with no excuses. That makes ineffective the use of previously untouched programs for malware injection.
- Zero-day protection. The previous paragraph implies that even if crooks will manage to discover and exploit the vulnerabilities in the programs that are considered safe, there will be no chance to succeed with infecting. That drastically increases the probability of preventing zero-day vulnerability exploitation.
- Minimal system impact. The aforementioned NGAV-class solutions usually require a separate hardware – just to isolate computers and endpoints from excessive calculations. CDR, on the other hand, may be mounted on regular workstations without a risk of performance degradation.
- Access to the original file. The solutions that actively detect threatening elements keep safe parts of a document intact. That may be extremely useful not only to its direct receivers, but also to cybersecurity personnel who may further analyse the contents of the file. The latter is useful for understanding the possible ways of disguising the phishing letter.
Flaws of Content Disarm and Reconstruction
There are no roses without thorns. Being effective at its key purposes, CDR also features a couple of unpleasant side-effects and design flaws that are generally hard to deal with.
- Response times. Once CDR takes over the document, it may take some time to analyse it and apply the corresponding actions. In some cases this time may elapse to minutes, making you wait even if this correspondence is urgent.
- False detections. As we noted in the description of Type 1 and Type 2 CDRs, the operations this system performs may cut off not only malicious content, but any executable element. Therefore, useful integrations that imply using macros, in-document links and so forth, will not be available. It cannot be called a classic false positive detection, but may still seriously dilute the functionality these documents originally carry.
- Lack of independence. Having solely a CDR system running does not mean that you can forget about the threats. It concentrates generally on the documents that come from emails, removable drives or local area networks. All other malware infiltration methods remain out of its sight.
Do I need a CDR?
Any choice of an auxiliary security software is your own decision. Content Disarm and Reconstruction is the same useful addition as IAM, User Behaviour Analysis or SIEM. But contrary to the mentioned systems, CDR will be as effective in small companies as it is in large ones. Pretty much every company deals with a considerable amount of files sent via email or in the local network. They can be checked manually as well, though, it will never be as effective, safe and fast as a check-up by a specialised system.
If you have a full-fledged protection system established, and are thinking of extending its functionality, CDR is definitely worth your attention. A lot of EDR/XDR/MDR developers have such systems on offer as an addition to the main course, so you may probably find the one which will natively integrate into your security system. Overall, CDR is especially recommended for application in large companies. They are under constant risk of cyberattacks, and naturally deal with numerous documents that arrive from various sources.